Bad Stark!
The cybercriminal's playground
A couple of weeks ago, I was wondering why Stark-Industries Solutions a bulletproof hosting (BPH) known to facilitate all sorts of malicious activity from hacktivism to nation state espionage, was not blocked/blacklisted at autonomous system (AS) level. A few people were kind enough to provide some insight and point me to additional reading.
One article that caught my attention was a posted by team cymru on August 13, in which they stated the following.
This had my gears spinning, so I wanted to check on recent abuse reports and malicious references that originated from the AS44477, owned by Stark Industries.
Read the following line in Jack Bauer’s voice
“The following takes place between August 13th and September 15th.”
I used a combination of open source tools and commercial threat intelligence platforms (TIP) to get a rough idea of the amount of events I am looking at and the results were discouraging for a one man analysis. I found around 800 Stark IPs related with cybercrime in one month period (Aug 13 - Sep15). In comparison, using the same search criteria, I got more than 1K results between July 13 - Aug 13.
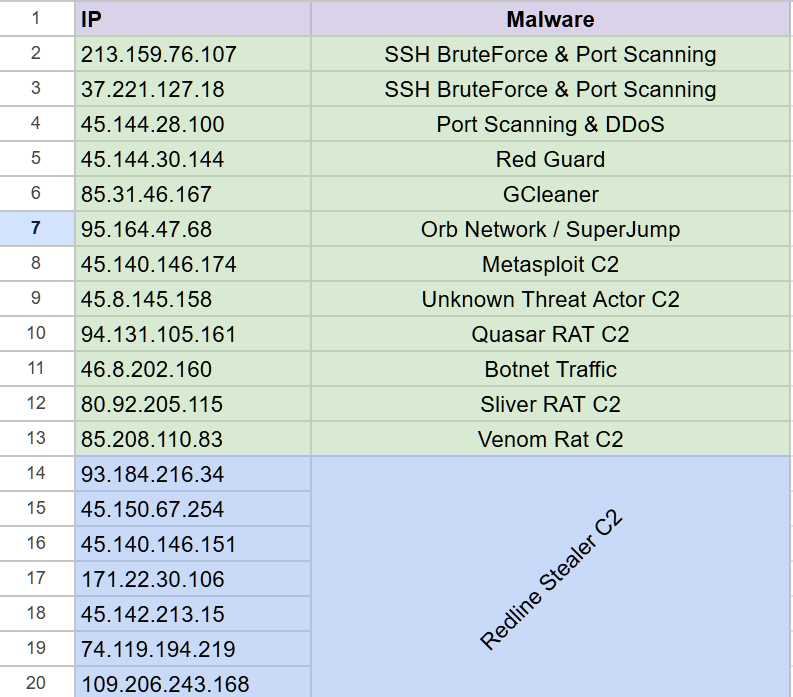
Since I couldn’t fall down the rabbit hole and follow all of the findings I sampled a few events from different dates. (Can’t create or upload a table so here is a screenshot)
As you can see, multiple IPs from different ranges are associated with various malware with RedLine Stealer being the prevalent malware.
The most interesting discovery, for me, was the entry regarding ORB networks.
Findings Overview
SuperJump | Orb Networks
Operational Relay Box (ORB) networks, function as proxy networks, combine compromised devices such as outdated routers and IoT devices with virtual private servers (VPS). This hybrid infrastructure allows attackers to relay malicious traffic and mask the origins of their attacks, making detection and attribution significantly harder for defenders.
Notably, ORB networks like SPACEHOP (ORB3) have been used by groups like APT5 and APT15 for reconnaissance and exploiting vulnerabilities. These networks can continuously morph and expand, increasing their stealth by cycling through compromised nodes. For example, in 2022, SPACEHOP facilitated the exploitation of a critical Citrix vulnerability, which was linked to APT5.
What makes ORB networks particularly concerning is their ability to render traditional Indicators of Compromise (IoCs) irrelevant. Since these networks frequently rotate compromised nodes, attackers can evade detection that relies on static IoC.
I found ORB networks fascinating and I will probably follow up on this, trying to identify Stark IPs that are part of such networks.
RedLine Stealer
First appeared around March 2020 is an information stealer written in C#, used to steal credentials and other information such as cryptocurrency wallet files. Various actors use RedLine and it’s commonly delivered via phishing campaigns and exploit kits. Different executions have been observed as some threat actors load it into memory while others drop it directly to disk, the exfiltration of data is via HTTP.
Venom RAT
A remote access trojan first observed in late 2022, it combines infostealer capabilities with keylogging, remote access as well as disabling user account control.
Sliver
A Golang-based post-exploitation framework developed by Bishop Fox, used as an alternative to Cobalt Strike, it facilitates C2 functionalities, utilizing various communication protocols like HTTP(S) and DNS.
Quasar RAT
Active since 2014, a remote access trojan written in .NET used by a variety of attackers, used in recent campaigns targeting various sectors, delivering malicious payloads via phishing attachments or links.
RedGuard
RedGuard, a derivative tool based on command and control (C2) front flow control technology, has a lighter design, efficient traffic interaction, and reliable compatibility with development in the GO programming language. Threat actors use it as a proxy to obscure their C&C profile from detection by blue team scanners and search engine crawlers.
As you can see, this AS is full of interesting and malicious findings. I am not blaming or attributing anything or anyone, just pointing out what I found. If anyone wants to follow up or contribute on this, please feel free to do so.
Don’t know the first thing about how Stark-Industries operates but I think it’s clear that their leniency is fostering a rotten ecosystem.