Twitter Bot Network
Patterns, phishing and evasion tactics in suspicious follower accounts
I am either the sexiest cybersec analyst, or I am being targeted by bots. Unfortunately it’s the latter.
It’s known that Twitter -- recently known as X (ba dum tsss!!) -- is filled with bots but I thought it would be interesting to investigate and try to understand if those are organized or opportunistic campaigns.
Just to give you a bit of context on how I am using the service, my Twitter is just an infosec feed. I don’t follow anyone socially, I rarely comment or repost, yet, bots found my account. I was reviewing my 100 followers and it seemed like each one of them is a bot account.
Now, on to the mildly interesting part. I will start by outlining several common patterns that I observed in every account.
Most of the accounts have a URL on their profile, following the same structure, that includes the account's username, likely for tracking purposes.
Additionally, after running the URLs through both commercial and opensource sandboxes & URL scanners, the majority of them reported discovery-related behavior which seems suspicious to me. Even though this looked like a weird behavior to me, I am not a web developer so I asked a few people that are actually in the field and all of them told me that this behavior was indeed suspicious.
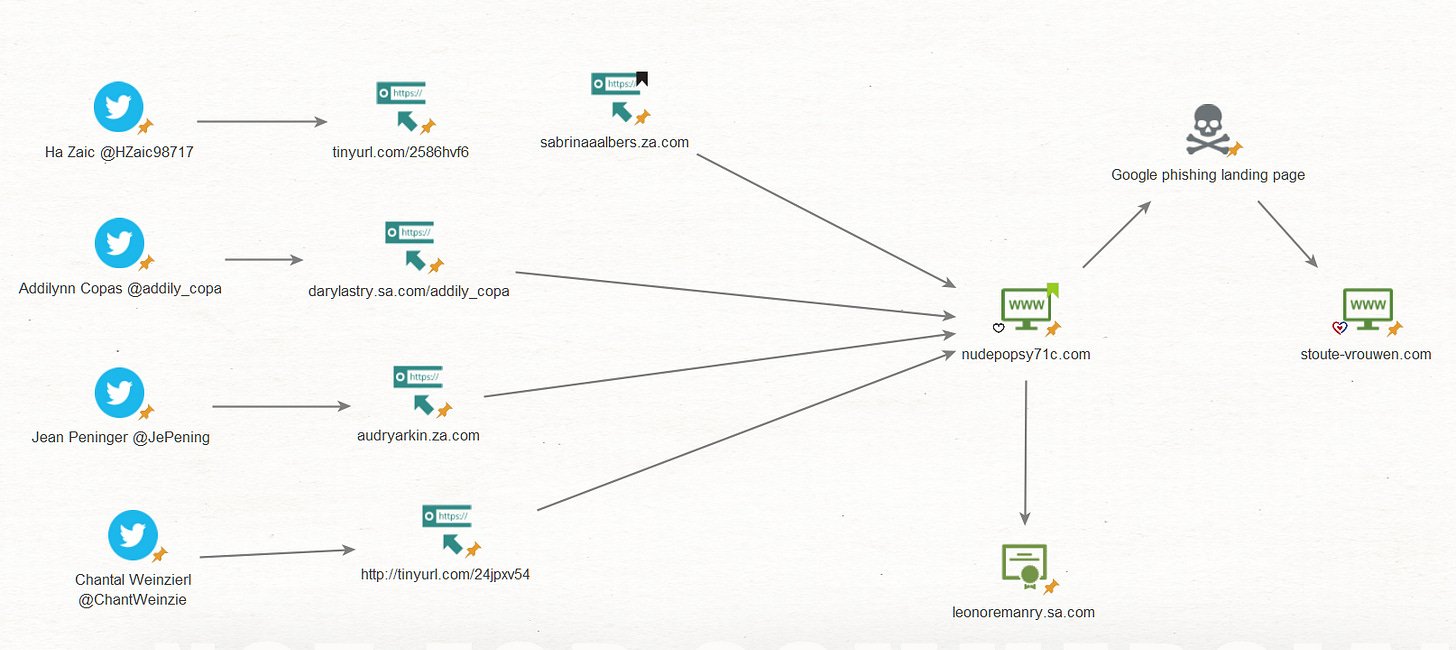
Then, I fell down the rabbit hole. I started sandboxing and visiting all of the URLs and following every redirection, trying to find a pattern, after visiting every last one of the URLs, I grouped them and was left with 4 distinct groups that were sharing some common characteristics.
nudepopsy71
This was by far the biggest group, close to 60/100 accounts pointed to the same domain nudepopsy71c[.]com.
The domain is a scam dating site clone that after a basic questionnaire (to figure out you are not a bot), redirects to a phishing landing page of an actual dating website called stoute-vrouwen[.]com.
I haven’t followed up on that dating site so I can’t evaluate if they are part of the scam or not.
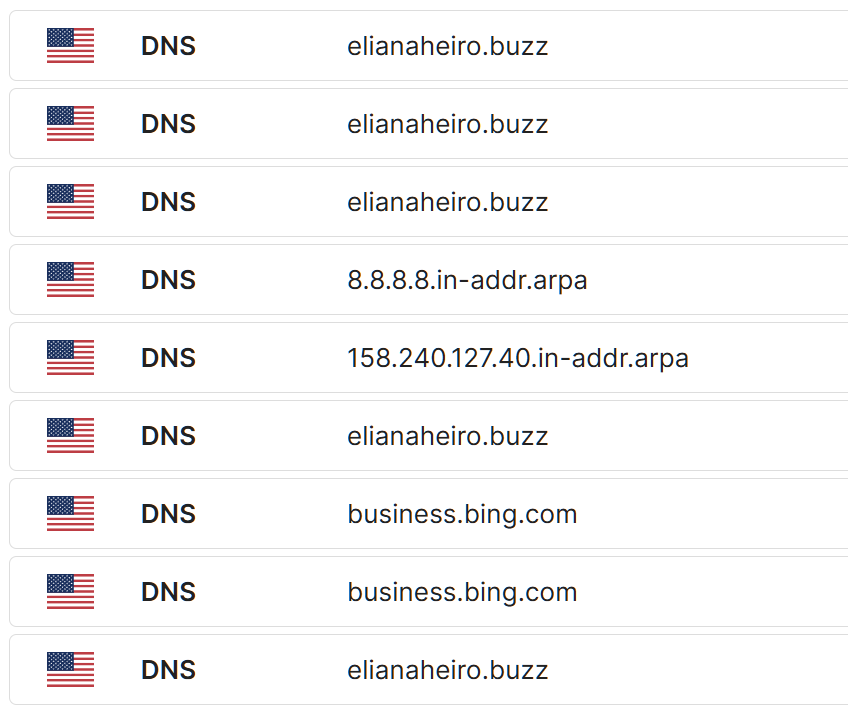
DotBuzz
The next group contained about 20 accounts that were pointing to various .buzz domains - all following the same /username structure, most of the URLs returned a 404 or redirected to google frontpage after trying to grab system information.
SA group
The last group had about 20 accounts that were redirecting to domains - using the same structure- that had the same domain suffixes (SA/ZA)
I can’t attribute this operation to any specific threat actor or fully understand the motives but I think it’s safe to say that this is a coordinated operation using consistent URL structure and landing pages, probably engaged in phishing while using geographically diverse hosting locations (South Africa, Russia) to evade detection or takedown efforts.
If anyone followed anything similar or have additional info, please feel free to reach out.