Got nothing witty or smart to open with so, this weekend we hunt for Sliver C2!
Sliver is an open-source cross-platform adversary emulation/red team framework, essentially a Command & Control (C2) framework written in Go. It was developed by Bishop Fox and released publicly in 2019 and immediately adopted by malicious actors.
Before we start our hunt, it’s important to identify a few distinct characteristics.
Sliver's key ports:
443: Default HTTPS C2 communication with implants
80: HTTP C2
8080: Also used for HTTP C2 traffic
8888: Common alternative HTTP C2 port
31337: Default multiplayer server port
1337: Alternate multiplayer listener
And you probably need 22 to log into the machine
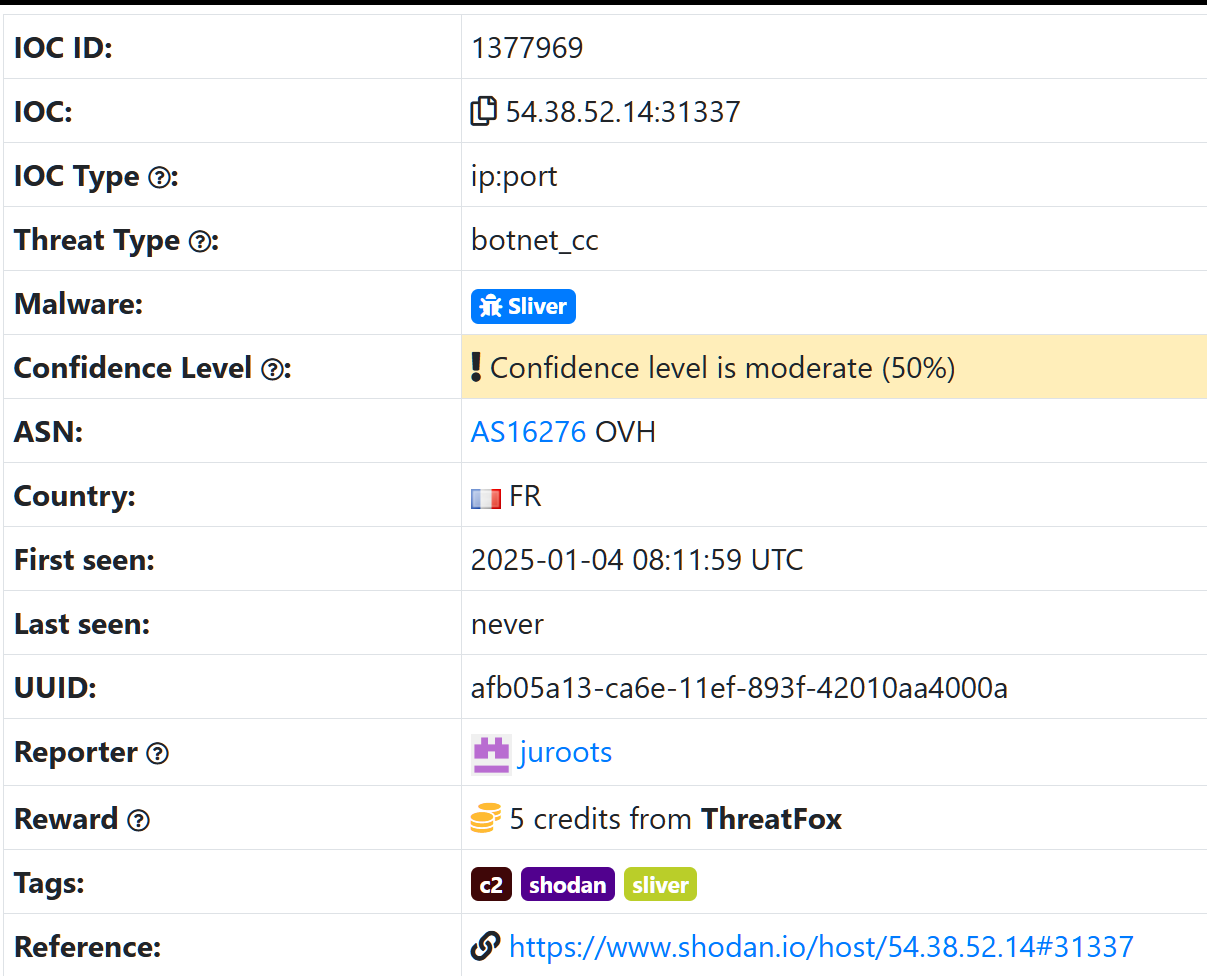
Our starting point is the IP 54.38[.]52.14
Hunt Methodology
At this point, let me make a quick note on the importance of using multiple platforms. This IP does not return the same results on Shodan and Censys.
Shodan for example lists port 31337 while Censys does not, that also helps us understand that creating a hunt rule using a port might not be the best way forward.
Earlier we established that port 31337 is used as the default multiplayer port. Now, reviewing the certificate reveals a couple of potential pivot points, the common names used.
Using that as a pivot point leads to 475 results, however as we mentioned above, it’s good to always get another approach.
ssl:"CN=operators" ssl:"CN=multiplayer"For a different approach let’s move over to Censys. In order to have solid pivots we need to rely on parameters that are hard to change. One such parameter is the JA3S Fingerprint.
The fingerprint is created by capturing the TLS version, Cipher and Server Hello parameters, this is a good pivot point because it’s very hard to modify those values without changing the source code. So let’s combine what we have so far and run a query on Censys, we will use the JA3S found on Censys and the common names we identified before as a pivot point.
services.tls.ja3s: 475c9302dc42b2751db9edcac3b74891 AND services.tls.certificates.leaf_data.subject_dn="CN=multiplayer"Analysis
Success! We have 242 results matching our search criteria, as you can see, some instances might not use the default ports and run the multiplayers on custom ports.
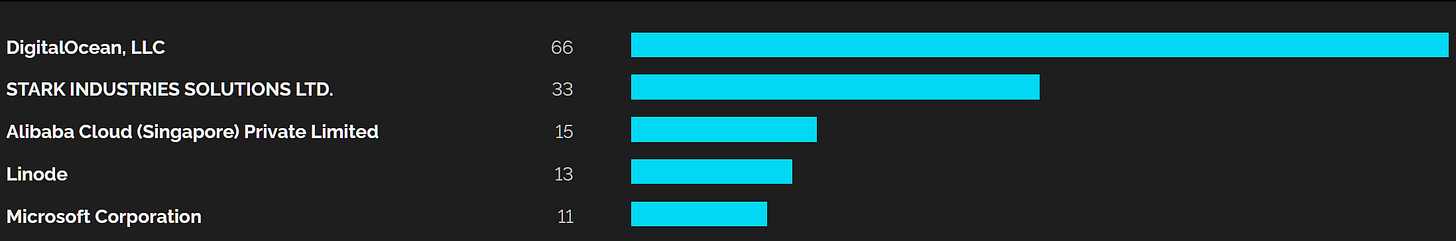
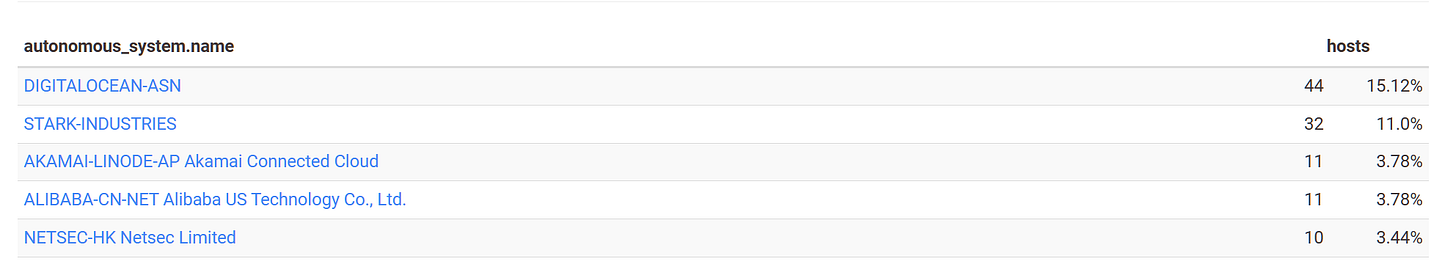
Alright, now that we have results from 2 different sources, let’s cross reference the findings, clean up, do some grouping and get the IPs.
It immediately stands out that the biggest clusters are common between the two platforms.
Furthermore, after analysing some of the findings I noticed that a group of 24 hosts shared the same SSH fingerprint, the group is hosted on Stark Industries AS44477 an organization known to be naughty which leads me to believe that this is a cluster deployed by the same actor. Following up on that pivot didn’t lead anywhere so for now I am going to leave it here.
And there you have it, a short overview on how to find Sliver deployments. Keep in mind that the tool is also used for legitimate purposes as well so not all IPs associated with this are going to be malicious, I’ll just share the list as part of the findings not necessarily as IoC.
Finally, this is just one of many ways you can look for Sliver C2, for example both Censys and Shodan offer search by tag but some instances might get omitted and also it would make for a very short post.
Thanks a lot for all the support and kind words over the last few months! Hope you are all doing well. I’ll close this with what I think was one of the best messages of 2024, it’s from Pavel Durov of Telegram