Wanted to have a look at Amadey Loader and its infra this weekend, so I found 2 domains that have been recently reported and made my coffee.
http://krakenlpay[.]com/8jfgndS3d/index.php
http://212.193.31[.]8/3ofn3jf3e2ljk2/index.php
Looking at the websites we can identify that the login page, directory structure and naming matches the Amadey loader login page that was previously reported.
Amadey functions primarily as a loader for other malicious payloads such as the Lumma stealer and an array of information stealers like Redline and Mystic. Recent reports indicate that threat actors like Secret Blizzard, have utilized Amadey to infiltrate systems via phishing emails that often employ social engineering tactics to trick users into executing malicious files.
Urlscan - Resource Hash Pivot
Using this as our starting point, I analyzed the website on urlscan.io and pivoted using the Resource Hash. The search returned 323 results. To validate our approach, I examined the first result, which confirmed our methodology by redirecting to another Amadey login page.
Knowing that the results are accurate, let’s try to find any patterns among them to try creating a hunting rule. Most of the results have consistent panel names & URL naming conventions like
Jo89Ku7d
Dem7kTu"
Zu7JuNko
CoreOPT
Additionally, there is a very high concentration of hosting in the following AS, with the login page size being very consistent 1/4/10 KB
AS51381 - 1337TEAM/ELITETEAM in Seychelles
AS57523 - Changway Technologies in Hong Kong
AS216319 - SUNHOST in GB
AS57678 - Cat Technologies in Hong Kong
AS216309 - EVILEMPIRE in GB
Furthermore, the predominant server config is
Nginx 1.18.0 on Ubuntu
Apache 2.4.58 instances
It’s worth noting that the resource hash value is different for the websites that use Apache software, leading to another set of results.
So to narrow it down and create a hunting rule that will cover all cases, we can combine our findings and include additional fields like the server and filenames present on the webpages like “style.css” and “Ico.ico”. This rule now covers everything related to Amadey login pages, doing a quick sampling proves exactly that!
page.url.keyword:*\/*\/Login\.php AND (server:"nginx/1.18.0 (Ubuntu)" OR server:"Apache/2.4.58") AND filename:"Style.css" AND filename:"Ico.ico"Comparing the results from all of the searches reveals 16 unique IPs and 32 new domains so I can safely say that the new rule works ;)
Armed with our 16 new IPs, let’s see if we can uncover more on the host side. Running a quick scan on the new IPs shows a mix of low, no and high detections.
Low-Key Conspiracy Theory
Before we move on, let me get a conspiracy theory out of the way. While looking into those IPs, I found that some of the ones that have been previously reported and (some) had references in the report, returned no results on the platforms that had been referenced.
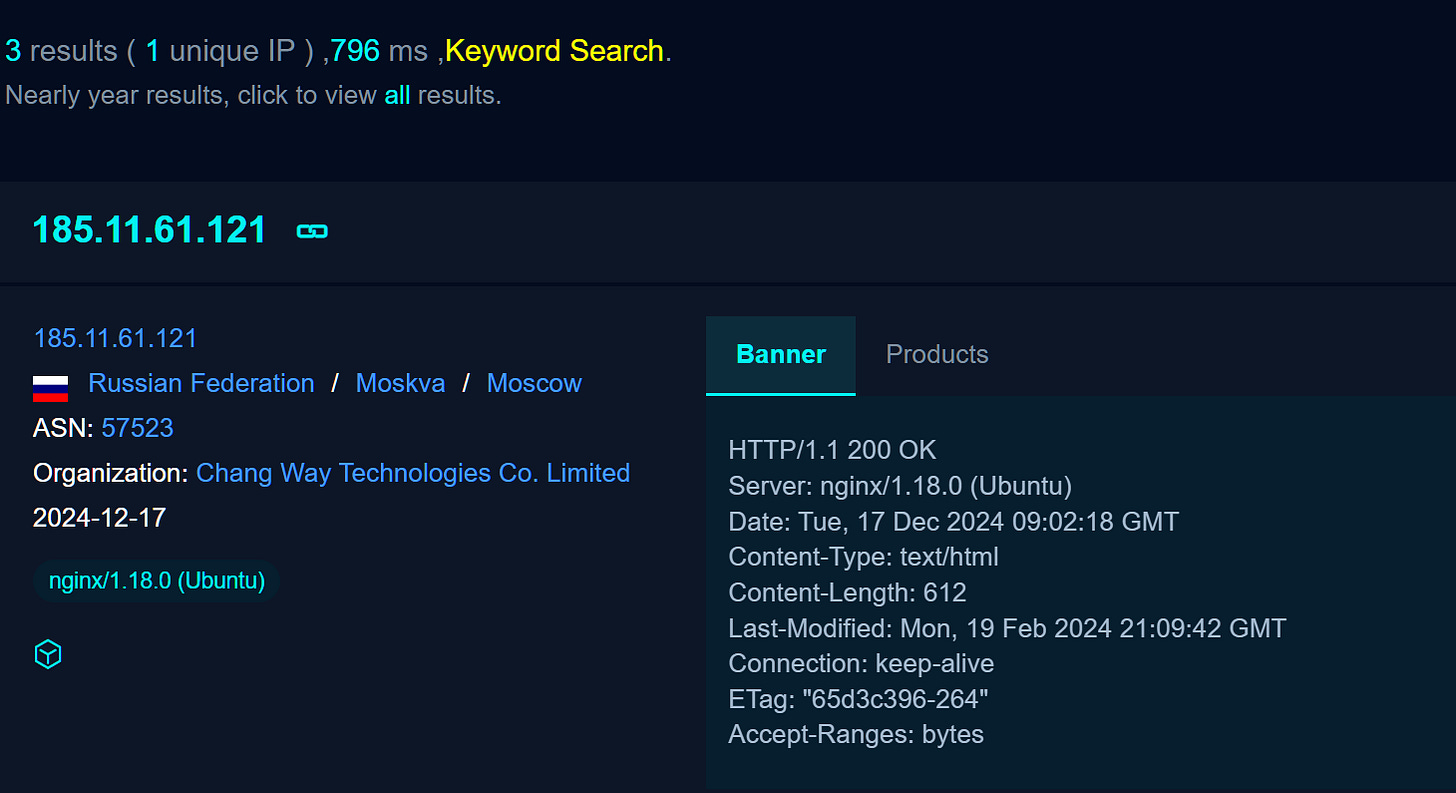
For example, the IP 185[.]11.61.121 was reported and had references in both Censys and Shodan. Searching on these platforms returns no active services, but searching for the same IP on FOFA returns results. I believe it could be possible that TA are actively blocking IP ranges used from Censys and Shodan.
As you know it’s not uncommon for threat actors to read those reports and perform counter-intelligence operations which puts researchers in a difficult spot about sharing IOC and findings openly.
Anyway, I think it was a good opportunity to outline the importance of having multiple sources while doing research. Now back to the infrastructure.
Infra Analysis
Going over the IPs we can see a group of 4 sharing the same SSH fingerprint, out of the 4, one IP was not included in the findings from before so we uncovered an additional host!
The group is hosted in the same AS 57678 (Cat Technologies Co. Limited) located in Russia.
The rest of the IPs didn’t lead to additional findings, so let’s have a look at some of the domains we found earlier. Reviewing the domains uncovered additional hosts that were hosting subdomains, additionally, we can easily spot a pattern when it comes to Autonomous Systems. AS 56971 seems to be the home for most of the domains/subdomains.
The AS pivot didn’t return any interesting results, so I will stop here for now.
As you can see this seems to be an extensive infrastructure with high concentration in Russia and China with some instances being protected by Cloudflare which seems to be a growing trend among TA.
As always, feel free to reach out. Thanks, and Happy Holidays!
IOC
# IPs
185.11.61[.]121
46.173.214[.]142
46.173.214[.]136
93.123.109[.]4
31.41.244[.]9
31.41.244[.]11
31.41.244[.]10
31.41.244[.]12
185.196.10[.]34
46.8.229[.]59
94.103.183[.]51
154.216.18[.]105
185.215.113[.]101
94.103.183[.]66
80.66.75[.]214
154.216.20[.]42
193.176.158[.]193
46.173.214[.]218
46.173.214[.]183
194.87.102[.]61
193.176.190[.]43
193.242.145[.]129
15.197.240[.]20
94.103.183[.]151
172.67.187[.]226
45.152.112[.]146
45.140.19[.]240
45.152.112[.]174
193.242.145[.]116
173.255.204[.]62
89.35.131[.]209
104.21.73[.]229
172.67.167[.]96
193.176.158[.]193
45.156.23[.]149
#Domains
amoamosss[.]com
bestofthebesttraining[.]com
brasseriehub[.]com
brasseriehub2[.]com
brasseriehub3[.]com
checkthebestofferyoucanget[.]com
culinarydownloads[.]com
downloaddining[.]com
downloadfilesoft[.]com
expertbigworldupdate[.]com
expertbigworldupdate2[.]com
expertbigworldupdate3[.]com
fastestfreecdn[.]com
filesoftdownload[.]com
getcloudsolutions[.]dev
innovupdates2[.]com
innovupdates3[.]com
kindofwelcomeperspective[.]com
o7labs[.]top
platformforcreateinterest[.]com
pleasurecanbesafe[.]com
proresupdate[.]com
resourcedownloadslatin2[.]com
resourcedownloadslatin3[.]com
responsibilitybridge[.]com
ruspyc[.]top
sanboxland[.]pro
simple-updatereport[.]com
theclientisalwaysright[.]com
tipinfodownload-soft1[.]com
tipinfodownload-soft2[.]com
tipinfodownload-soft3[.]com