This weekend I set out to review and search for Cobalt Strike infrastructure.
As always, I started at Censys with a very broad and general search that I knew would return many results, the aim was to understand the distribution and start narrowing down my search. Basically the query requests all instances that have been tagged as cobalt strike.
services.software.uniform_resource_identifier: `cpe:2.3:a:fortra:cobalt_strike:*:*:*:*:*:*:*:*`As expected, the search returned many hosts (939). When I am faced with such a large number of results, I always try to perform various groupings to help me digest the information. For example, grouping the hosts by Country helps us understand that there is a very high concentration in China, followed by the US.
We can also group the hosts based on their AS to gain additional information and enrich or create hunting rules if needed.
Another pivot could be done by grouping by SSH host fingerprint, this pivot can help us with alert & rule creation as it’s more targeted to a single threat actor. The search shows that some hosts share an SSH host fingerprint which means that they have been probably provisioned by the same threat actor.
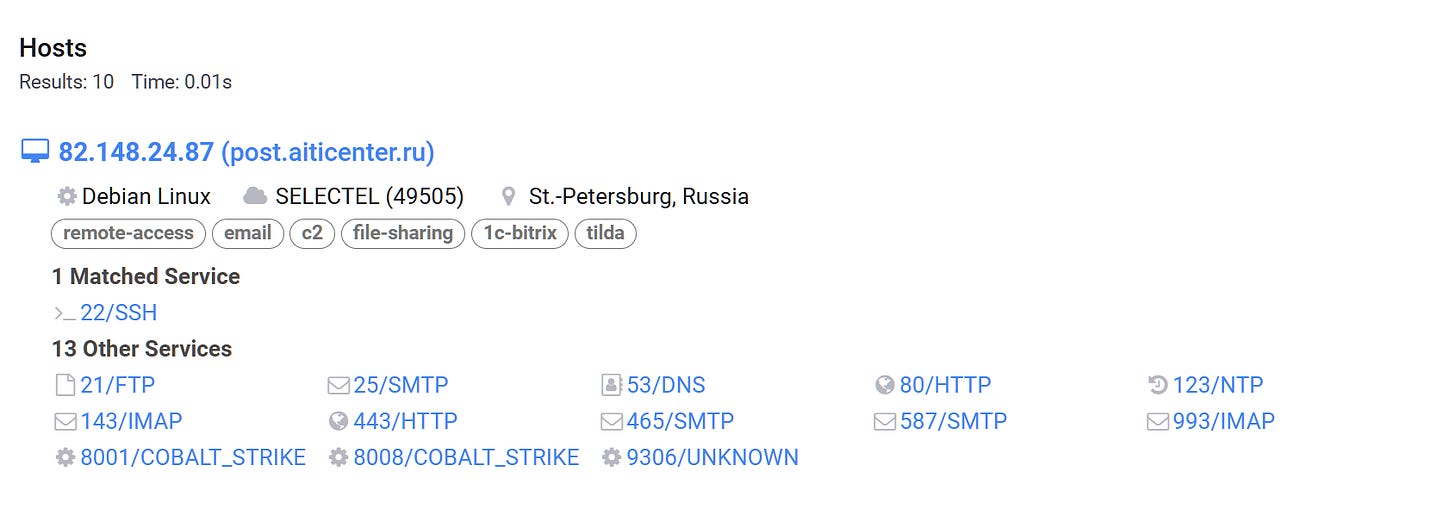
Following the first result, we get 10 hosts, located in Russia sharing the same SSH host fingerprint.
services.ssh.server_host_key.fingerprint_sha256=`bf12cbd5e656c01ba279acf549a6d5131d3253bf0cb4cb3467d106bbaee80a80`Most of the IPs have been previously reported and some are returning as clean which could be a FP or undetected infrastructure.
Using information obtained by our last search we can further improve our search queries and focus more on similar infrastructure, a good way to do that is through the use of the “watermark” field that is associated with Cobalt Strike deployments and indicates the deployed version. In this case the watermark indicates the version 4.7 that was deployed around October 2022.
It’s worth mentioning that we can use the same logic to identify cracked versions of Cobalt Strike by using the watermark “0”.
But anyway, I am rabbit holing, going back to the start of this blog, I wanted to have a look at the initial findings to try and uncover newly unregistered Cobalt Strike servers.
So, while looking through the findings, I noticed many hosts sharing the same values in the services banner field, regardless of the port. So I pivoted off of the services banner to see where it would get me.
The search returned 397 results, using a script I cross referenced the new findings with the initial 939 hosts and found 85 instances with low or no detections in Virus Total and Threat Fox running Cobalt Strike on various ports, so I can confidently say that we have successfully found new and undetected Cobalt Strike infrastructure.
As always, I am certain there are many leads to follow and things I missed so please expand on it and feel free to reach out, I truly appreciate feedback.
Thanks!
# New Cobalt Strike Instances
47.92.77.57:443
61.135.130.190:443
1.94.97.56:4433
45.145.229.234:443
120.79.135.77:443
61.135.130.191:443
47.84.94.67:8080
211.149.243.119:10443
1.94.141.87:50050
47.83.233.177:443
1.94.6.24:4444
38.46.12.68:14250
1.94.113.115:443
113.45.153.104:443
23.94.133.94:55554
218.30.103.192:443
148.135.44.218:4433
47.92.87.62:8443
123.57.245.136:8888
45.137.81.84:443
218.30.103.198:443
47.92.130.102:443
43.202.33.84:80
45.77.33.25:443
94.20.88.63:443
218.30.103.182:443
23.27.101.82:80
42.51.44.43:50050
82.67.60.21:80
218.30.103.130:443
44.193.202.139:443
118.89.198.206:2087
80.64.30.50:13371
81.71.13.76:7777
61.135.130.179:444
44.214.15.225:443
74.48.77.147:443
3.15.169.57:443
121.40.120.206:80
20.42.96.49:443
34.30.72.38:60001
103.234.72.56:443
23.95.85.51:443
103.140.186.155:443
2.56.125.55:443
45.119.99.5:50443
104.131.174.71:443
35.232.8.38:80
36.133.19.66:10250
218.30.103.189:443
154.12.82.72:80
47.92.213.224:443
218.30.103.168:443
118.25.85.56:443
101.35.210.224:59443
52.56.196.38:443
154.201.87.109:18084
106.38.201.40:8443
36.133.18.101:10250
45.43.54.62:8443
18.234.229.2:443
44.222.217.17:80
47.122.69.106:443
64.225.127.146:443
124.71.0.187:8443
99.79.73.121:443
167.179.81.6:4433
47.92.29.21:9999
3.236.59.222:443
119.45.251.70:80
3.230.115.153:443
47.92.92.147:443
64.237.48.195:443
44.209.166.148:443
192.3.39.166:7788
39.100.73.161:443
45.155.54.29:80
64.94.84.219:443
20.5.43.62:80
192.241.162.4:443
121.36.53.239:8080
23.95.44.80:40843
66.42.60.7:443
45.67.35.57:443