Gone Phishing
Hunting Rhadamanthys Infrastructure in the 2024 Holiday Season
As the holiday season approaches, threat actors are increasing the deployment of infostealer campaigns (among others), with a particular focus on exploiting trusted travel and shopping platforms.
Twitter user JAMESWT_MHT reported a malicious PDF attached to a phishing email. The reported file contains the Rhadamanthys infostealer.
Rhadamanthys
Is an infostealer malware primarily delivered through phishing campaigns that leverage social engineering tactics. It has gained notoriety for its rapid iterations, with the most recent version (0.7.0) released in June 2024, incorporating sophisticated features like AI powered optical character recognition (OCR) for extracting cryptocurrency wallet seed phrases from images. The malware typically infiltrates systems via password protected ZIP files containing LNK files that execute malicious PowerShell scripts to download the stealer directly into memory.
Analysis
Using Censys and the IP associated with the sample I performed a few pivots that led to additional malicious infrastructure used by the Rhadamanthys malware.
Examining the reported IP and the service running on port 7257 (HTTP) I was able to uncover 18 new servers matching the exact value.
Services Banner
First pivot was done by looking at services banner in Censys, what we're actually seeing is the initial response a server sends back when something tries to connect to it.
services.banner="HTTP/1.1 404 Not Found\r\nContent-Type: text/html\r\nServer: Microsoft-IIS/8.0\r\nDate: <REDACTED>\r\nContent-Length: 166\r\n"This result, gives us some information. For example, we know the server is using HTTP 1.1 and reveals that this is Microsoft's Internet Information Services web server, specifically version 8.0. This is particularly interesting because IIS 8.0 was released with Windows Server 2012, which gives us information about the likely operating system.
From the resulting 18 servers most were already reported as malicious and some have been already associated with the Rhadamanthys infostealer, others have not been flagged yet, indicating either newly provisioned infrastructure or a coincidence simply matching the services banners.
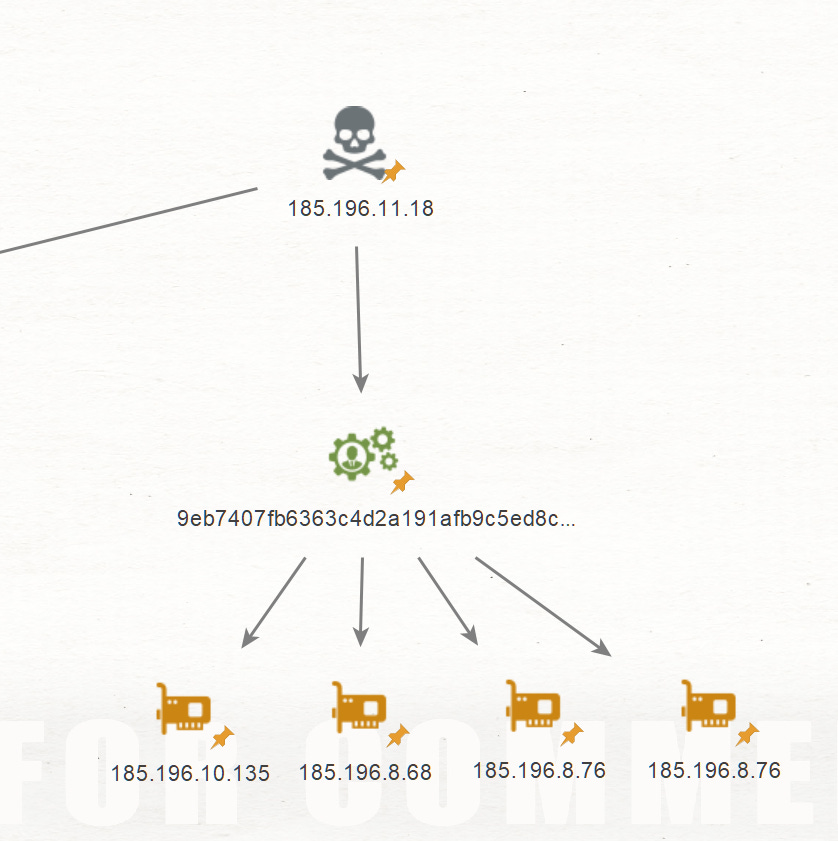
Services Certificate
The next pivot was done by looking at the services certificate. When looking at the certifate we are basically looking at a SHA-256 hash of the server's TLS/SSL certificate. This hash acts like a unique fingerprint for that specific certificate.
services.certificate="9eb7407fb6363c4d2a191afb9c5ed8cb16c41a68a87d60fa7dc6294f6b2c4892"The search returned 4 servers running MS server 2012, even though those IPs were not associated with Rhadamanthys malware, we can say with high confidence that it’s actually associated, based on the service certificate and the above finding related to the service banner.
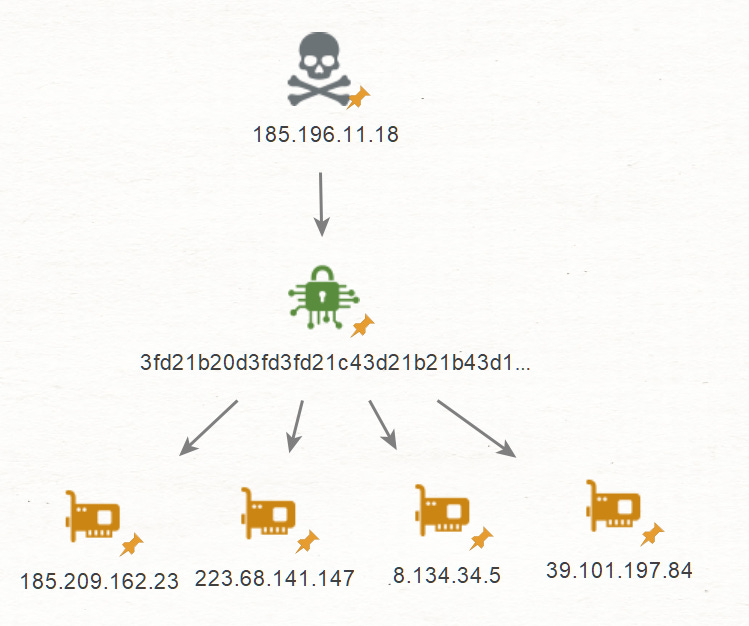
Jarm Fingerprint
Finally, the last pivot was performed based on
- JARM Fingerprint
- OpenSSH 8.0
- Port 22
- OS server 2012
The JARM fingerprint (3fd21b20d3fd3fd21c43d21b21b43d1ec49a4b64df0a9e9f328abd60285841) acts like a digital signature that identifies how a server handles TLS/SSL connections. This helps us identify servers configured in a particular way. The OpenSSH 8.0 software specification tells us exactly which version of SSH server software is running, the port 22 is a bit redundant but anyway :)
Windows Server 2012 CPE identifier tells us the exact operating system running on these servers which is a crucial parameter of our hypothesis.
services.jarm.fingerprint:"3fd21b20d3fd3fd21c43d21b21b43d1ec49a4b64df0a9e9f328abd60285841" AND services.software.uniform_resource_identifier:"cpe:2.3:a:openbsd:openssh:8.0:*:*:*:*:*:*:*" AND services.port:22 AND services.software.uniform_resource_identifier:"cpe:2.3:o:microsoft:windows_server_2012:*:*:*:*:*:*:*:*"This returned 8 hosts, 4 of them were not picked up in our previous pivots, outlining the importance of looking through multiple angles.
And that’s all folks. This is just the tip of the iceberg, these campaigns are massive and the infrastructure is vast. As always, many more paths to be explored and rabbit holes to fall down to, so feel free to reach out if you are interested.
Take care!
IOC
# Services Banner Pivot
88[.]210.12.126
103[.]148.58.151
104[.]37.175.232
185[.]234.216.132
154[.]216.19.192
193[.]124.205.63
103[.]148.58.152
45[.]200.149.186
179[.]61.251.153
38[.]55.97.42
45[.]155.220.96
45[.]200.149.72
154[.]216.19.192
185[.]196.8.68
185[.]196.8.56
# Services Certificate Pivot
185[.]196.10.135
185[.]196.8.68
185[.]196.8.76
185[.]196.11.18
# JARM Pivot
185.209.162[.]23
223.68.141[.]147
8.134.34[.]5
39.101.197[.]84