Intel Drops #4
Phishing kit targeting MS login pages
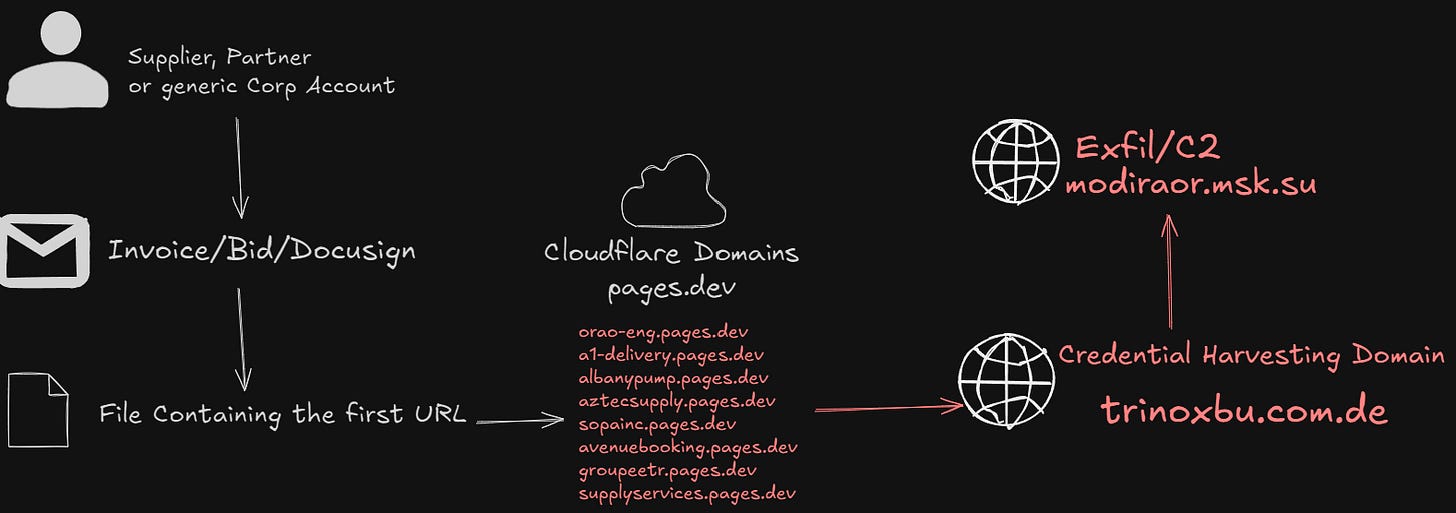
Ongoing phishing campaign hosted on Cloudflare infra, using pages.dev domains and captcha challenges, targeting Microsoft login pages.
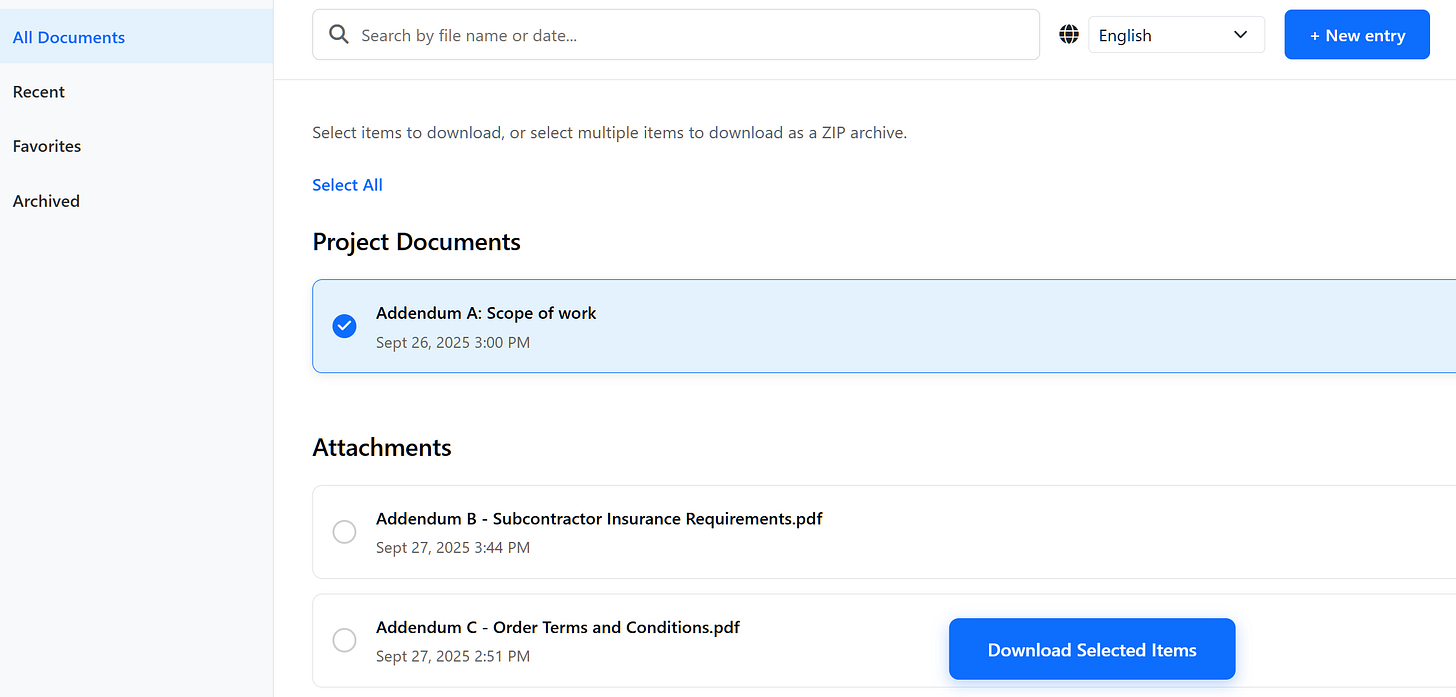
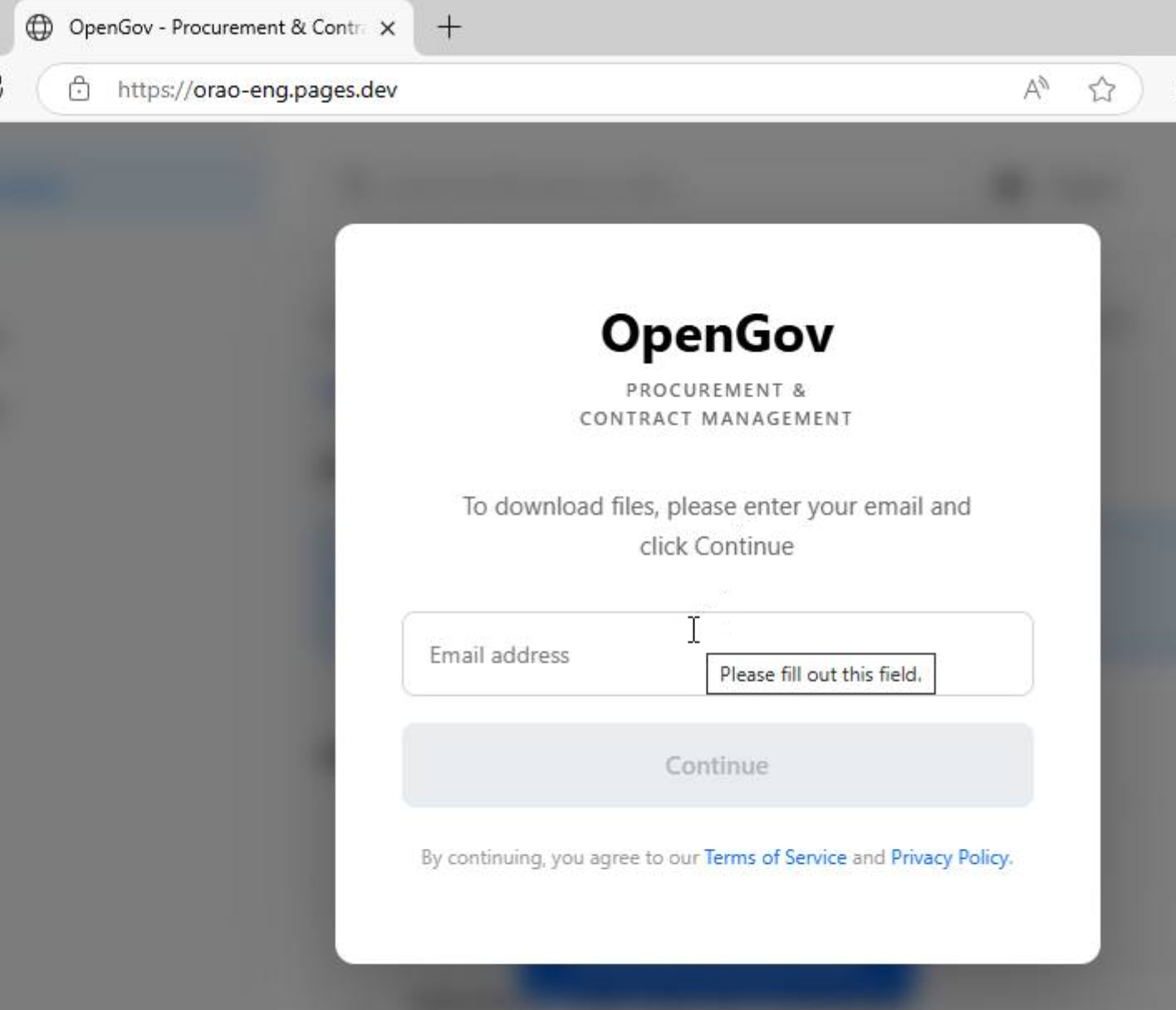
The attack starts with emails using subjects themed around bids, invoices or documents requiring signature. The emails, contain URL that redirects to fake OpenGov sites, prompting users to enter their credentials before they can download a file.
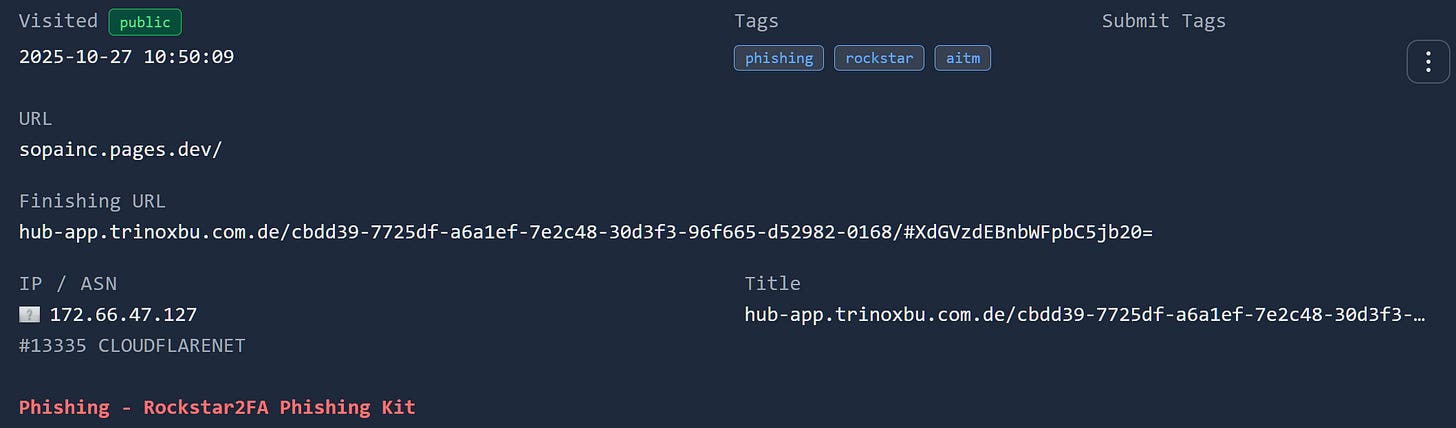
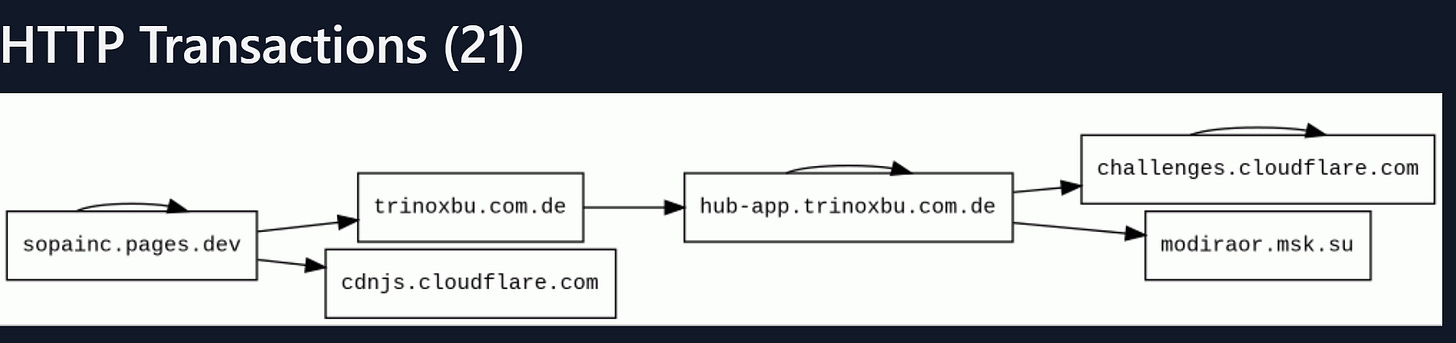
Running the url through urlquery, returns a potential match with the Rockstar2FA kit, along with the http transaction flow
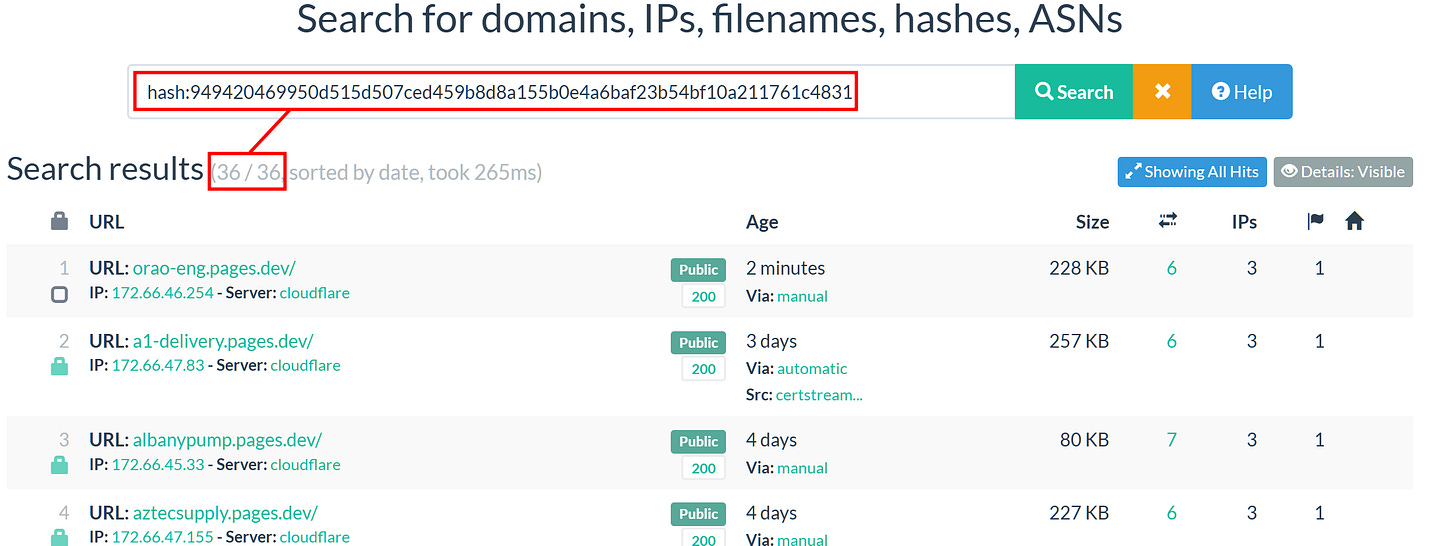
We can further expand on the pages hosting the redirection URL by pivoting on a website component hash using urlscan
Please reach out if you have worked on similar phishing kits or if you have more IoC to share related with this campaign.
That’s all, have a nice week and take care.
IOC
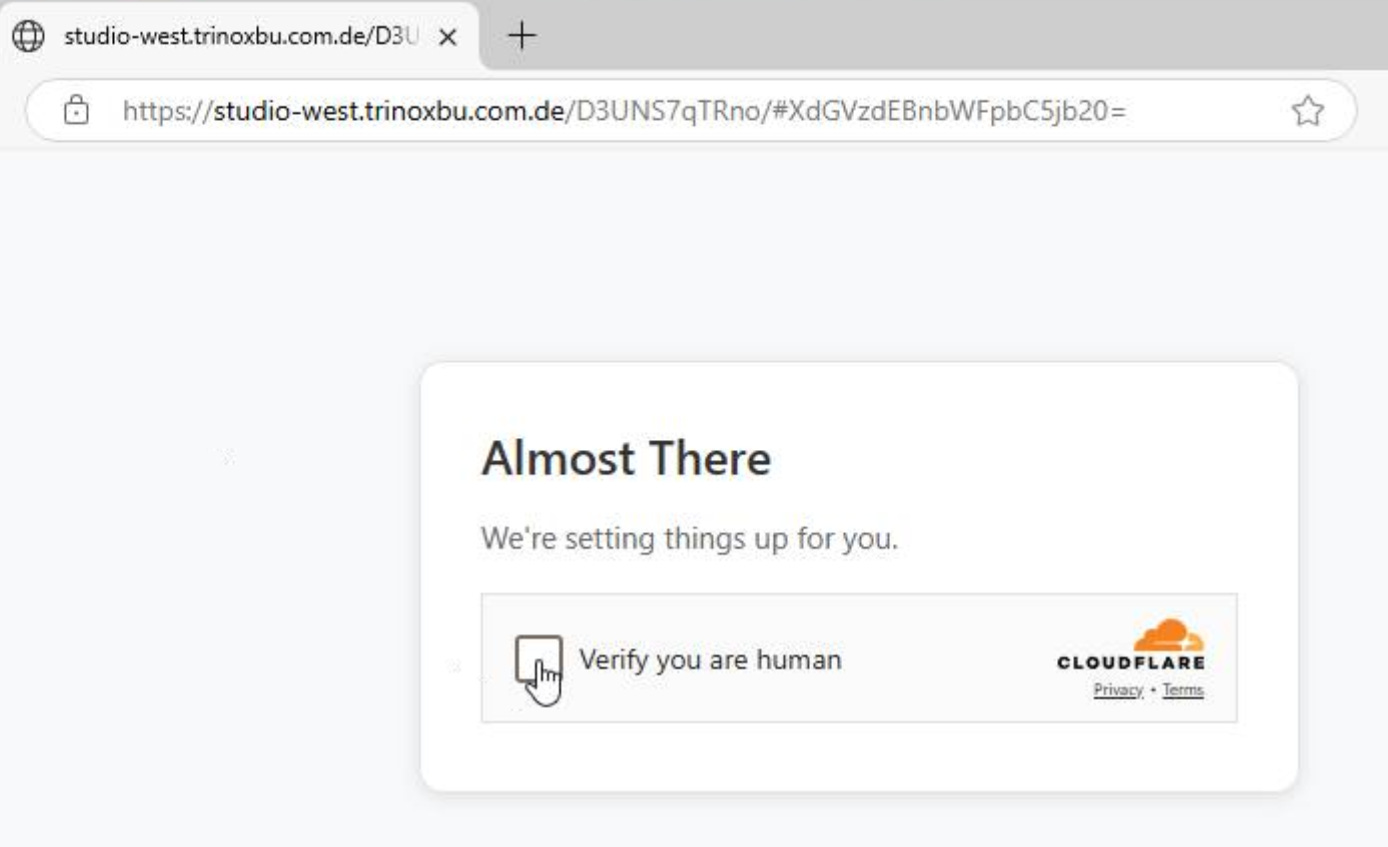
trinoxbu.com.de
modiraor.msk.su
orao-eng.pages.dev
a1-delivery.pages.dev
albanypump.pages.dev
aztecsupply.pages.dev
sopainc.pages.dev
avenuebooking.pages.dev
groupeetr.pages.dev
supplyservices.pages.dev
tenaquip.pages.dev
apresfurniture.pages.dev
emercom.pages.dev
emercom.pages.dev
rmsme.pages.dev
wilsongroup.pages.dev
thinkconfluence.pages.dev
pmi-group.pages.dev
essemgroup.pages.dev
supplyservices.pages.dev
supplyservices.pages.dev
tarpmakers.pages.dev
mountmetalcraft.pages.dev
trapenliftservice.pages.dev
apexa-bid.pages.dev
csshl-gouv.pages.dev
mtlpropane.pages.dev
mtlpropane.pages.dev
kza-qc-ca.pages.dev
cssob-gouv.pages.dev
mtlpropane.pages.dev
cssob-gouv.pages.dev
csshl-gouv-qc.pages.dev
cssob-gouv.pages.dev
csshl-gouv-qc.pages.dev
groupeabs.pages.dev
minotaurquebec.pages.dev
transitionquebec.pages.dev

Thank you!