Prospering Lumma
Bulletproof Malware
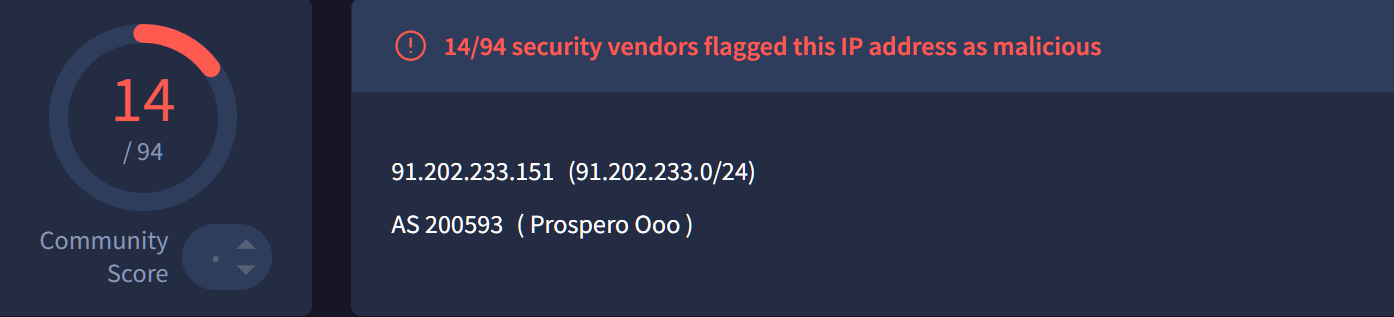
You all know that Lumma is going crazy lately. I was tracking another Lumma cluster (I know shocking) when Krebs published a new article about Prospero, a bulletproof service provider. Funny coincidence the starting poing of my ongoing investigation was an IP hosted at that ASN (200593) which send me down a rabbit hole.
Started from the IP 91,202.233.151 that is actively hosting Lumma infostealer malware.
Starting from urlscan.io we can pivot off one of the hashes that are provided in the indicators tab
hash:5021cc94accc930c25a56574dcf3ab56b9717e450d3712a424b27cab1eca1a9dThat leads to 60 results, most of the URLs are hosted on the malicious IP 91,202.233.151 but we uncover some additional IPs and URLs, serving the same malware.
After analyzing the results we are left with the following groups of IPs, most are using Apache 2.4.52, one using 2.4.53 and a few are behind Cloudflare’s CDN. Additionally, we can observe 2 distinct directories, “1337” and “Update”
IPs
# Apache/2.4.52 (Ubuntu)
91.202.233.151
185.99.135.162
85.31.47.154
87.121.86.16
185.196.9.251
85.217.144.194
84.32.190.45
# Apache/2.4.53 (Win64) OpenSSL/1.1.1n PHP/8.1.6
95.214.24.244 - 2125873
# Cloudflare
188.114.97.3
172.67.171.88Related URLs & Domains
# 1337 Directory
update-checker-status.cc/1337/
security-service-api-link.cc/1337/
utorrent-backup-server5.top/1337/TORRENTOLD-1.exe
utorrent-server-api.cc/1337/TORRENTOLD-1.exe
win-network-checker.cc/1337/TORRENTOLD-1.exe
fox-news-checker.cc/1337/TORRENTOLD-1.exe
# Update Directory
microsoft-auth-network.cc/update/TPB-1.exe
coinbase.connexion-monwallet.com/update/TPB-1.exe
information-binance.com/update/TPB-1.exe
compte-coinbase.com/update/TPB-1.exe
rappel-coinbase.com/update/TPB-1.exe
api.aide-coinbase.com/update/TPB-1.exeNext, I tried to find commonalities between the hosts/technologies used but I couldn’t create a successful hunt rule. The only common thing I managed to uncover was a shared SSH key between 2 IPs using Hunt.io which led to a dead end.
87.121.86.16
85.31.47.154Most of the hosts did not return any results on Censys or Shodan which makes me think that the operators are blocking the crawlers on purpose.
That being said, we now know from Kreb’s report that the AS 200593 is used mainly for malicious purposes, since it’s a relatively small AS, we could use alternative methods to review the domains that are hosted on those hosts and try to identify potential Lumma (or other malware) distribution servers.
Moving over to Validin’s platform which is amazing for DNS related investigations and doesn’t seems to be blocked. Since we know the IP blocks, we can search for them and filter the A records to get any domain that is hosted in that network, to further reduce FP we can filter for A records that have been “Last Seen” after the 15th of February.
This leave us with a little over 880 domains.
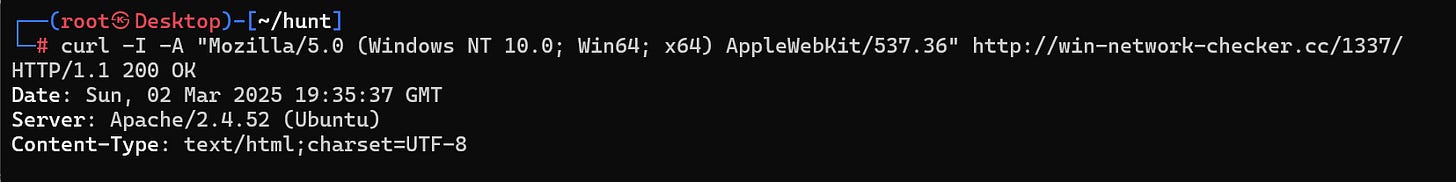
Since we know this particular Lumma campaign is using the /1337 and /update directories, we can query directly for them. (adding the agent to avoid getting blocked if any mechanisms are in place)
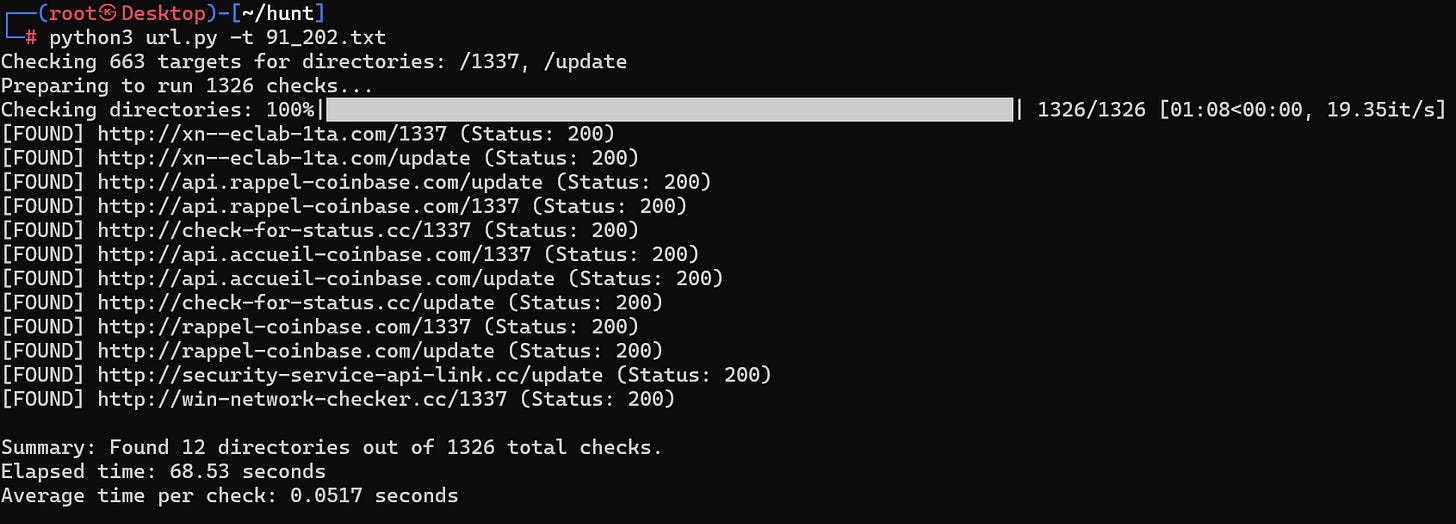
curl -I -A "Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36" http://win-network-checker.cc/1337/Now that we know the logic is correct, we can automate this process by creating a script. Using my newly hired coder Claude, we create a script that will query every url for the directories and we’ll repeat the same process for the second IP block
# 91.202.233.0/24
91.202.233.150
http://xn--eclab-1ta.com/1337
http://xn--eclab-1ta.com/update
91.202.233.151 (seen in the begining of this post)
http://api.rappel-coinbase.com/update
http://api.rappel-coinbase.com/1337
http://check-for-status.cc/1337
http://api.accueil-coinbase.com/1337
http://api.accueil-coinbase.com/update
http://check-for-status.cc/update
http://rappel-coinbase.com/1337
http://rappel-coinbase.com/update
http://security-service-api-link.cc/update
http://win-network-checker.cc/1337# 91.215.85.0/24
http://canadapharmacytrust.net/update
http://fastrxorders.com/1337This search returned a few more domains and a couple of new hosts, ran a quick scan on one of the findings and it seems that our logic is solid, one of the sanboxes flagged it and it seems like ours was the first submission.
This was just one of Lumma’s active campaigns, there are other that are using different directories, names, executables etc. As you can understand this investigation can take ages but I just want to outline one approach rather than finding all the urls so for now I’ll stop here.
The post from Krebs made me wonder what other interesting findings we might uncover in these networks, so, in the coming weeks I’ll have a closer look on the AS and try to map any malicious campaigns.
As always, feel free to reach out!
PS : Thank you all for your messages and support, it means a lot!