Hunting Pandas
Uncovering massive Red Delta, APT41 infrastructure and possible overlaps
It all started with the malware analysis report by somedieyoung linking the malware to Mustang Panda/Red Delta.
TL;DR : If you don’t care about the analysis and you want to take my word for it here is the Full IoC list
Mustang Panda
Mustang Panda is a China-based cyber espionage threat actor that was first observed in 2017 but may have been conducting operations since at least 2014. Mustang Panda has targeted government entities, nonprofits, religious, and other non-governmental organizations in the U.S., Europe, Mongolia, Myanmar, Pakistan, and Vietnam, among others.
Analysis
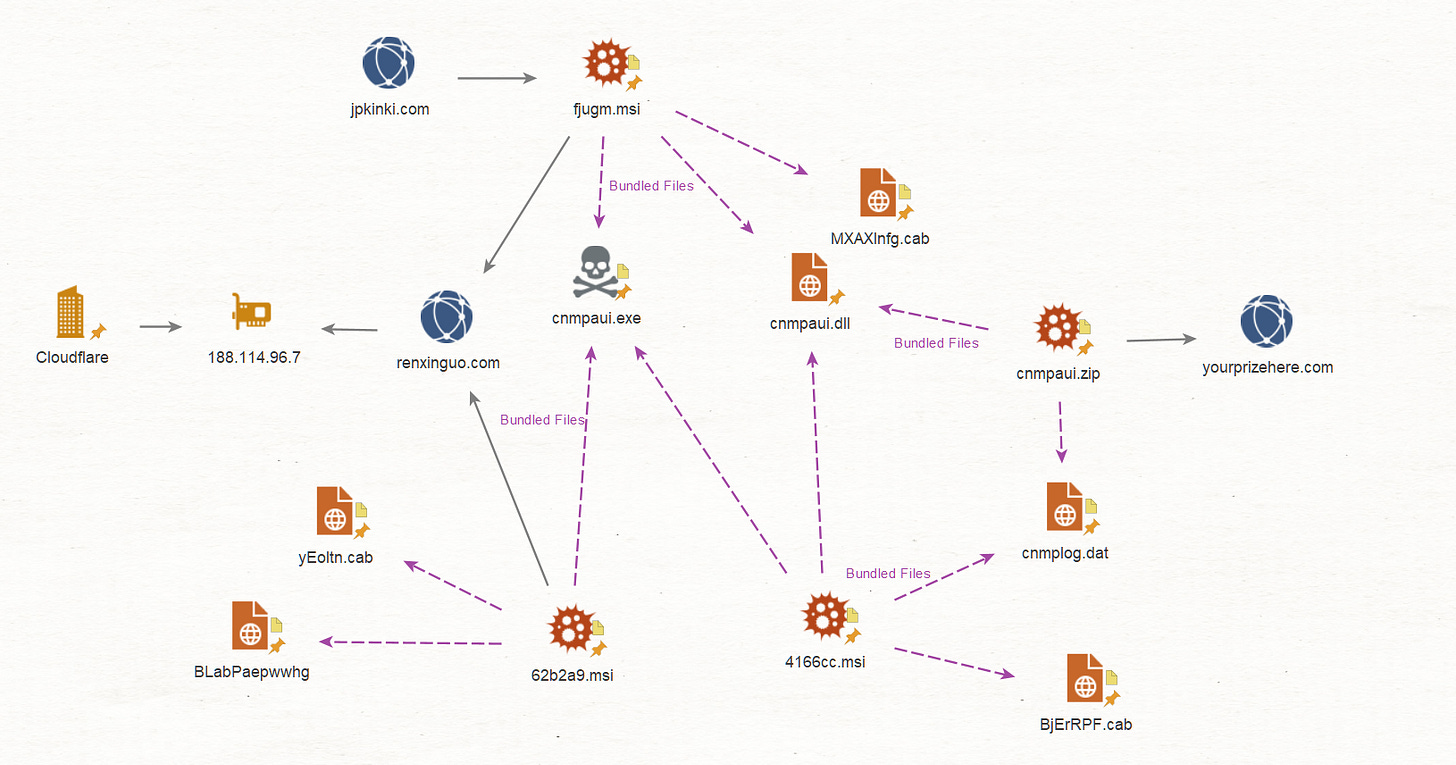
Using the report we can generate the following IoC diagram (you can read the full analysis here)
We’ll begin our hunt at the first domain found in the malware analysis, jpkinki[.]com hosted at 139.180.192[.]163. When it comes to IPs, I will completely ignore Cloudflare’s ASN as we can’t really pivot from them.
jpkinki.com
139.180.192.163Host Banner Pivot
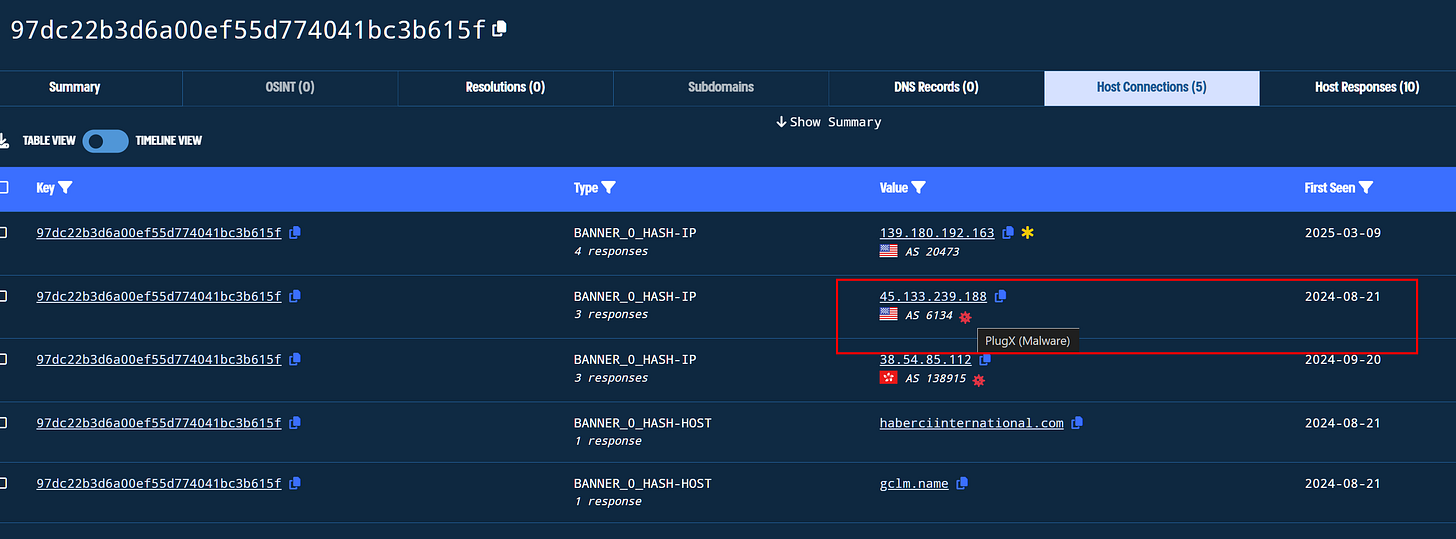
Using Validin we can review the domain for interesting pivots. The host banners pivot, gets us 5 findings (4 new Ioc) some of which have been previously tagged as PlugX indicating we are in the right path.
After the last update, Validin conveniently groups the results in different pages making it easier to review and pivot. In our case the host response banner was captured for port 443 and 8088 giving us 2 unique Banner Hashes.
To expand our findings we’ll go over the result pages, pivot on the Banner Hash and start grouping our findings.
First stop, ASN grouping to check if the threat actor is favoring specific ASN for their infra deployment.
# Host Banner 97dc22b3d6a00ef55d774041bc3b615f
139.180.192.163 - AS 20473
45.133.239.188 - AS 6134
38.54.85.112 - AS 138915
haberciinternational.com
gclm.name
# Host Banner e30fb7845d2cda285b40e57001cfdb71
139.180.192.163 - AS 20473
45.133.239.188 - AS 6134
45.32.105.184 - AS 20473
173.199.71.152 - AS 20473
45.152.65.213 - AS 139659
103.79.120.89 - AS 137443
45.152.66.25 - AS 139659
haberciinternational.com
83.229.127.115 - AS 139659
38.89.72.133 - AS 174Sure enough, there are some overlaps on the AS which is something that might help us create a hunting rule.
→ AS 139659
→ AS 20473
JARM Pivot
Since we see a pattern forming regarding the ASN, we’ll follow that trail. Examining the host 45.76.132[.]25 we can see an interesting pivot on the JARM Fingerprint, leading us to additional findings. Some of them matching our previous rules and some already reported as PlugX malware (used by Mustang Panda / RedDelta)
07d0bd16d21d21d07c07d0bd07d21dd7fc4c7c6ef19b77a4ca0787979cdc13Now armed with more indicators, we can create groupings and focus on the hosts of the top 3 AS to create new associations and patterns that will lead us to additional infrastructure.
Validin generates the Header Hash and Banner Hash based on the keys in the header of HTTP responses which, in combination with the JARM makes them a very good pivot point.
Response Banners + JARM + ASN
After analysing all the banner and header responses I gathered the following interesting data per AS.
AS 20473
nginx/1.22.1
Header Hash : d7001d5eaca56712100c
JARM : 2ad2ad0002ad2ad00042d42d00000000f78d2dc0ce6e5bbc5b8149a4872356
JARM : 2ad2ad0002ad2ad22c2ad2ad2ad2ad703dc1bf20eb9604decefea997eabff7Pivoting on the Header Hash returns 12 unique hosts matching our parameters, some already associated with PlugX so I would say these findings can be attributed to the threat actor with high confidence.
166.88.117.11
103.79.120.67
103.79.120.70
45.195.69.111
103.79.120.74
139.180.192.163
223.26.52.245
146.66.215.19
103.79.120.71
103.79.120.85
96.43.101.248
103.79.120.69AS 135377
The JARM associated with the finding on this AS is the one we saw earlier so I focused on other findings. The Header Hash 74003aa800b6e7effc1c returns over 400 IPs & domains heavily associated with PlugX, RedDelta (Mustang Panda) and more interestingly APT41 indicating a potential overlap.
* APT41 is known for conducting both state-sponsored espionage and financially motivated operations, while RedDelta has been reported to target government entities and utilize malware
** The results from this pivot might include some False Positives so I’ll include these findings under “Medium Confidence” section on the IoC list
74003aa800b6e7effc1c
07d0bd16d21d21d07c07d0bd07d21dd7fc4c7c6ef19b77a4ca0787979cdc13
Conclusion
We started from a few indicators associated with Red Delta infra and through pivoting we managed to discover additional infra and potential operational overlaps between Red Delta and APT41.
Thanks to all 3 people that made it to the end of the post. Take care!
Special thanks to Michal Koczwara for sharing the initial report that launched this investigation and Kenneth Kinion for his support with the Validin Platform.