Had many cases of infostealer incidents lately so I decided to research the latest infra to update my understanding of the malicious infrastructure landscape.
TL;DR Full IoC list
1337team Limited Hypothesis
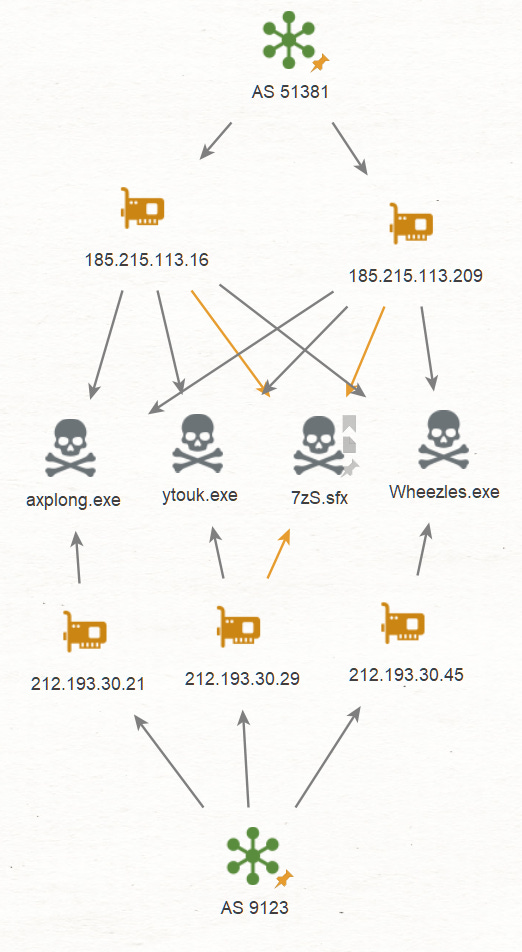
Expanding on our previous post, our starting point for this hunt is the IP 185.215.113[.]16 and the hypothesis that a threat actor associated with various infostealers has been using AS51381 (1337team Limited) to deploy malicious infra.
Starting on Censys from host 185.215.113[.]16 to get the services running to help us narrow down our search query.
As always, the first check is the SSH fingerprint which leads to an additional IP on the same AS supporting our initial hypothesis. As we can see, those hosts are running SSH and HTTP services, so we can use the AS + service ports to create our hunt rule.
autonomous_system.asn: 51381 AND services.port=22 AND services.port=80Our new rule returns 20 results which are all associated with various infostealers, the Amadey and Smoke loaders (Redline, Lumma, MarsStealer, Stealc) making it a success ;)
Going over the related files, we can see that some malicious files are communicating with IPs on multiple ASN indicating that the files are either used by multiple TA or that this specific TA is deploying infra on multiple providers (both possible).
Korean Cluster
Another finding was identified, following one IP from the initial hypothesis and pivoting off of a communicating malicious file named “cajubae” (hash:00173630900838da2ccce0ae7fb54f7d8b3138434f63d056c636e0aec4f8e37b)
We discover that many IPs from different ASN communicate with the same file, interestingly, the ASNs are registered in Korea which can help us focus our search for the next pivot.
Using Validin and the cert fingerprint we find additional results, which we can group by country to narrow down our search.
As mentioned above, focusing on Korea, we can see that a big chunk of the distribution is associated with AS 3786 and 4766 which leaves us with 23 results
Scanning the newly found IPs returned low or no detections but also very recent DNS resolutions of malicious domains, leading me to believe that we landed on a new cluster of malicious infrastructure.
# Korean Cluster
220.125.3[.]190
123.212.43[.]225
119.204.11[.]2
58.151.148[.]90
218.152.239[.]116
125.7.253[.]10
211.202.224[.]10
175.119.10[.]231
119.194.160[.]37
211.171.233[.]129
211.181.24[.]133
211.171.233[.]126
218.152.239[.]123
123.140.161[.]243
210.180.252[.]110
211.181.24[.]132
211.168.53[.]110
211.119.84[.]111
210.182.29[.]70
210.108.43[.]192
211.104.254[.]139
211.59.14[.]90
211.119.84[.]112Similarly, we can follow the same logic to filter for IPs in the Mexico cluster
# Mexico Cluster
189.163.178[.]96
201.103.179[.]216
187.144.133[.]47
187.225.144[.]248
187.204.66[.]156
187.204.206[.]7
189.181.23[.]186
187.156.113[.]114
187.199.194[.]16
201.124.5[.]27
201.110.232[.]122
189.181.30[.]147
187.224.115[.]16
187.201.7[.]156
189.189.172[.]68
187.204.55[.]0
187.199.191[.]176
189.181.53[.]56
187.199.183[.]102
201.110.241[.]248
187.205.255[.]67
189.163.98[.]139
187.134.57[.]31
187.152.17[.]215
201.110.217[.]30
201.119.104[.]185
189.165.174[.]71
187.201.114[.]50
189.189.229[.]237
189.163.142[.]13
187.228.55[.]117
189.134.97[.]255
189.245.27[.]132
201.103.66[.]91
189.163.10[.]121
187.201.135[.]232
187.211.202[.]16
187.201.173[.]202
187.134.41[.]207
189.232.12[.]90
187.211.34[.]223
187.156.38[.]229
187.156.79[.]158
187.204.80[.]208
187.204.100[.]230
189.190.189[.]17
201.119.33[.]19
189.179.37[.]132
187.134.42[.]142
187.201.131[.]196
187.140.17[.]135
187.199.187[.]63
189.232.1[.]60
189.165.166[.]147
189.141.147[.]36
187.156.64[.]85
187.134.80[.]172
201.124.243[.]137
201.124.224[.]61
189.169.23[.]66
187.156.151[.]152
187.134.40[.]51
187.156.82[.]96
189.161.121[.]167Finally, I noticed the domain niksplus[.]ru repeating over and over while researching this and resolving on many IPs indicating fast flux, which can lead down another rabbit hole that we’ll not follow in this post.
Summarizing, we started from a hypothesis of a TA deploying infra in one ASN and we managed to pivot to additional ASN and uncover newly deployed infra.
I’ll keep tracking these clusters over the coming weeks and update if anything interesting comes up. Feel free to expand on the findings and reach out if you want to chat.
Thanks and take care!