Intro
On May 21 a multi-nation coordinated attack against Lumma’s infostealer infrastructure was reported. The FBI, Microsoft’s digital crimes unit and many other companies and international partners joined forces to disrupt one of the most prolific infostealers.
The operation was a success, thousands of domains were taken offline and infrastructure was seized. In the coming days, many claimed that the malware would disappear and other infostealers were already taking the lead.
However, what I am seeing day after day is a completely different picture. It’s true that Lumma took a big hit but based on last month’s incidents, Lumma is still alive and well.
Show Must Go On
After the takedown operation, Lumma’s developers posted the following message, ensuring everyone that the operation will go on and functionality has been restored.
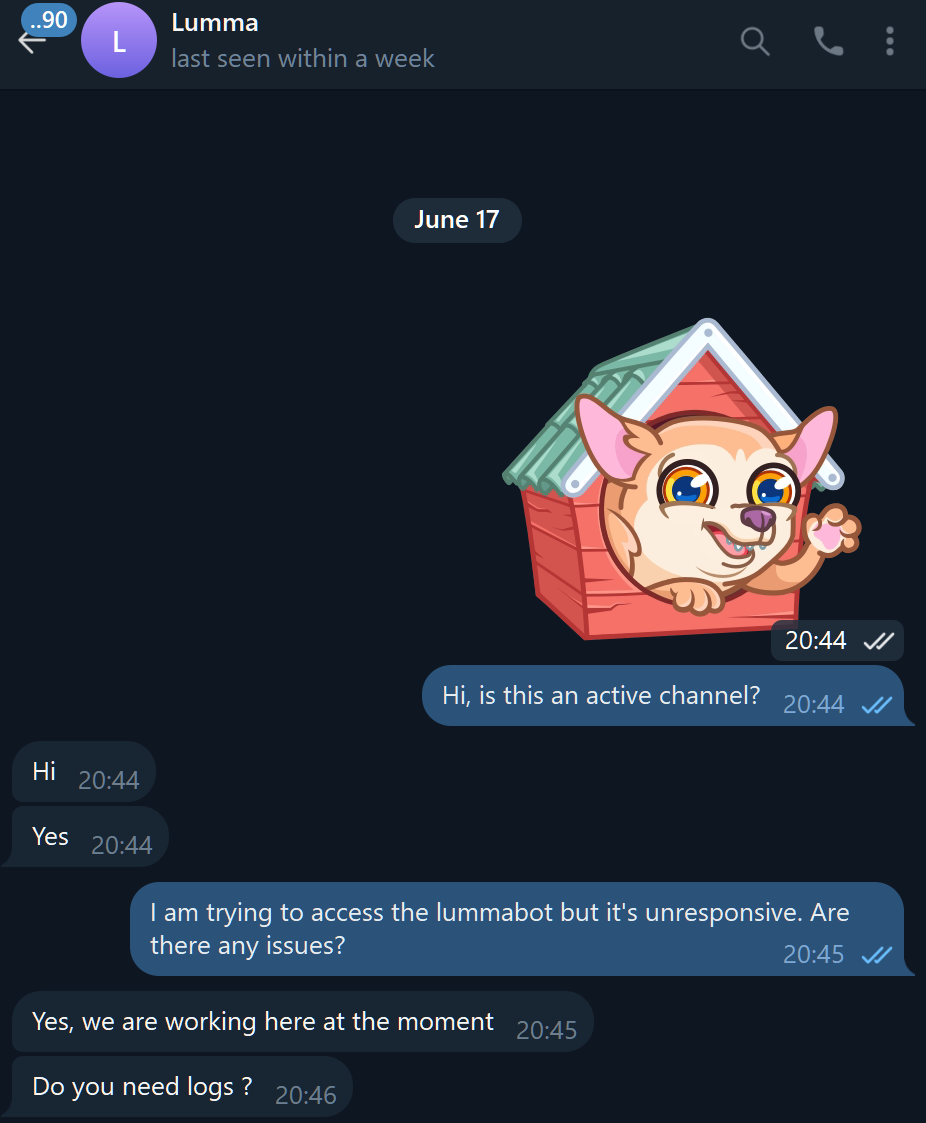
In addition to the message above, we can see that the malware is alive and well just by browsing their Lumma Logs Market Bot, which lists infection times after the operation (21/5). However, this could be an older strain still being used to infect devices, but it’s not! Proof that the malware is actively developed come from the malware logs of infected devices, which show the version of the infostealer used on the system.
Lumma Operation Structure
Let’s start by mapping the core setup of the Lumma infostealer. Conveniently, they have gathered all their contact info and channels in a usrlink page comprised by the Seller | Bugs | Logs Market
Lumma Seller
@lummaseller128
This is the channel that the actual sell of the infostealer takes place. The details of the malware (build, coding language, size, etc.) can be found in a description page, along with the pricing for the plans, conveniently hosted on telegra.ph which requires no registration.
Experienced - Price: $250 / month
Professional - Price: $500 / month
Corporate - Price: $ 1000 / month
Logs Market
@lummamarketplace_bot
In this channel, the malware logs are being sold, containing the actual loot of the infections. Passwords, Cookies, etc. can be found in those logs. Specific filters can be applied to narrow down your search and show only relevant logs. Users can filter for things like crypto wallets, cookies or even specific countries for as low as 1$.
Lumma Support
@lummamarketsupport
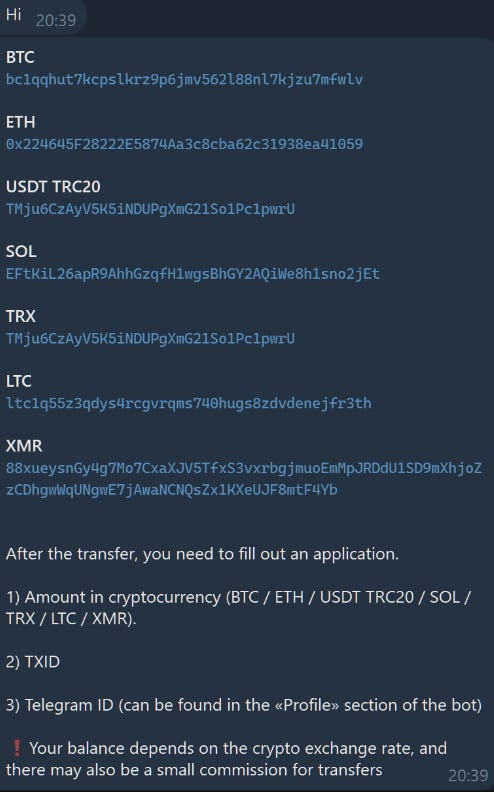
Finally, there is the lumma support channel, that assists users with their purchases and finance. You can top up your account by adding funds in on of the provided addresses.
Backup Channel
@zevsup
Another channel that was active after the takedown operation is called Lumma and it seems to be acting as a backup channel in case the bot stops working.
Analysis
Country Distribution
Now that we covered the high level structure, we can focus on the data. Based on the market bot there are 10.6K results, meaning around 10.6 infected devices although I am sure there will be some duplicates. By querying the bot we can easily get an understanding of the infection distribution based on countries.
It’s worth noting that infection times are registered long after the takedown operation.
Following the money
Since the Lumma support was kind enough to provide the crypto deposit address I thought it would be interesting to review them and get a rough estimation of the deposited amount on their addresses (although the addresses change).
The total amount is around 16K at the time of this writing exlcuding the XMR address which does not allow users to know the exact amount of XMR in an address.
BTC: bc1qqhut7kcpslkrz9p6jmv562l88nl7kjzu7mfwlv
ETH: 0x224645F28222E5874Aa3c8cba62c31938ea41059
USDT TRC20: TMju6CzAyV5K5iNDUPgXmG21So1Pc1pwrU
SOL: EFtKiL26apR9AhhGzqfH1wgsBhGY2AQiWe8h1sno2jEt
TRX: TMju6CzAyV5K5iNDUPgXmG21So1Pc1pwrU
LTC: ltc1q55z3qdys4rcgvrqms740hugs8zdvdenejfr3th
XMR:
88xueysnGy4g7Mo7CxaXJV5TfxS3vxrbgjmuoEmMpJRDdU1SD9mXhjoZzCDhgwWqUNgwE7jAwaNCNQsZx1KXeUJF8mtF4YbAs expected, some of the BTC addresses associated with the deposit address are associated with known malicious activity like the Conti ransomware, indicating that affiliates are diversifying their opportunistic attacks (ransomware & infostealers).
Lolzteam & Lumma
This is where things got really interesting. Reviewing malware logs, post-takedown operation, I found many infections that had an extra description in their ‘System.txt’ file which was redirecting to Telegram channel/accounts unrelated with the “official” Lumma operations.
The above roughly translates to:
”Brute-force crypto wallets | check cryptowallets/seed-phrase Minimal balance $3000
Contacts - @expirepm
I'll buy your YouTube channels in large volumes! Working in this field for more than 6 years and can confidently say that only working with us will you be able to sell your YouTube channels and get maximum profit. To regular sellers we provide the best price on the market for any channel + % from streaming. Our team is available 24/7
TG: https://t[.]me/ytmilanyt”
Following the contacts leads to 2 unique channels.
Lolzteam Marketplace
First is the Lolzteam Marketplace (also known as LZT), a major Russian language cybercriminal forum.
This platform hosts :
“Traffers" operations: Cybercriminals who distribute malware through compromised social media accounts with large followings
Account trading: Gaming, social media, and streaming platform accounts
Stolen data sales: Including infostealers, credential databases, and account credentials
Cybercriminal services
Which match perfectly with infostealer operations as it can be used to monetize stolen credentials or accounts!
Russia 34
The second is another Telegram channel, called Russia 34 that seems to be a log marketplace with heavy concentration in .com domains (4500+), followed by Germany, France, and Italy. "Base 34" appears to be the campaign or group identifier and they seem to offer "checked" (verified working) accounts from global infostealer accounts.
Closing Thoughts
After writing this, I came to these 2 conclusions:
#1 Established malware operations have better built-in redundancy than Fortune 500 companies
#2 Integrations between cybercrime ecosystems creates a self sustaining economy
As always, there are many stones left unturned and I will probably follow up on this with some threat hunting and IoC but for now I’ll leave it at this.
Special thanks to the 10 people who actually read the entire post, really appreciate you!
Take care and stay safe!