Intel Drops #1
July phishing campaign
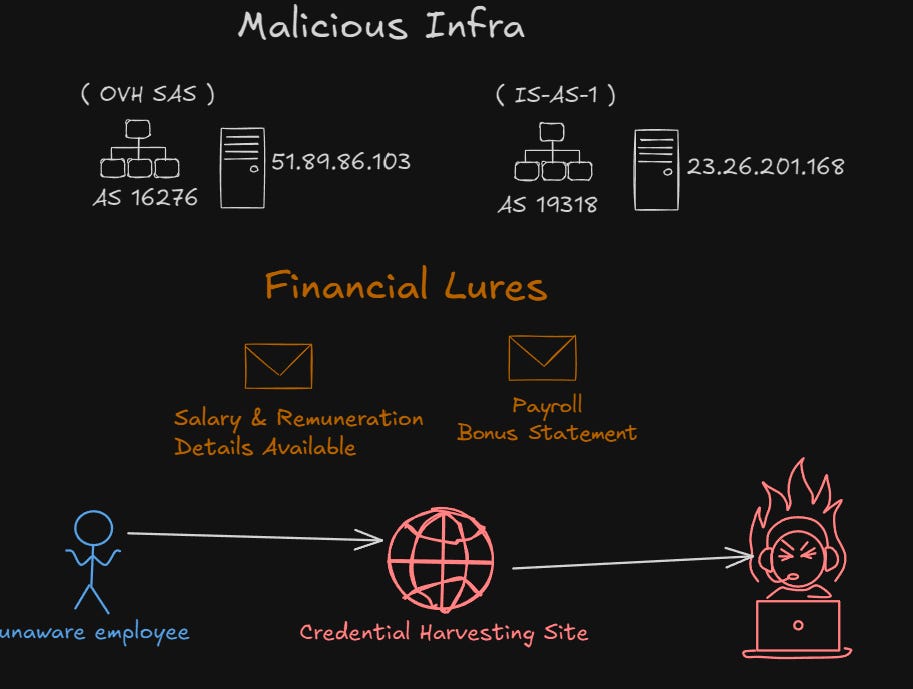
There is an active phishing campaign targeting EU and US companies, originating from 51.89.86.103 and 23.26.201.168
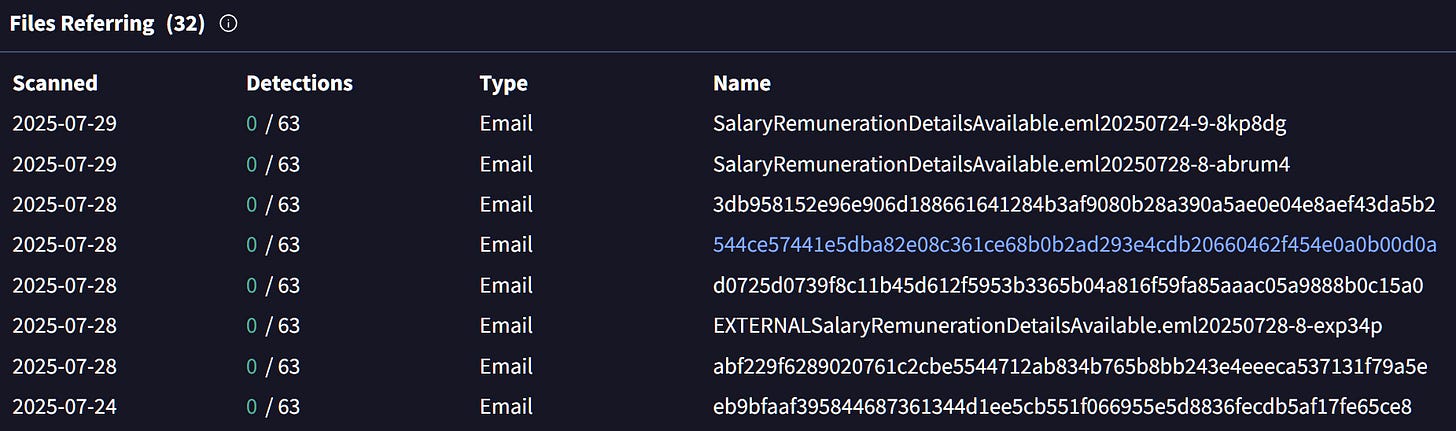
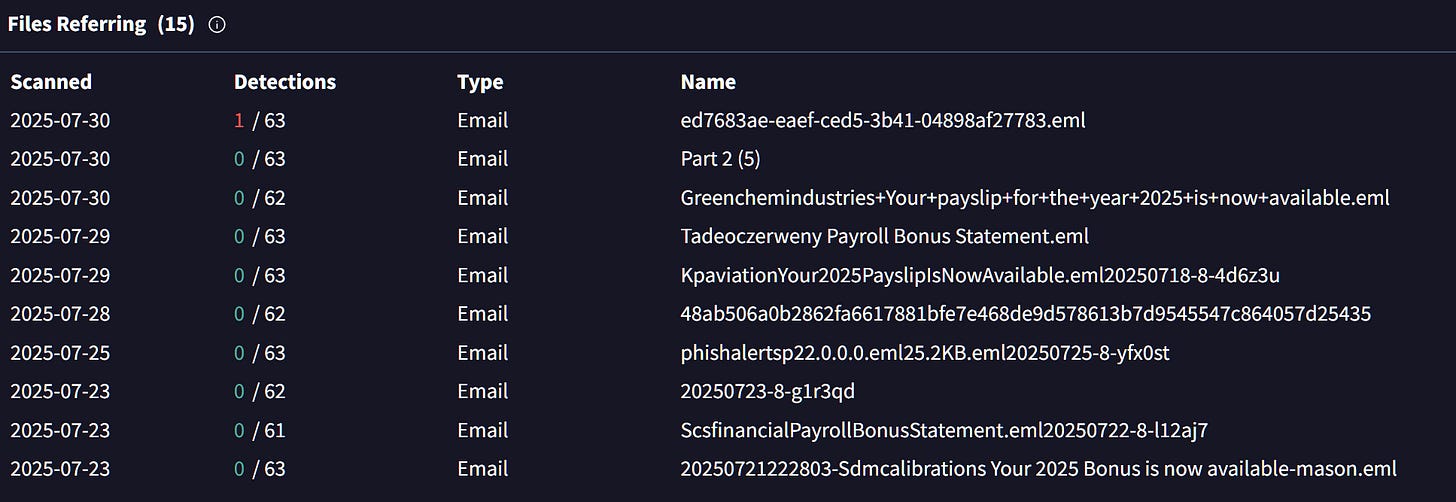
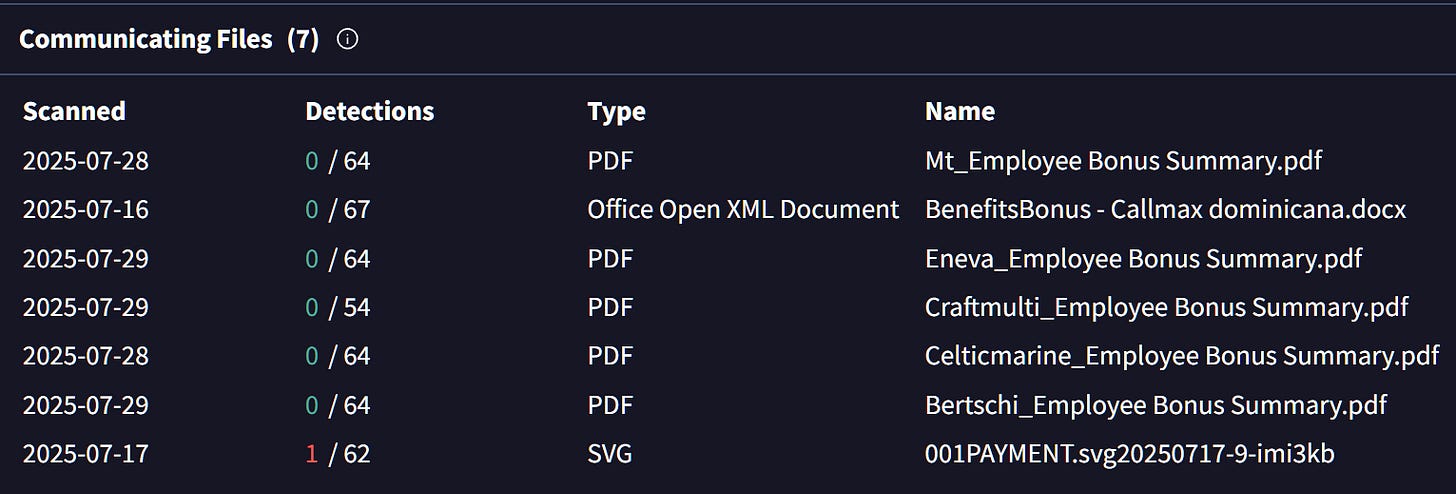
Having a closer look at the IPs, we can immediatly see that there are hundreds of eml files referring them. Some are shared as eml file hash but others include the name which clearly shows the financial lure theme.
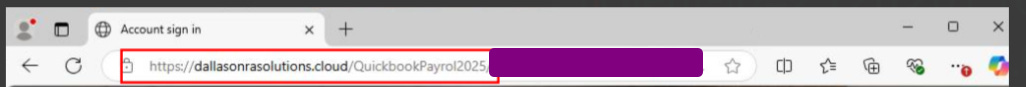
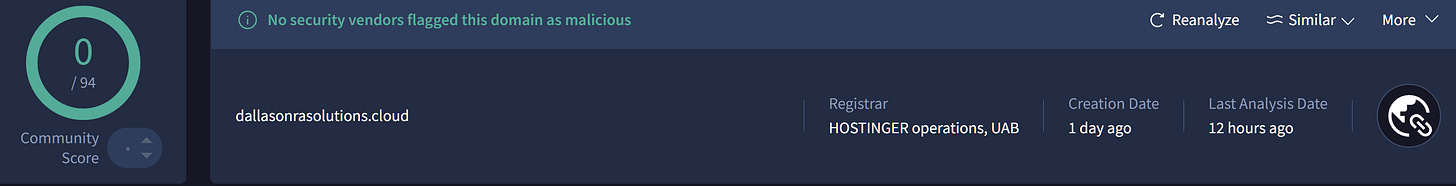
The emails contain a pdf file and within the file there a QR code which redirects to identical credential harvesting websites “dallasonrasolutions[.]cloud &
withbible[.]com”
The first domain was registered one day ago which raises flags on it’s own, while the second domain was created 14 years ago indicating a possible breach of the domain that is now used as a landing page for the campaign, this hypothesis is further supported by the files communicating with the domain.
Campaign Analysis
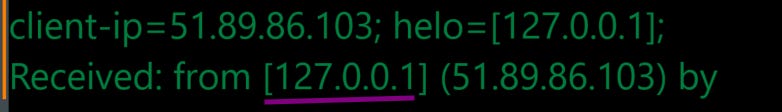
The reason I think this is a single campaign is based on the similarities in the financial nature of the email lures along with the identical credential harvesting sites. Finally, analyzing the email headers shows that the same HELO message is used in both instances.
IoC
dallasonrasolutions.cloud
withbible.com
51.89.86.103
23.26.201.168




Interesting, thank you!