Weekend Hunt
Uncovering Shared Malware Infrastructure
As always, the story starts with me browsing Malware Bazaar. Going through the latest samples, I stumbled upon an interesting discovery. The malware sample that started everything was a crypted .exe of the well known Lumma Infostealer.
Lumma
Lumma is a potent information stealing malware that has gained traction primarily through Telegram channels, particularly by masquerading as legitimate software or cracked applications, such as CCleaner 2024. Its tactics include stealing sensitive user credentials stored on infected devices and ensuring persistence by checking if it is set to run at system startup.
Lumma C2 Analysis
The file is hosted at wdfiles.ru, a free file hosting service.
https://wdfiles[.]ru/29vck
Filename: crypted_LummaC2.exe
sha256: 50828bab09602ff91a8fcb4c8ded23a2331472e62b32edc8f54b68c5ae91f40eReviewing the sandbox reports, I quickly found all the domains contacted upon execution of the malicious file. Most of the domains were offline at the time of writing. Additionally, all of the domains are newly registered and offer very little information to pivot from, so this would normally be the end of this review. But it's not!
https://preside-comforter[.]sbs
https://savvy-steereo[.]sbs
https://copper-replace[.]sbs
https://record-envyp[.]sbs
https://slam-whipp[.]sbs
https://wrench-creter[.]sbs
https://looky-marked[.]sbs
https://plastic-mitten[.]sbs
https://lumhiddenforest[.]shop/api
https://steamcommunity[.]com/profiles/76561199724331900
https://marshal-zhukov[.]comAnother malware sample reported around the same time had an interesting story to tell. The malware analysis identified the sample as Amadey malware.
URL: http://185.215.113[.]16/mine/random.exe
SHA256: 373ffb138b7376264a307837ef5bd51bd02380376f9fdd27350cf1b65a28bcbb
Amadey
Is capable of remote access, keylogging, credential theft, and cryptocurrency mining. Recent reports indicate that Amadey has been delivered via various techniques such as malicious CAPTCHAs and phishing emails targeting sectors like finance and government in Latin America.
Amadey C2 Analysis
Reviewing the sandbox reports for Amadey showed that the communicating domains are exactly the same showing a clear infrastructure connection between the 2 (and additional) malwares.
However, the Amadey malware connected to many more domains upon execution, so I followed the reported IPs/URLs on sandbox, Censys, and VT. Some domains redirect to what appears to be C2/distribution servers hosting different malware/infostealers for distribution depending on the victim's OS/versions, etc.
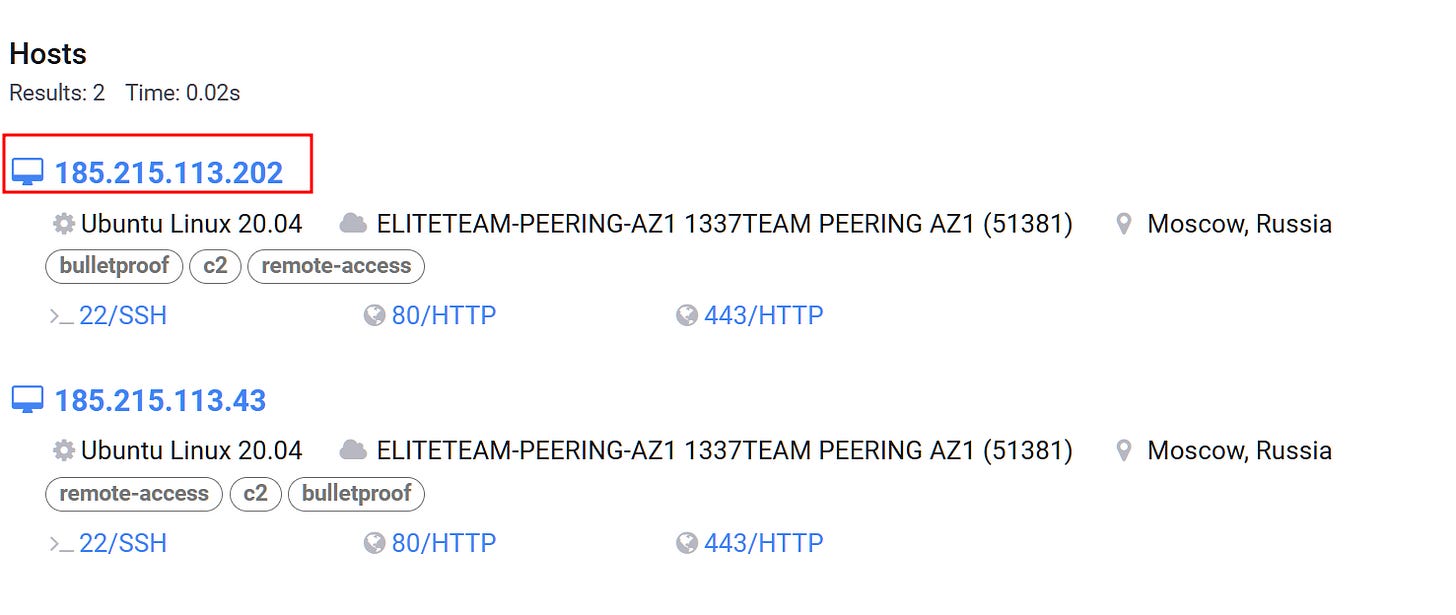
IP : 185.215.113[.]43
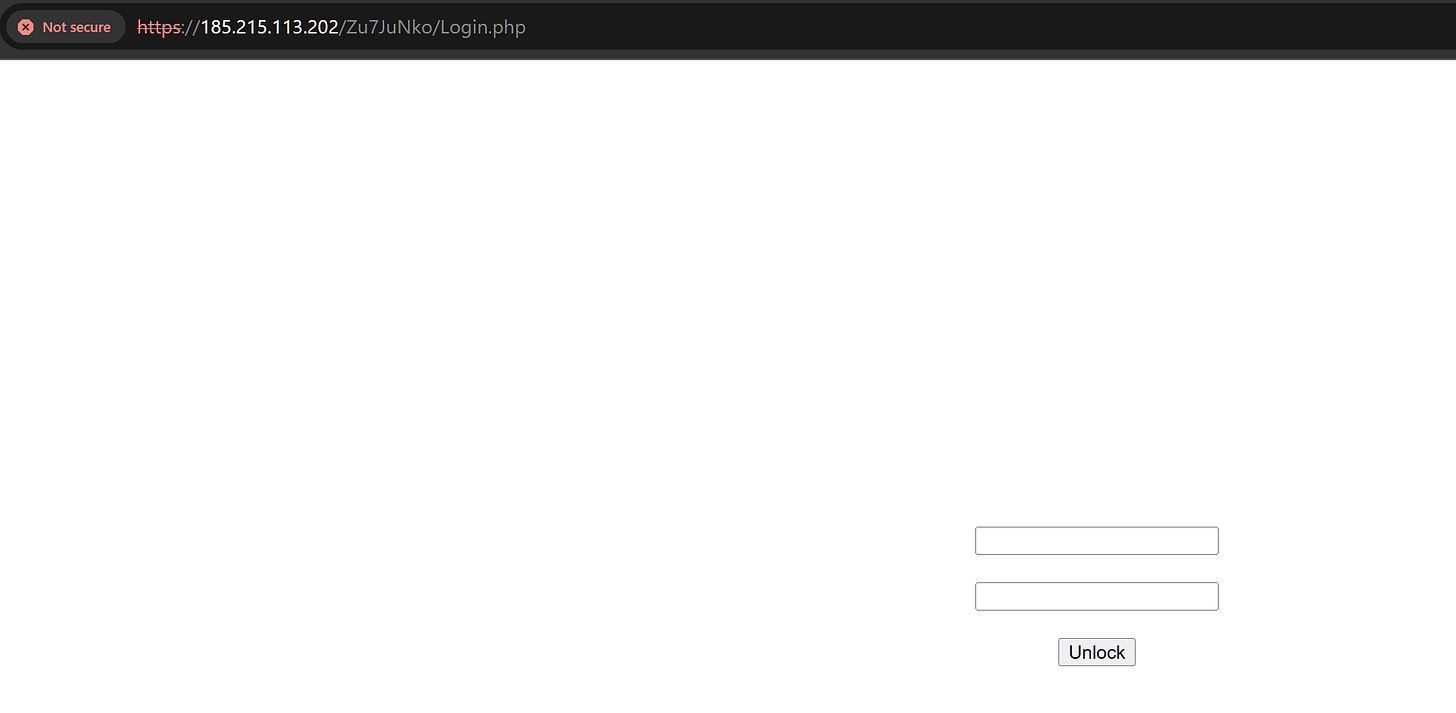
url: http://185.215.113[.]43/Zu7JuNko/index.phpAn additional interesting find was a possible C2 login page which led to an additional pivot. Using the SSH key fingerprint on the server, I was able to uncover another C2 server that was not reported in the sandbox analysis.
services.ssh.server_host_key.fingerprint_sha256: e7c420a6cdcff65864fe44d2f524c79da82d68fa40c3e72ef4d555bd911231b6My understanding is that there is a tier of distribution servers that hosts various infostealer variants and an additional tier of C2 servers controlling the distribution and actions on objectives.
There are a million more pivots that we can probably do and uncover more, so please feel free to jump in and assist if you are interested.
Thanks!
IOC
# IPs
185.215.113[.]43
185.215.113[.]202
185.215.113[.]206
185.215.113[.]16
185.156.72[.]65
185.199.111[.]133
31.57.135[.]113
31.41.244[.]11
20.233.83[.]145
34.118.84[.]150
18.213.123[.]165
104.21.16[.]9 # URLs grouped by domain
home[.]twentykx20pt.top
home[.]twentykx20pt.top/AMeacCwtwXCqXfwTNSOI1732768477?argument=jU36GhzuE8Oe2jSq1732896340
home[.]twentykx20pt.top/AMeacCwtwXCqXfwTNSOI1732768477
twentykx20pt[.]top
twentykx20pt[.]top/v1/upload.php
raw[.]githubusercontent.com
raw[.]githubusercontent.com/6nz/virustotal-vm-blacklist/main/gpu_list.txt
raw[.]githubusercontent.com/6nz/virustotal-vm-blacklist/main/processes_list.txt
raw[.]githubusercontent.com/6nz/virustotal-vm-blacklist/main/ip_list.txt
raw[.]githubusercontent.com/6nz/virustotal-vm-blacklist/main/pc_userna
raw[.]githubusercontent.com/6nz/virustotal-vm-blacklist/main/MachineGuid.txt
raw[.]githubusercontent.com/6nz/virustotal-vm-blacklist/main/pc_username_list.txt
raw[.]githubusercontent.com/6nz/virustotal-vm-blacklist/main/pc_na
raw[.]githubusercontent.com/6nz/virustotal-vm-blacklist/main/Machi
raw[.]githubusercontent.com/6nz/virustotal-vm-blacklist/main/processes
raw[.]githubusercontent.com/kgnfth/tumblr/refs/heads/main/svchost.exe
raw[.]githubusercontent.com/6nz/virustotal-vm-blacklist/main/pc_name_list.txt
raw[.]githubusercontent.com/6nz/virustotal-vm-blacklist/main/i
raw[.]githubusercontent.com/6nz/virustotal-vm-blacklist/main/g
raw[.]githubusercontent.com
github[.]com
github[.]com/kgnfth
github[.]com
github[.]com/kgnfth/tumblr/raw/refs/heads/main/svchost.exe
github[.]com/kgnfth/tumblr/raw/refs/heads/main/svchost.exeP
atten-supporse[.]biz
atten-supporse[.]biz/api
atten-supporse[.]biz/
atten-supporse[.]biz/Q
atten-supporse[.]biz/apiE
upx[.]sf.net
szurubooru[.]zulipchat.com/api/v1/messages
31.41.244[.]11
31.41.244[.]11/files/unique2/random.exePM
31.41.244[.]11/files/unique2/random.exe
31.41.244[.]11/files/unique1/random.exe
31.41.244[.]11/files/7781867830/XXM5y4g.exe
185.215.113[.]16
185.215.113[.]16/well/random.exeC
185.215.113[.]16/ferences.SourceAumid2
185.215.113[.]16/well/random.exe61395
185.215.113[.]16/well/random.exeE
185.215.113[.]16/well/random.exe5
185.215.113[.]16/well/random.exe3
185.215.113[.]16/well/random.exec61395d
185.215.113[.]16/steam/random.exe
185.215.113[.]16/well/random.exe2
185.215.113[.]16/well/random.exea
185.215.113[.]16/well/random.exehp32
185.215.113[.]16/luma/random.exe
185.215.113[.]16/well/random.exeM
185.215.113[.]16/well/random.exe310001
185.215.113[.]16/luma/random.exe
185.215.113[.]16/c0f9c30b4baed74c61395d7fac00b58987e8fcf7b8c730804042ba5ce9024un5M
185.215.113[.]16/well/random.exeAppData
185.215.113[.]16/well/random.exen
185.215.113[.]16/well/random.exeg
185.215.113[.]16/well/random.exe
185.215.113[.]16/well/random.exe311001
185.215.113[.]16/well/random.exe#
185.215.113[.]16/steam/random.exeF
185.215.113[.]206
185.215.113[.]206/c4becf79229cb002.php/
185.215.113[.]206/c4becf79229cb002.php
185.215.113[.]206
185.215.113[.]206/c4becf79229cb002.phpg:Q
185.215.113[.]206/c4becf79229cb002.php9
185.215.113[.]206/
185.215.113[.]206/c4becf79229cb002.phpy
185.215.113[.]43
185.215.113[.]43/Zu7JuNko/index.php
185.215.113[.]43/Zu7JuNko/index.php78
185.215.113[.]43/Zu7JuNko/index.php;
185.156.72[.]65
185.156.72[.]65/files/download?aD
185.156.72[.]65/dll/key
185.156.72[.]65/files/downloadft
185.156.72[.]65/files/download65/files/downloadft
185.156.72[.]65/add?substr=mixtwo&s=three&sub=nosub
185.156.72[.]65/files/download-269d65d60108622213LMEM
185.156.72[.]65/dll/downloadyW
185.156.72[.]65/files/download65/files/download
185.156.72[.]65/dll/keysystem32
185.156.72[.]65/files/download
185.156.72[.]65/files/downloadLMEM
185.156.72[.]65/dll/keyRL
185.156.72[.]65/dll/keyML
185.156.72[.]65/dll/download
185.156.72[.]65/files/download65/files/downloadt
185.156.72[.]65/files/downloadUZ