Play it!
Legitimate services as C2
This investigation started with a single C2 URL found at a pastebin image.
The C2 was pointing at subscribe-supervision.gl[.]at.ply.gg, which resolves to 147,185.22.23
Community notes associate this IP with malwares njRAT and XWorm, so let’s understand these malware and their functions.
njRAT
NjRAT, also known as Bladabindi, is a remote access Trojan that has been widely weaponized by various threat actors for espionage and financial theft. Recent activity observed since March 2024 highlights its deployment via phishing campaigns, often utilizing malicious links in emails impersonating legitimate entities to entice victims into downloading malicious payloads. The malware is capable of stealing sensitive information through keylogging and screenshot capture, along with providing unauthorized remote access to infected systems
XWorm
Is a Remote Access Trojan, allowing cybercriminals to deploy various malicious functionalities including data theft, DDoS attacks, and remote control of infected systems. It is commonly delivered through multi-stage attacks involving phishing emails with malicious LNK files that execute PowerShell scripts to download additional payloads from remote servers
Analysis
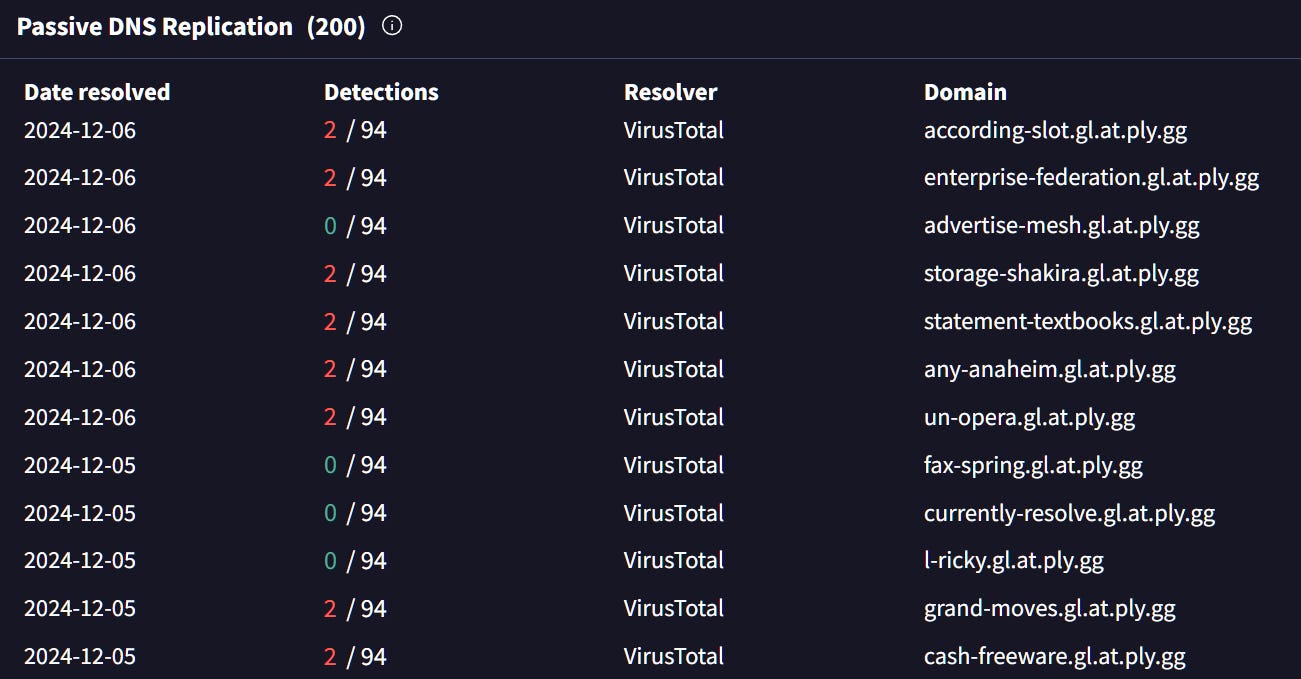
Now, let’s have a closer look at the domain/IP. Started by checking the Passive DNS resolutions on VT which indicate a naming pattern (ply.gg)
Most of those domains and associated IPs are flagged as malicious for either spreading or hosting some variable or RATs or other malware, I found relations with AsyncRAT, XWorm, njRAT, Razy, Cobalt Strike, SpyMax and many more mainly from AS400519, so I added this AS to the notes and moved on.
Additional checks on the C2 URL show many domains previously hosted or currently being hosted at the same server.
Investigating those domains further shows that all of the associated websites redirect to playit[.]gg.
Playit.gg
Is a legitimate tunneling service that helps users host game servers and other services from their home computers, making them accessible over the internet without needing to configure port forwarding or having a public IP address. As you can understand, this can be easily exploited by threat actors to hide C2 traffic in normal gaming traffic while using legitimate domain reputation and the service’s CDN.
Post installation, executing the program redirects to a URL https://playit[.]gg/claim/120b43bd72 which is used as an identifier and allows you to tunnel traffic.
The offering from playitgg service, matches the naming convention we saw at VT relations and the malwares behavior & use cases from threat actors related to infection through legitimate software distribution and Phishing/ DDoS attacks through infected machines.
Domain Pivoting
Looking closer one of the domains, ravstormdev[.]top, we can see that 5 IPs have previously hosted this domain. Those IPs host millions of domains and have been mentioned on various reports and are associated with both cybercrime and APT activity which outlines that malicious infrastructure is often used by many Threat Actors
Looking through all the domains is unfeasible so I focused on pivoting off of the IP instead.
IP Pivot
Starting with the first IP, we can see that there are many services running on the server, as expected since it’s the nature of the service.
Port 80 seems to be redirecting to playit webpage so we can use this filter to find additional hosts and look at the IPs distribution.
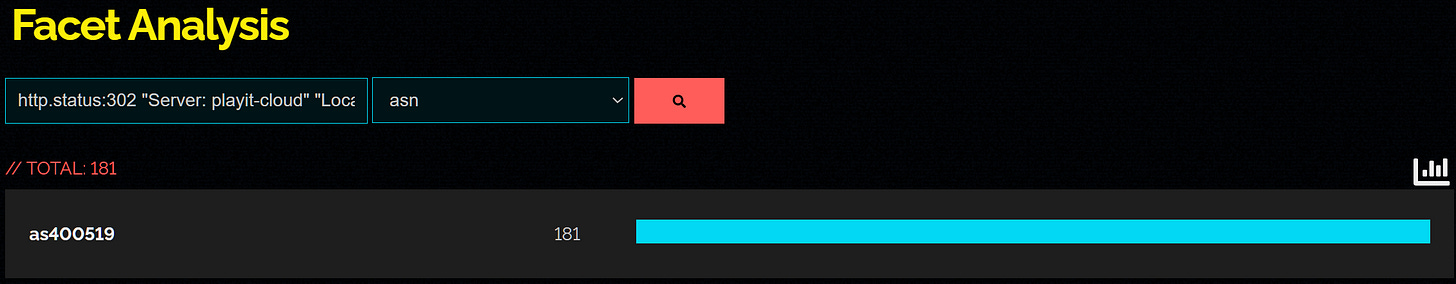
services.banner="HTTP/1.1 302 Moved Temporarily\nServer: playit-cloud\nLocation: https://playit.gg\n"The search returned 291 results in Censys, all of the hosts are part of the same AS called Playit-gg which maps to AS 40519 (if you remember this was a lead we noted before).
Similar results were obtained on Shodan as well.
http.status:302 "Server: playit-cloud" "Location: https://playit.gg"Additionally, looking at the passive DNS history we can try to follow the domains and map communicating files, files and related malware.
A single pivot from the the domain un-opera[.]gl.at.ply.gg which resolves at 185.199.110[.]153, hosting 308K domains, looking like phishing domains, so it opens another rabbit hole that I will probably go down another time.
Conclusion
After this analysis, I can say with high confidence that various threat actors are using the legitimate service playit.gg as infrastructure to host malicious & phishing domains, spread malware and hide C2 traffic. Activity is associated with APTs and cybercriminals with diverse agendas from monetary gain to influence operations and espionage.
IOC
# C2 URL from pastebin post
subscribe-supervision.gl.at.ply[.]gg
# Domains hosted at 147.185.221[.]23 redirecting to playit.gg
ravstormdev[.]top
cerealshub[.]online
amakusa[.]lat
furians[.]net
galaxy4dayz[.]com
onys[.]fun
powsync[.]com
ddzunlock[.]tech
empanabbo[.]xyz
galantoath[.]online
gaymershub[.]net
play-valorcraft[.]com
solodeus[.]xyz
skycams[.]top
retropixel[.]fun
remotosgsm19[.]tech
wefinddogs[.]com
# IPs associated with the above domains
147.185.221[.]23
188.114.97[.]3
188.114.96[.]3
3.33.130[.]190
15.197.148[.]33
# Passive DNS Historical data of IP 147.185.221[.]23
according-slot[.]gl.at.ply.gg
enterprise-federation[.]gl.at.ply.gg
advertise-mesh[.]gl.at.ply.gg
storage-shakira[.]gl.at.ply.gg
statement-textbooks[.]gl.at.ply.gg
any-anaheim[.]gl.at.ply.gg
un-opera[.]gl.at.ply.gg
fax-spring[.]gl.at.ply.gg
currently-resolve[.]gl.at.ply.gg
l-ricky[.]gl.at.ply.gg
grand-moves[.]gl.at.ply.gg
cash-freeware[.]gl.at.ply.gg
friends-temp[.]gl.at.ply.gg
al-concert[.]gl.at.ply.gg
cuzwedid[.]xyz
nopajamas[.]win
washington-favorites[.]gl.at.ply.gg
two-besides[.]gl.at.ply.gg
retropixel[.]fun
figure-complications[.]gl.at.ply.gg
flowers-ftp[.]gl.at.ply.gg
tibiszkuszrp[.]hu
rate-charlie[.]gl.at.ply.gg
designed-paragraph[.]gl.at.ply.gg
might-summaries[.]gl.at.ply.gg
lake-rate[.]gl.at.ply.gg
real-safe[.]gl.at.ply.gg
investment-progress[.]gl.at.ply.gg
photography-karen[.]gl.at.ply.gg
channel-delayed[.]gl.at.ply.gg