Investigating a malware sample reported by X user @Tac_Mangusta
https://x.com/Tac_Mangusta/status/1864281983079096340 which was tagged as the Remcos RAT.
Remcos
Is a commercial RAT (remote administration tool) sold online. It provides purchases with a wide range of advanced features to remotely control computers belonging to the buyer. However, threat actors have abused Remcos to collect sensitive information from victims and remotely control their computers to perform further malicious acts.
Analysis
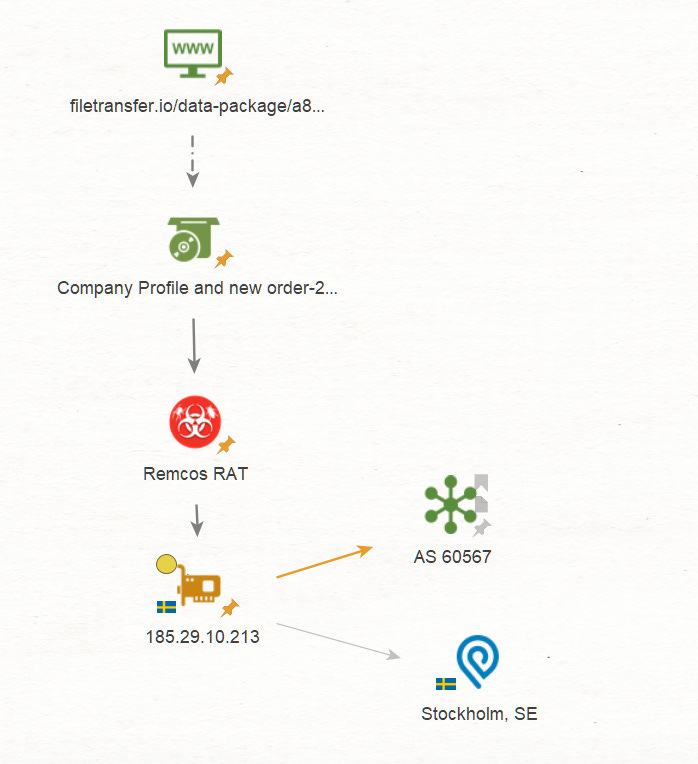
The infection chain starts with a phishing email, redirecting to the file sharing site filetransfer.io, the user downloads the malicious file which contains the Remcos RAT.
Malware analysis reports show the malware connecting to the IP 185.29[.]10.213:63650
Examining the reported IP shows 4 services running on the server, the reported port however is not shown, which makes me think that there is some sort of header/cookie block on the server side to prevent discovery and obfuscate the service further.
Building hypotheses
Since I didn’t have a lot of information to go on and in order to continue the hunt, I needed to build a hypothesis.
Autonomous System & Services
It’s not uncommon for threat actors to use the same AS when they provision infrastructure, additionally, they often use templates for server deployment.
Following this hypothesis, I pivoted using the AS 60567( DataClub S.A. ) and specific services which led to 27 new hosts. Unfortunately, most of those IPs came back clean and their services didn’t have any distinct characteristics that I could pivot from.
autonomous_system.asn: 60567 AND (services.port: 135 AND services.port: 3389 AND services.port: 5985 AND services.port: 47001)Using a script (thank you Claude), I checked the findings against Virus Total. Five of the resulting IPs had been previously reported, so I followed that lead. However, the detections are associated with generic spam and phishing campaigns, not directly connecting them to Remcos RAT so confidence level is moderate. (Credibly sourced information but not enough for complete certainty)
RDP & Port 47001
Moving forward, I thought of approaching this from a different angle so I started searching on ThreatFox for IOC related with Remcos malware
Looking at the associated IPs and given the nature of the tool, I noticed that most of them had port 3389 (RDP) open which was often spotted alongside port 47001. This search query, as expected, generated more than 400K results which is not really helpful, so I added this finding to the information gathering notes and moved on.
Hash & Communicating IPs
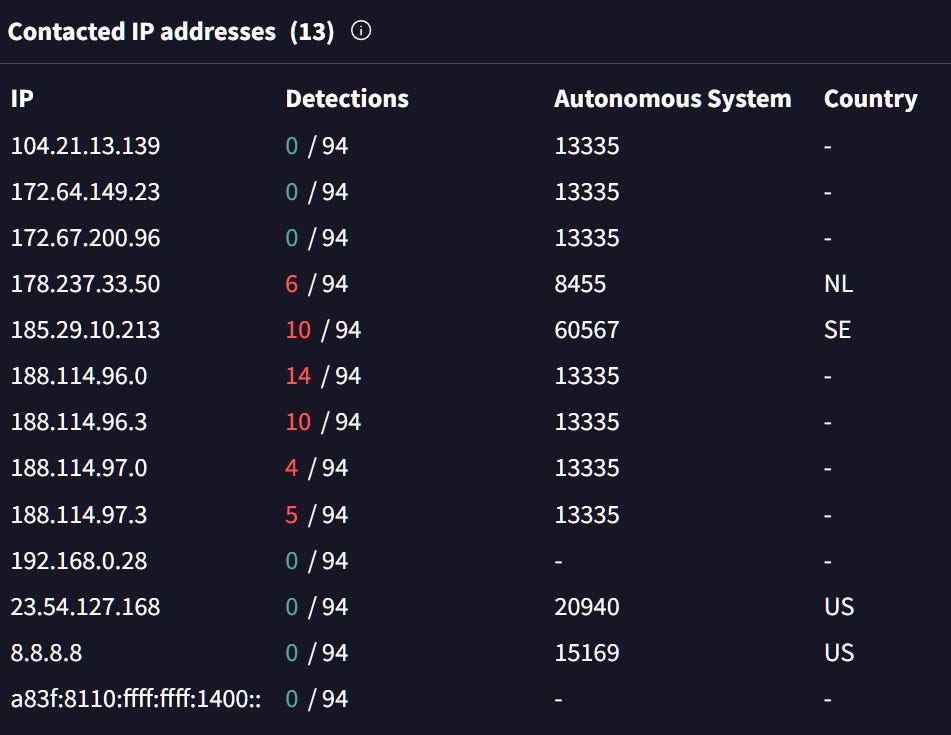
My initial pivots didn’t really lead me anywhere, so I went back to the malicious file and had another look at the communicating IPs. We can see that this particular malware sample communicates with 13 IPs.
AS13335 is owned by Cloudflare, so I will avoid it, as it’s very hard to pivot from.
Starting with the IP 178.237.33.50, the host has a couple of interesting services running on high ports. So I pivoted using the SSH fingerprint and ports combination, which led to 9 hosts—a more manageable number.
SSH Fingerprint & Port Combination
services.banner_hashes="sha256:a736ea626be1236a658cbd50fe41aa5b2874c1cd6168731f0379516d55017b7d" AND services.port:6556 AND services.port:2020From the resulting hosts only 2 IPs have been previously reported.
178.237.33[.]50
178.237.33[.]51Reviewing the remaining IPs, I found out that they are related with various malware/phishing/APT campaigns, indicating that this infrastructure is commonly used by Threat Actors so it’s very difficult to attribute and connect it to a specific malware.
Wrapping this up, as you can understand, not every hunt is straight forward and often might lead to absolute nothing or generate more questions than answers.
Since I cannot 100% attribute any of the IPs to Remcos, take the IOC with a grain of salt, aka Moderate Confidence.
As always, if any of you wants to collaborate and follow up on this, feel free to ping me @orlof_v
Thanks!
IOC
** Moderate Confidence **
# Services and ASN pivot
185.29.9[.]113
185.29.8[.]124
109.248.144[.]171
185.29.9[.]118
185.29.9[.]119
# SSH Fingerprint & Port Combination
95.142.100[.]71
165.227.209[.]82
178.237.33[.]34
178.237.33[.]50
178.237.33[.]51
178.237.35[.]186
178.250.238[.]75
178.250.238[.]76
208.109.38[.]215
** High Confidence **
# Malware Communicating IPs
178.237.33[.]50
185.29.10[.]213
188.114.96[.]0
188.114.96[.]3
188.114.97[.]0
188.114.97[.]3