Uncovering GoPhish Deployments
Patterns, Tools, and Techniques
Nothing special this weekend, just a short writeup on quick and easy ways of finding GoPhish instances.
GoPhish
GoPhish is an open-source phishing simulation framework used by organizations to test and train their employees cybersecurity awareness and by threat actors to test if they can phish unsuspecting users. Using templates, an HTML editor and an easy to use UI, it makes it easy to create phishing campaigns. Upon installation it uses port 3333 by default for its administrative interface/dashboard.
Our starting point is https://2.59.22[.]50:3333, as you can see, we are redirected to the default login page.
This login page is common for every GoPhish instance unless manually altered which makes it a perfect starting point to identify hosts running GoPhish. We can use the “gophish.css” filename as a pivot point for our initial search on urlscan.
Analysis
The search returned 911 results, whenever I am presented with a large number of results I always group the findings and use some graphs to help visualise the findings. Some key points are
AWS was the top hosting provider
Nginx prevalent server technology (1.18.0)
Default admin ports 3333 often used
Looking at the findings, we can also see another pattern, malicious domains often included security terms (secure, safeguard, protected), IT terminology (admin, helpdesk, support), and authentication words (login, auth, verification). They seem to impersonate major brands through Microsoft-related terms (office365, sharepoint), financial services (paypal, bank), and social platforms (linkedin, google, facebook). Their structure typically features hyphenated words, suffixes like "notification" or "service," geographic markers (uk, eu), and alternative TLDs (.online, .site, .io).
microsoft.protect.tools
microsoft.nodelab-it.de
sicsoe-microsoft.system-it-security.com
microsoft-teams-update-support-manager.rngdis.fr
linkedin-notification.co.uk
linkedin.invitation-requests.com
google-alerts.notification-service.co.uk
google-accounts.live
paypal.security-service.site
admin.capitarlise.com
capitallbank.co.inThe results go back a couple of years and most of the old domains/IPs will be inactive so let’s focus on the findings from the last 15 days.
2.59.22.50
2.59.22.50:3333
188.114.97.3
gofish.cxtwh.site
16.171.178.228
avcilar.online
157.230.228.36
completion.normaltests.site
13.234.63.50
ec2-13-234-63-50.ap-south-1.compute.amazonaws.com
88.30.58.65
rupema.crmatica.com
188.166.136.28
cilsurvey.com
94.130.105.168
awareness-phish.hackattack.com
185.184.58.213
gophish.rsecure.lu
51.254.115.39
39.ip-51-254-115.eu
admin.dieenvironnement.fr
157.90.230.60
gophish-admin.nitbg.com
3.212.215.46
admin.0kta.help
52.220.112.85
fisherman.amcasia.com
142.93.102.239
jdwl.online
15.236.5.186
gophish.eassist.me
54.37.65.245
245.ip-54-37-65.eu
35.209.234.80
c74154.sgvps.net
46.101.213.152
hgp.eamil-admin.com
195.191.219.218
gophish.gompels.comMoving over to Censys for a closer look at the hosts, and looking at the domain admin[.]0kta.help hosted at 3[.]212.215.46 we can see another interesting pivot point.
We can use the HTML tags to search for hosts returning the same response.
This search returns close to 1.2K of hosts results meaning that many domains can be hosted on the same host.
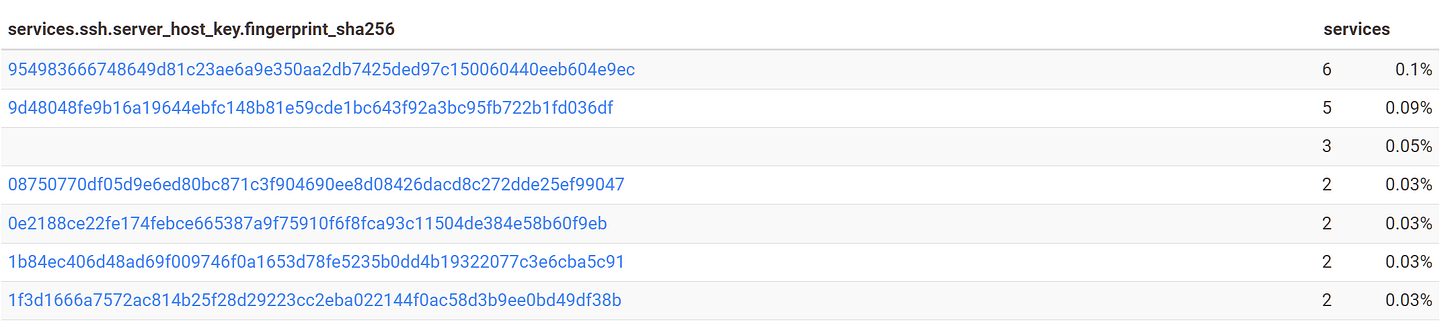
We can further investigate the domains by using the reporting functionality on Censys and filter by “dns.names” which generates a report based on the requested field. This indeed shows that there are around 3.5K of domains hosted on those servers
Other interesting reporting fields can be the ASN, Country, server technology or SSH fingerprints. For example, using the SSH fingerprint we can see that some servers share fingerprints indicating that they have probably been provisioned by the same entity.
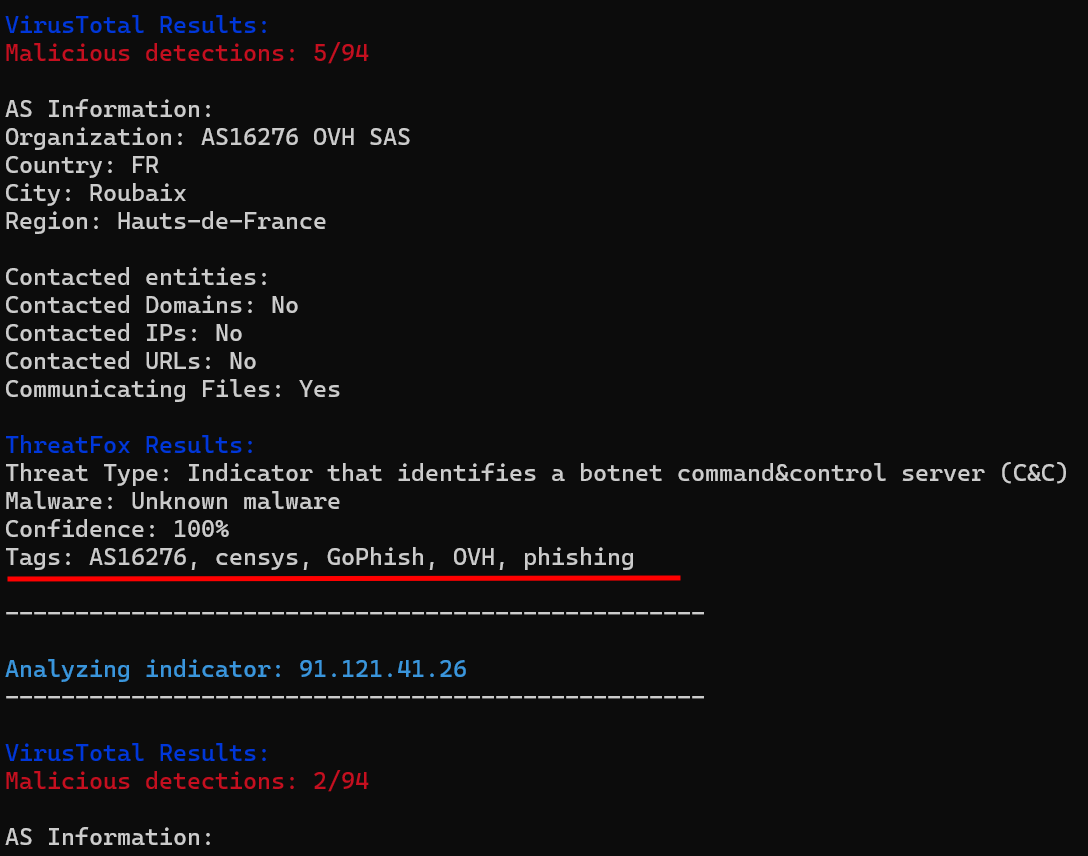
Doing a quick lookup for the first group of IPs we can see that they have been previously reported and are associated with GoPhish instances.
As you can understand, this is a huge rabbit hole you can fall down and spend a lot of time, pivoting from domain to domain and associated files, uncovering malicious and educational phishing campaigns. Since it’s very hard to follow all the trails and figure out which is malicious and which is not I will not share any IoC.
As I said in the begining, this is just a short writeup to show how you can uncover GoPhish instances, so for now, I’ll leave it here.
As always reach out if you have any questions or suggestions.
All the best and Happy New Year!