Cobalt on the weekends
One IP to 250 IoC - The Power of Pivoting
As most people do on their weekends, I was reviewing my previous Cobalt Strike hunting rules in order to refine and update them. Started poking around and pivoting which led to many new IoC.
Starting Point & Data Collection
My starting point was the following domain, hosted on the IP 83.147,255.133
sladkiepopki,help
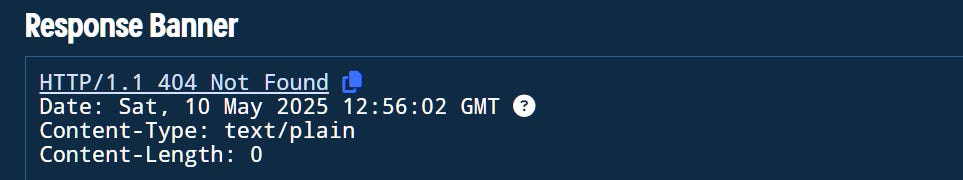
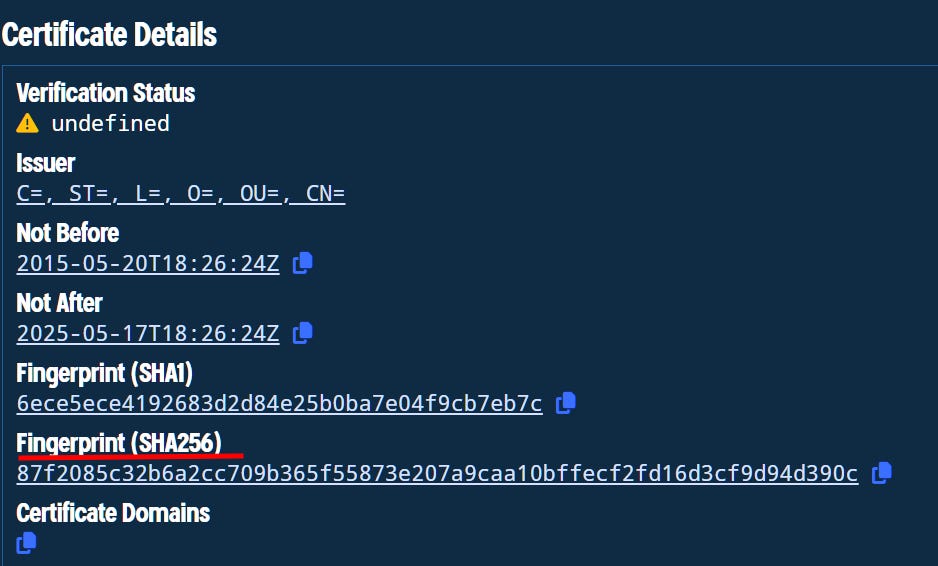
83.147.255.133Using Validin to review the hosted domain, we can see it’s only 3 month old and it’s using a self signed certificate, which in combination with our header details and JARM can be used as a first pivot. To keep our findings fresh, we’ll adjust our rules to look for results in the last 10-15 days.
Our first search returns around 400 results, mainly true positives. Interestingly enough, upon reviewing the results I noticed that the same certificate was present on every true positive result. Before moving into the analysis I think it’s best if we include these finding in the data pool as well to expand our search and results.
So now we have our 2 rules :
Rule #1 → Header Hash & Jarm
Rule #2 → Cert Hash + Header Hash (covering multiple JARM)
Our new alerts generate around 300 unique IPs and Domains. Let’s start our analysis by grouping the findings by provider.
Now that we have our main ASN clusters we can move on to building our hypothesis.
ASN Reuse Hypothesis
We all know that many threat actors provision multiple instances in the same AS in the sake of convenience, so we’ll try to take advantage of that.
AS45753 - Netsec Limited
Starting with Netsec Limited and armed with our previous findings, we can expand on our rules based on the hypothesis of AS reuse.
The IPs we had previously identified all share the same header/banner hash, cert fingerprint and AS, so by tweaking our rule a little to only include AS4573 and removing the very narrow banner focus, we get more results (5 new IPs) that match our header and certificate paterns.
Reviewing the new group of IPs (Group B) reveals an additional JARM which we can use in combination with our header/banner hashes to further expand our results.
As expected we get some duplicate results (removed from the list) but we also found 7 new entries matching our criteria and a group of IPs on 1 AS (AS36352 HostPapa)
# AS36351 HostPapa
192.1227.128.8
192.210.206.196
108.174.50.172
This group of IPs seems to be impersonating Cloudflare and Microsoft self signed certificates to improve their look of legitimacy. Further reviewing the IPs we find two more domains matching our rules, that were recently registered.
wtcx.top
centosonline.topAfter that finding, everything else was pointing back to infra that we had already identified so I figured that we can’t pivot any futher from this point.
Going back to our initial findings, another AS that had a group of IPs was Digital Ocean.
AS14061 - DigitalOcean, LLC
Following the same hypothesis, we use our previous findings and narrow down on the specific AS while removing the JARM fingerprints to uncover addtional infra and expand our search.
Our first try, using ASN + Headers returns more 1.5K results with many false positives so we’ll have to add more filters to refine the rule.
For this, we’ll be using the host banner, reducing the results to around 50 unique entries on the DigitalOcean ASN.
This search allows us to grab more information from hosts like additional JARM fingerprints that we can use to pivot further.
The JARM in combination with our previously identified headers can help us identify additional Cobalt Strike instances.
JARM Pivot - Censys
Moving over to Cesnys, we get 240 results if we use only our unique headers since the generic header rule covers multiple JARM fingerprints.
However, if we add the JARM fingerprint we got from our last pivot, the results drop to 13 new IPs.
The new IPs are mainly concetrated in the AS45090 TENCENT-NET-AP Shenzhen Tencent Computer Systems Company Limited, bringing our investigation to a full cyrcle.
The End
There are many threads that we didn’t follow like for example the 240 results covering multiple JARM or the Alibaba IP cluster but I think this investigation and pivoting can keep going forever, so I’ll stop here and maybe do a part 2.
In conclusion, we started with one domain/IP and finished our investigation with around 250 IoC (some already reported, some new) which shows the power of pivoting.
As always, I hope you are all doing well. Feel free to reach out if you want the full hunting rules or addtional info.
Thanks, take care!