Host long and prosper🖖
From BPH to massive malicious Crypto Exchange Infrastrcutre
Following up on my previous post, I wanted to start a weekend hunt from Prospero’s networks, a well known BPH provider.
As of this writing, the AS 200593 has 2 IP Blocks. Since there will be a lot of domains and DNS related queries in this hunt, we will be using Validin’t platform as it’s a goldmine of information. First things first, let’s see how many hosts we can find active on those networks.
# IP Blocks
91.202.233.0/24
91.215.85.0/24Breaking the ice
We start by checking how many hosts serve any domains. To keep the IoC somewhat fresh, we'll limit the search results to February 13th-15th and onward.
By putting my amazing analytical and data engineering skills to work and definitely not using AI to parse the results, we have the following for the first network (91.202.233.0/24)
58 Active IPs
892 Domains
To avoid chasing infrastructure that is currently offline, we can further refine our search by filtering the Host responses of “200 OK”, now we are left with
15 IPs and 85 unique Domains. Most, if not all of the domains are associated with mainly phishing activities following one of 4 main themes.
Crypto (trusted-fastbtc[.]top)
Netflix/Streaming (neifiixapp[.]com)
Banking (sweedbank-help[.]com)
Shiping & Logistics (transport-mondiairelay[.]com)
91.202.233.11
91.202.233.17
91.202.233.132
91.202.233.137
91.202.233.140
91.202.233.142
91.202.233.143
91.202.233.145
91.202.233.146
91.202.233.147
91.202.233.153
91.202.233.155
91.202.233.160
91.202.233.198
91.202.233.217Analysis & Grouping
Based on common characteristics and patterns, we can easily identify 2 main clusters hosting similarly themed phishing websites, indicating a centralized campaign.
Cluster 1 - 91.202.233.0/24
Many domains are hosted across multiple IPs and that many of the hosts have similarities when it comes to services and service titles. For example, many are serving plesk pages exposing a /login.php or /login_up.php page.
Specifically, the following 5 IPs all host 84 identical domains. Additionally, those hosts share common page titles like "Web Server's Default Page" or "Plesk Obsidian 18.0.67"
91.202.233.132
91.202.233.142
91.202.233.140
91.202.233.143
91.202.233.160Cluster 2 - 91.202.233.0/24
The next cluster is comprised of 3 IPs that host around 20 domains, all these domains appear with the "FASTPANEL" page title
91.202.233.145
91.202.233.155
91.202.233.146We could use the info gathered from those two cluster to further hunt for additional findings but I would like to focus more on the next big finding that we will analyse below. However, if you want to dive deeper into the networks, this information can be used as a starting point.
# HOST-LOCATION
/login_up.php
# HOST-TITLE
Contains : "Web Server's Default Page" or "Plesk Obsidian" or "FASTPANEL"
Port 22
SSH-2.0-OpenSSH_8.4p1 Debian-5+deb11u3
SSH-2.0-OpenSSH_8.9p1 Ubuntu-3ubuntu0.10
Type A record value contains "plesk"
Headers
HTTP/1.1 200 OK
Path: /login_up.php
HTTP/1.1 200 OK
FASTPANEL
JARM
29d29d00029d29d00042d42d0000002059a3b916699461c5923779b77cf06b
29d29d00029d29d00042d42d00000000f78d2dc0ce6e5bbc5b8149a4872356
00000000000000000042d00000000022a14908b59e70935d7a5c2f786c3606The Crypto Exchanges
Now for the really interesting part!
While reviewing the initial results, an interesting pattern stands out immediatly in the title of some pages. The words “Cryptocurrency Exchange”, indicating possible cryptocurrency exchange impersonations, diving a little deeper we can filter the page titles using these words.
This leads us to a little over 100 hosts, a manageable number that we can further analyze.
All of the 106 hosts share one characteristic, a Header Hash (Validin).
Now that we have a header hash, we can used it to expand our search on other networks outside of Prospero ASN.
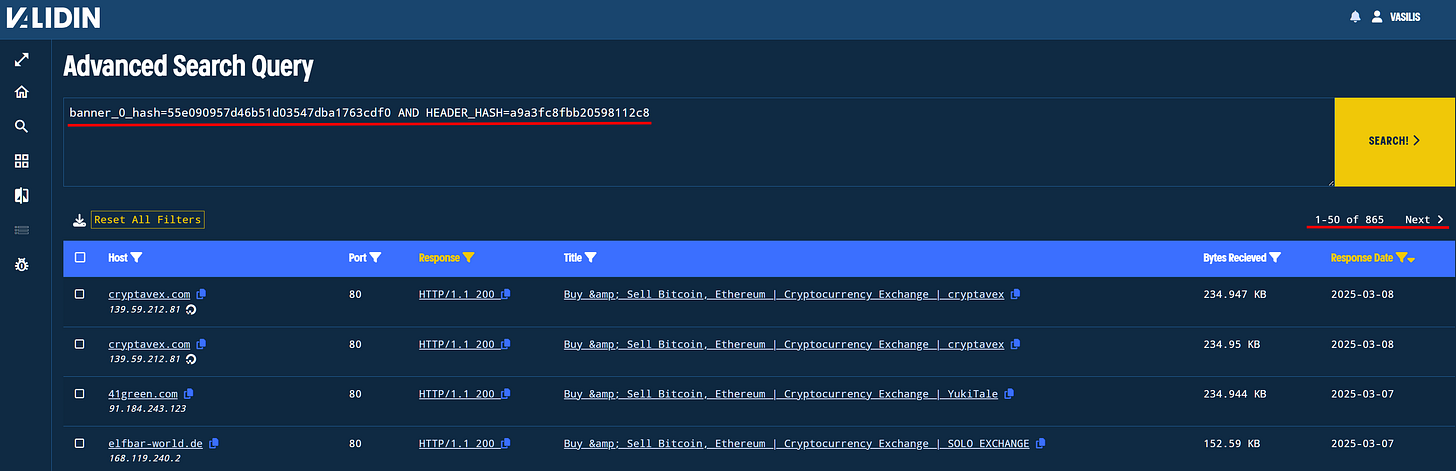
Searching on the platform using the aforementioned hash returns 160 unique hosts that are serving multiple domains (seen in the last 20 days), some of the domains hosted on those servers are not related to crypto exchanges and that can lead to a very broad search.
In order to further refine our hunting rule, we can also add the “Banner Hash” which will help us focus only cryptocurrency exchange impersonations.
banner_0_hash=55e090957d46b51d03547dba1763cdf0 AND HEADER_HASH=a9a3fc8fbb20598112c8 Using the new rule returns 206 unique IoC, all of these IPs/Domains/URLs are impersonating legitimate crypto exchange, using the binance API to pull current prices and have the exact same look which clearly means they are part of a single campaign. What is more interesting is that this campaign, spans multiple ASNs indicating that is not centralized on Prospero’s bullet proof hosting.
Many of the findings include the exchange name “Yukitale” & “cryptavex” which is mentioned in a scam report found on a Russian site, attributing the attack to advanced Ukrainian scammers(?).
*based on the info WE have, can’t really attribute anything to anyone
Interestingly enough, none of these IoC have been reported yet making this a very successful finding & hunt rule.
P.S : The hosts we identified above are hosting more sites unrelated to crypto theme that might be malicious as well, I haven’t checked them out. Feel free to do it
The End
Putting all together, we started by reviewing Prospero BPH which led us to a pretty big and fresh infrastructure probably associated to a single Threat Actor, spanning multiple ASNs, hosting crypto related scams.
In future posts, we might try to find common patterns between the hosts to see if they are connected to other malicious campaigns.
Thanks and take care!