Christmas Tycoon
Tales from the phishing factory with over 1.9K domains
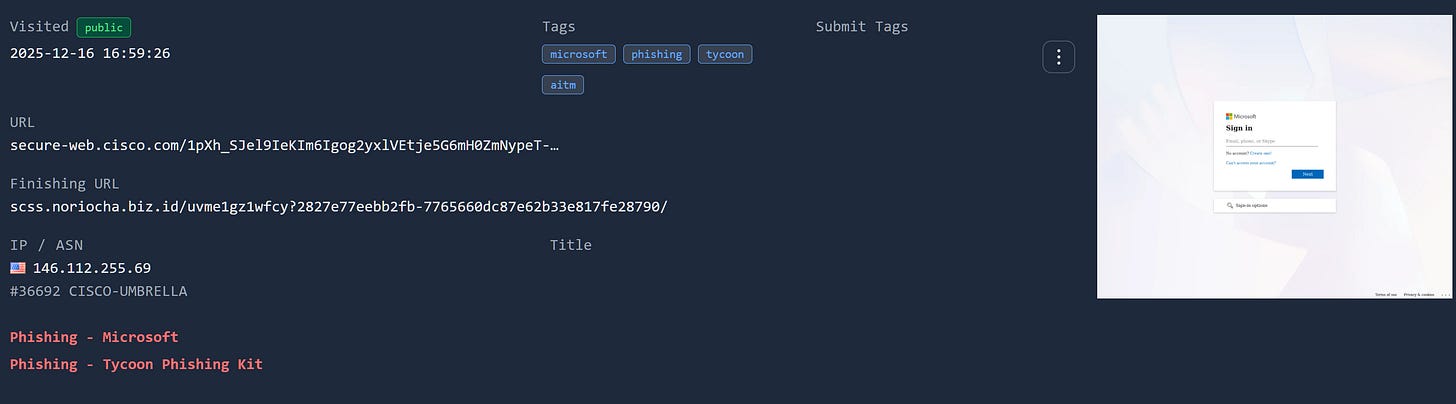
This investigation started from a phishing attempt. A compromised account sent a phishing email, containing a URL using Cisco Secure Email link to bypass security controls.
The link redirected to kdc[.]lk/office which in turn redirected to the credential harvesting site scss.noriocha.biz[.]id/<unique_id> which UrlQuery reports as the Tycoon phishing kit. Not surprising since based on AnyRun’s trend reporting, Tycoon is the number one malware family atm.
https://secure-web.cisco.com/1pXh...G0R_BE/https%3A%2F%2Fkdc.lk%2Foffice%2FHypothesis
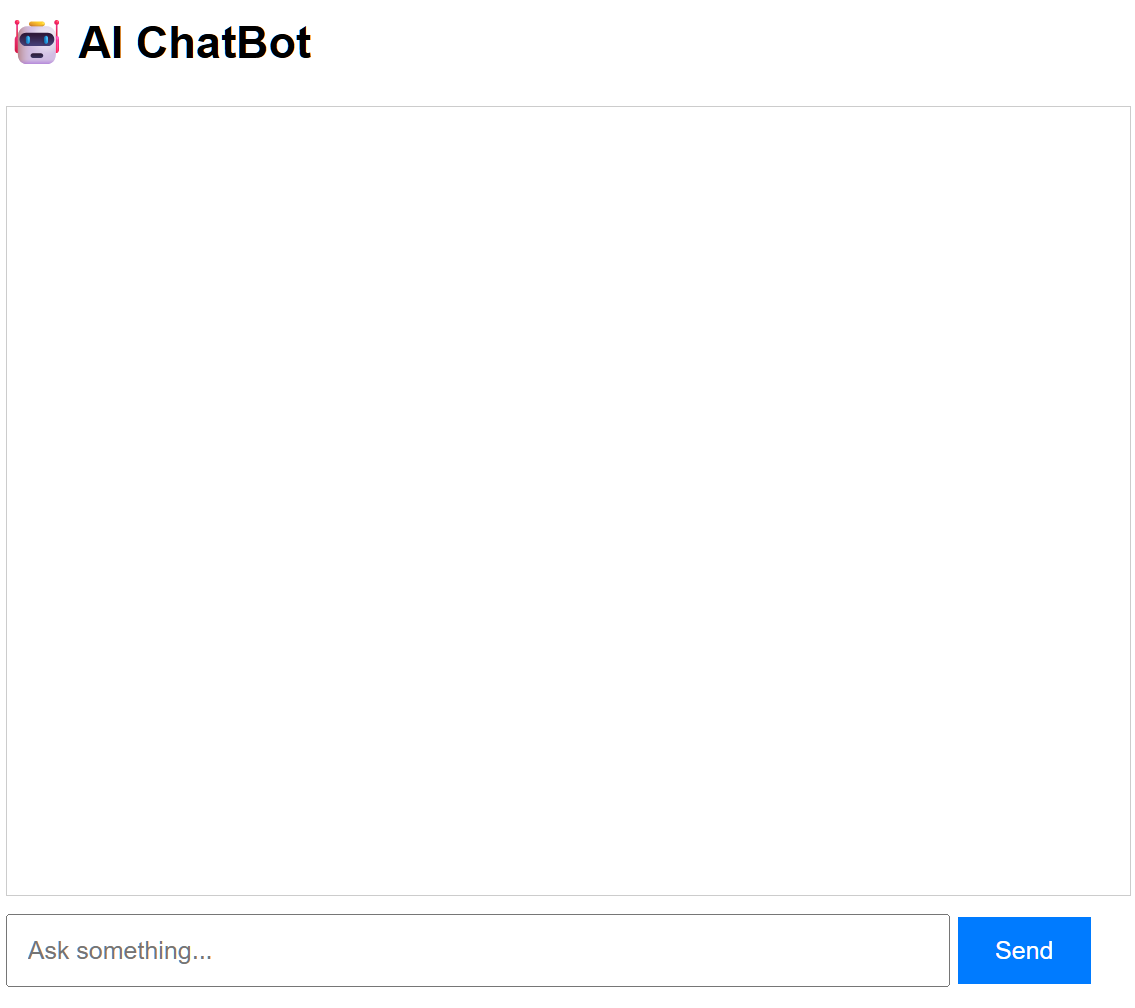
Interestingly, if you try to visit the site without the redirection ID, you’ll find an AI chatbot. This provides a somewhat unique fingerprint that we can use to pivot and discover more domains and infra related to Tycoon Phishing kit.
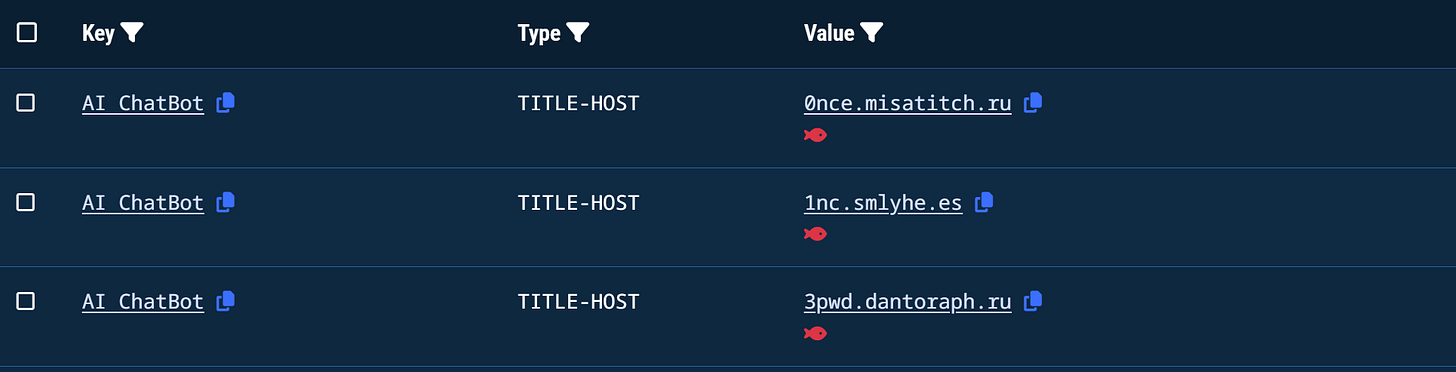
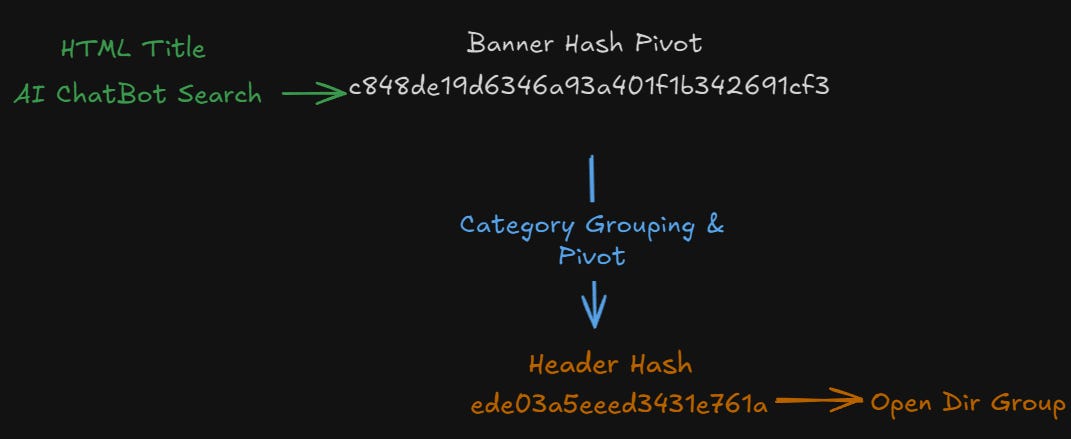
scss.noriocha.biz[.]idHaving this info on our hands, we can get some quick wins by searching for the HTML title in Validin. Sure enough, we get our first batch of indicators, proving our hypothesis.
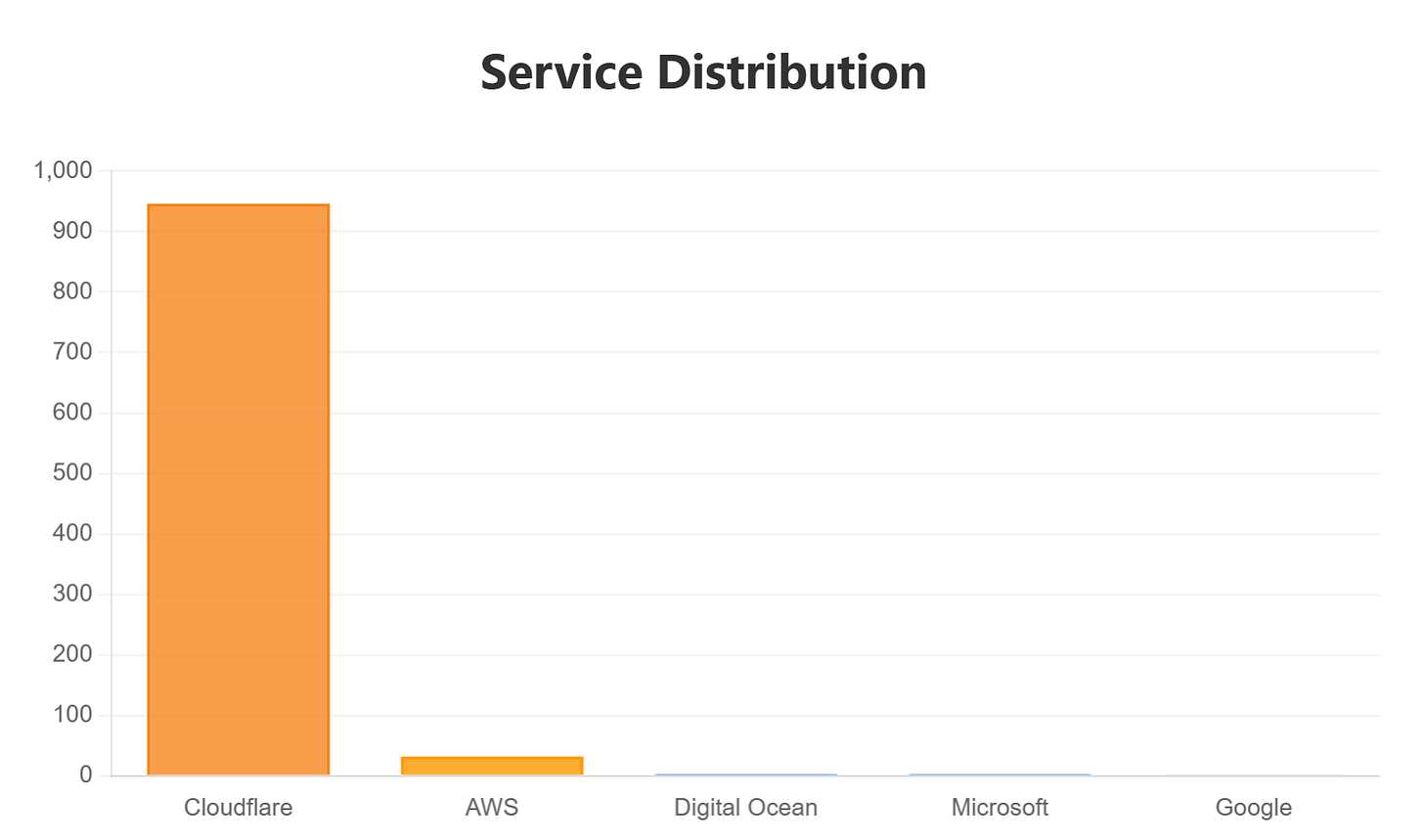
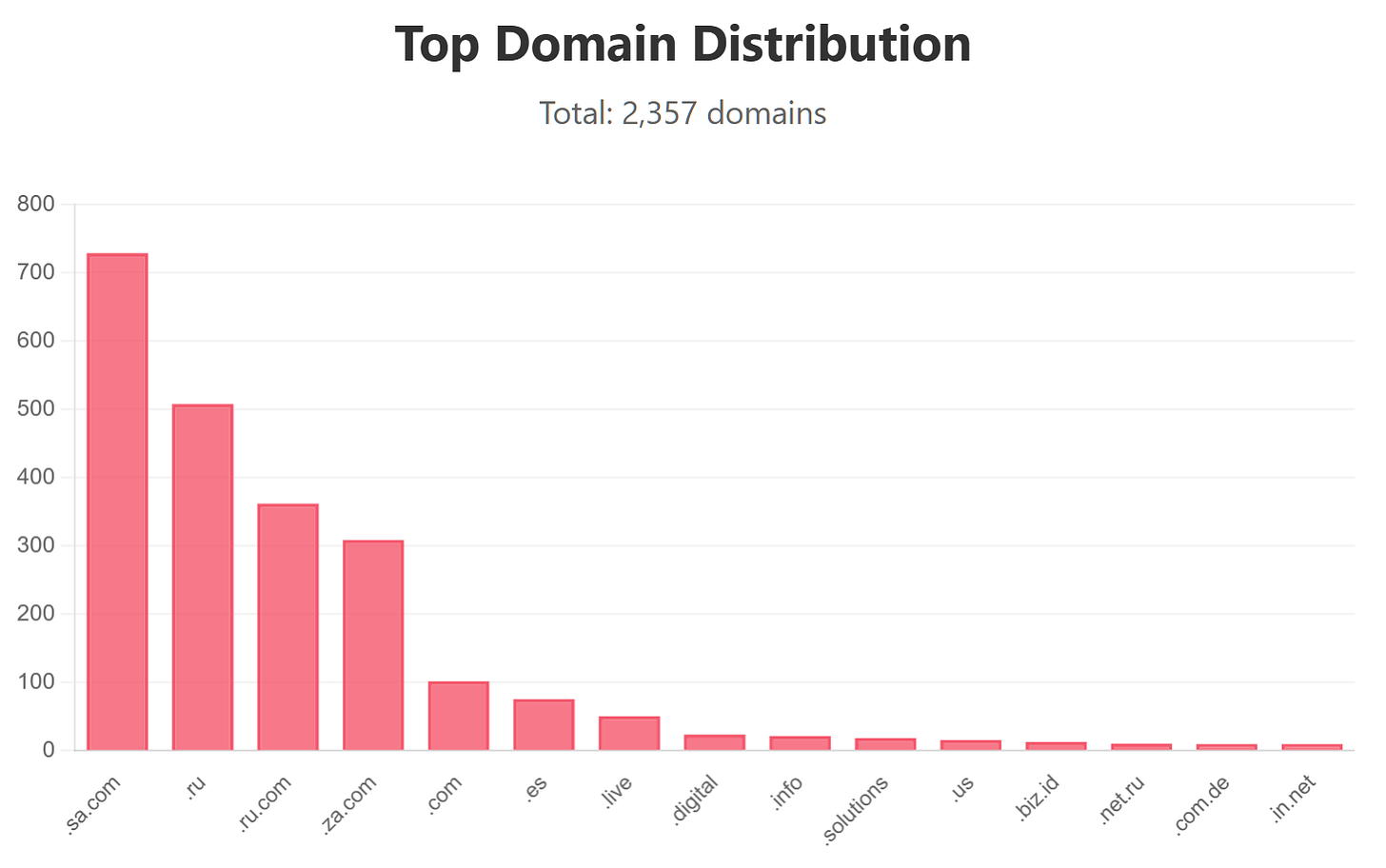
Our initial search returned almost 3.5K results (around 2.5K domains and 1K IPs), so let’s group them to better understand what we are working with. First, we’ll remove the IPs from our results. Since all of the domains are hosted in cloud hosting providers and CDNs, this information doesn’t add any value.
Next, we’ll only include active domains ; last seen within the last 7 days (of this writing) and group our domains based on their TLD. As you can see, we have high concentration on sa.com and .ru TLD. Removing the subdomains from the list leaves us with 756 unique entries.
Banner Hash Pivot
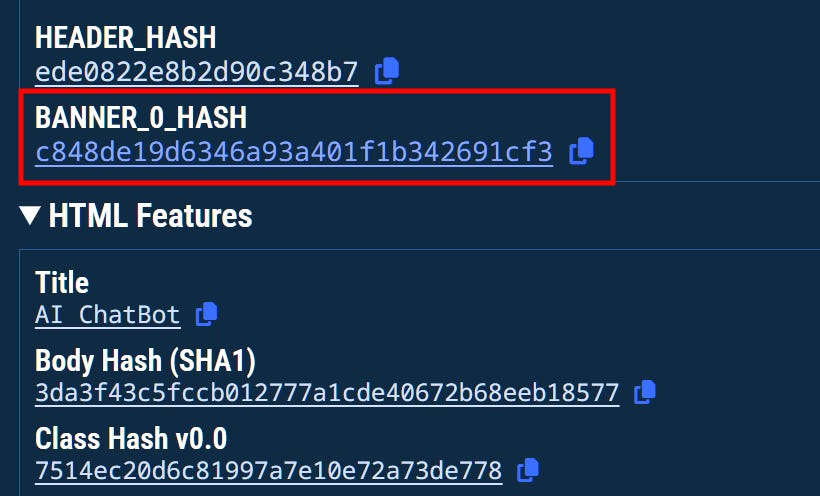
Now that we have a list of true positive results, we can review our findings and identify common characteristics and patterns. One thing all of our results have in common are their Banner Hash, so we can use it as a pivoting point to expand our search.
Following the same steps as before, we remove the subdomains and duplicates from our original list leaving us with 418 new phishing domains. Our new domains share another interesting characteristic, some very distinct HTML titles.
Grouping the Campaigns
All of the newly discovered domains have one of the following 5 HTML titles, making it easy to group the phishing campaigns.
*You can use any of the following titles in Validin to pivot to additional domains*
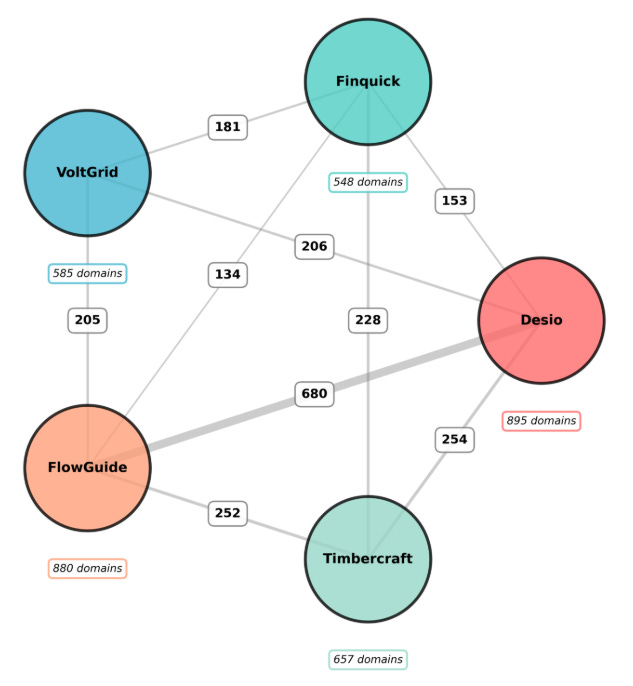
Finquick - Finance & Payments SaaS Landing (HTML) (548 Domains)
Desio Copilot – AI Workspace (895 Domains)
VoltGrid | Clean Energy Solutions (585 Domains)
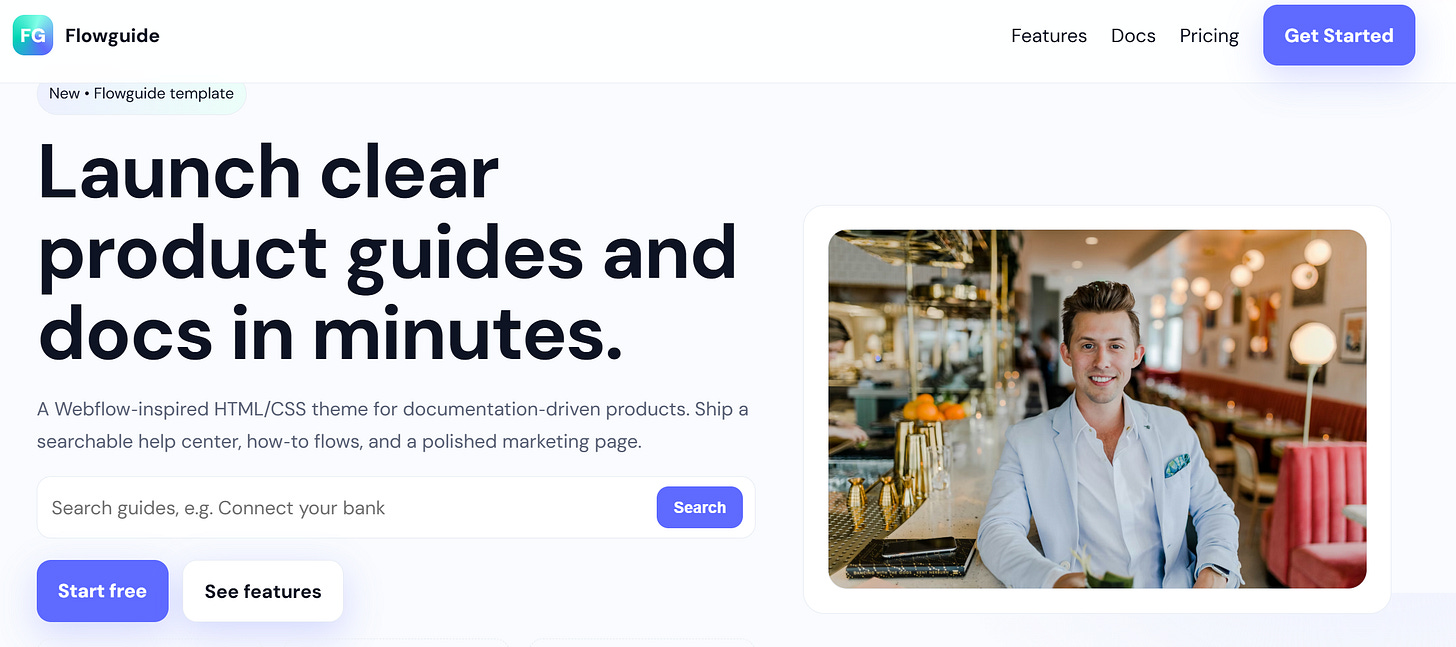
Flowguide – Product Guide & Docs (HTML) (880 Domains)
TimberCraft | Premium Wood Construction (657 Domains)
By visiting the sites, we can quickly see the same generic text and images being reused.
Further analyzing the domains/categories we see a lot of overlap and redirections between the different themes, especially between Desio and Flowguide while Timbercraft has the least overlaps (for now).
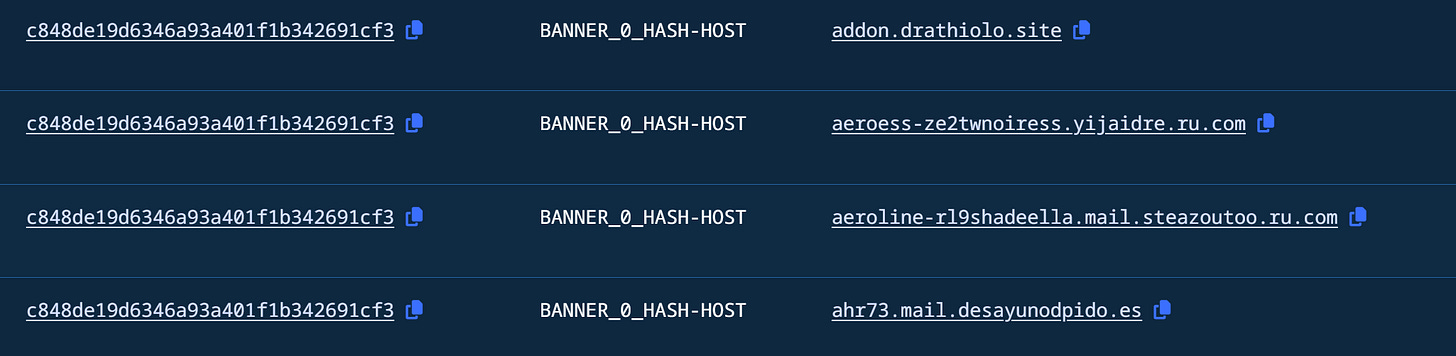
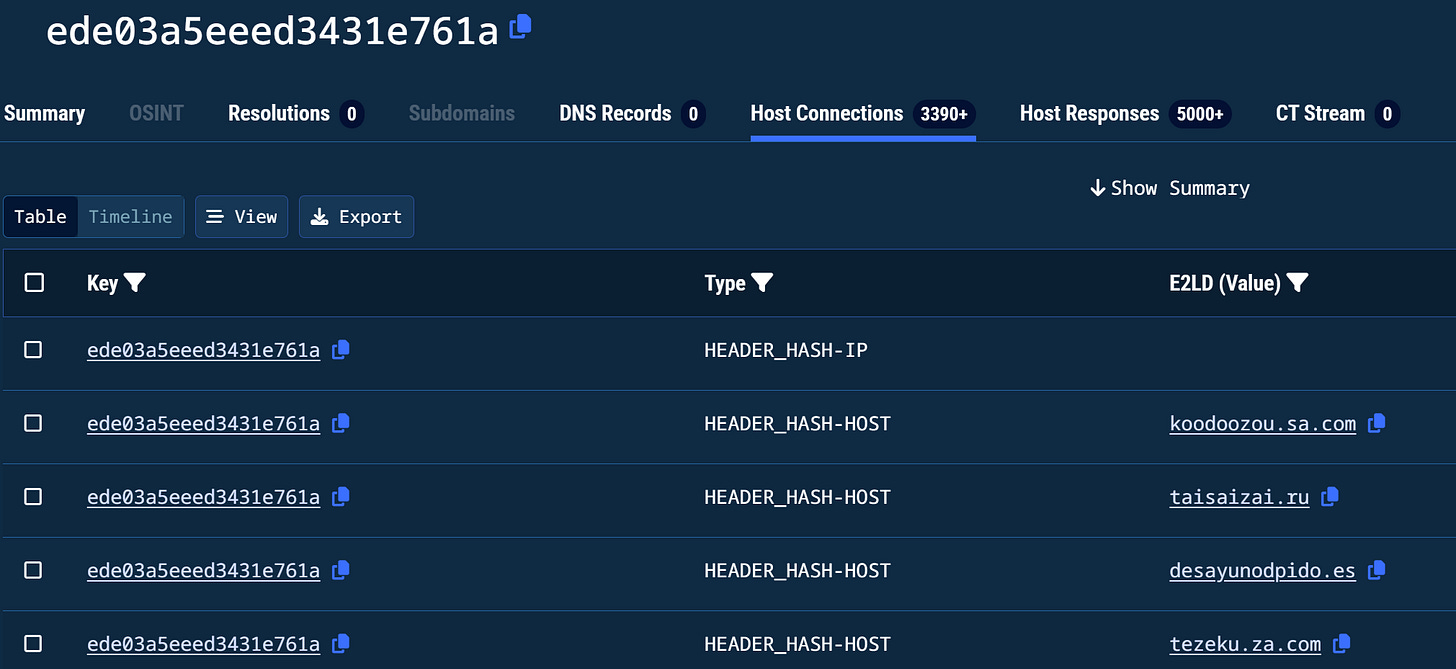
Header Hash
For our final pivot, we’ll focus on a few header hashes that kept appearing over various domains. This pivot leads to another great pool of malicious domains containing over 850.
This list contains another interesting finding, a group of around 30 open directory sites that are probably worth a closer investigation.
Conclusion
After writing this post, I went back to the original credential harvesting URL but I got redirected to one of the generic templates mentioned above. This leads me to believe that the use of this generic landing pages is being utilized when the campaign is inactive or paused.
In addition, the heavy use of this 5 generic templates seems like an automated deployment infrastructure that is sacrificing uniqueness for volume which is further supported by the heavy use of DGA.
The volume of the findings speaks for itself. It all started with a single domain and led to over 1900 unique domains purely based on infra fingerprinting.
I’ll probably follow up on these findings at some point ; but for the time being, that’s all.
Hope you are doing well and wish you health, personal and professional development for the new year.
Thank you for all the support, kind words and feedback during this year, it means a lot.
Take care!