C2 powered by Steam
Gaming the system - Infostealers user profile strategy
It all started with a hash on Malware Bazaar.
User “JOI” reported it early November and the community jumped on it. Pretty quick it was identified as the Vidar malware.
Vidar is an infostealer malware family that has been actively involved in various cybercrime campaigns through 2024. This malware primarily targets sensitive information, including login credentials and financial data using techniques like DLL side loading and leveraging compromised or fake software distribution channels. It has been observed in conjunction with other malware like Lumma and StealC.
sha256: a4e0fd3483e26b4c0dfda5b2c1cb89571e06a8162e88b8a47a810a4b38934b1f
Vidar malware is not exactly news and a different variant is not very interesting. The interesting part was the relations reported in VT.
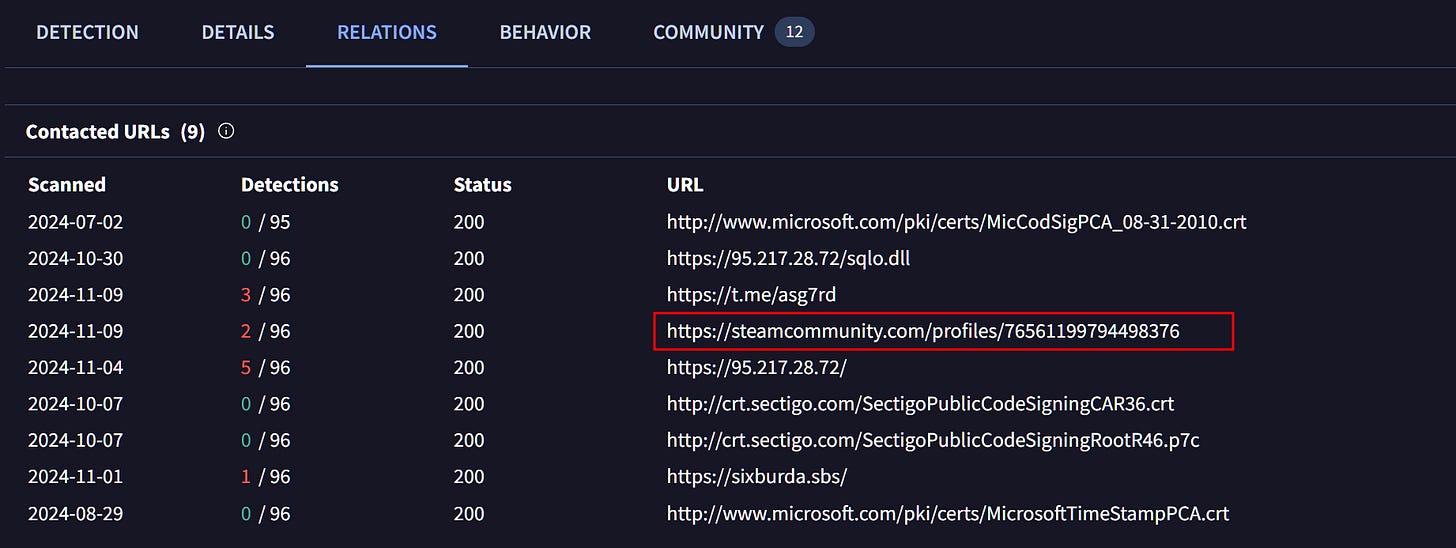
What caught my eye was a Steam community user account. This has been previously reported[1] [2] and this techniques seem to be associated with infostealers in particular but I wanted to follow up the lead regardless.
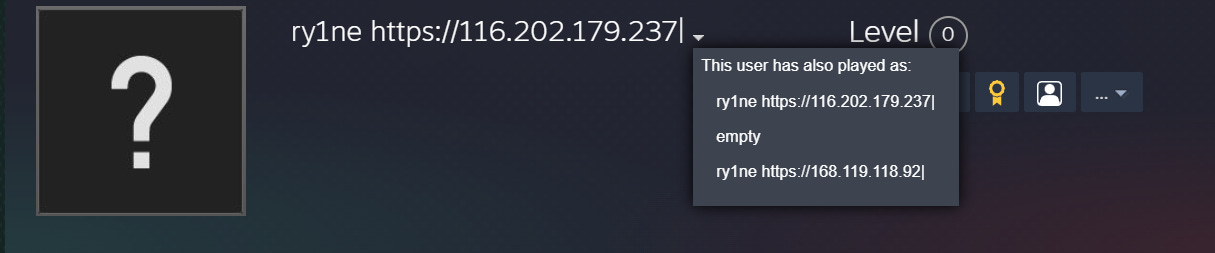
As you can see in the image below, this user account has used multiple usernames including various IPs.
All of the usernames follow the same structure and seem to user “https” to try and blend with legitimate traffic and end with a pipe symbol “|” which to me indicates a configuration file syntax where the pipe marks the end of an entry.
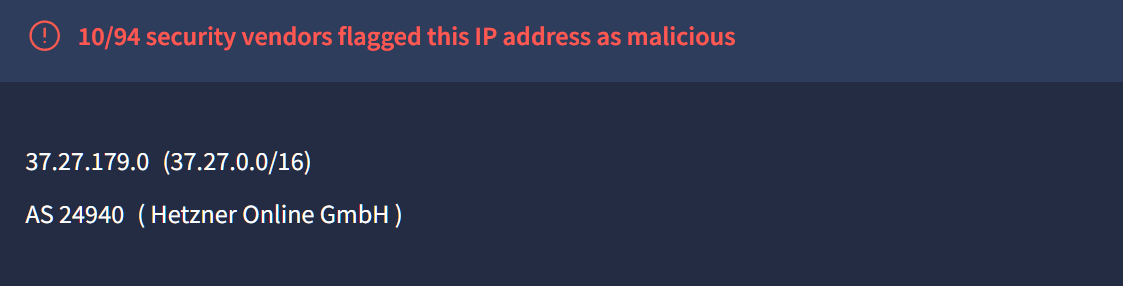
The IPs have been reported as malicious/suspicious and marked as Vidar infrastructure.
Most of the URLs are down but 2 seem to be working (at the time of writing this) and apply some sort of filtering which redirects to google start page.
https://65.109.243[.]177
https://37.27.179[.]0
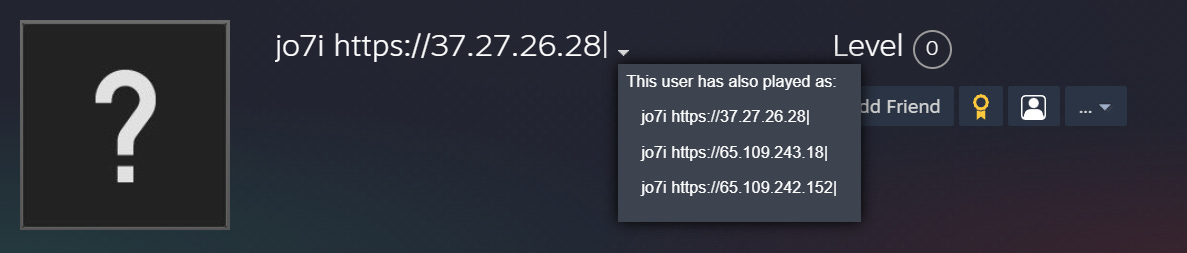
Naturally, I looked for similar entries and was not disappointed. Additional usernames containing IPs from the same netblock (AS24940) exist following similar pattern.
This is only the tip of the iceberg. Doing a quick search using the first two octets of some of the IP blocks of the AS24940 returned more results.
As you can understand this is a never ending rabbit hole and it was impossible to proceed manually so I figured, let’s try to automate this task.
I grabbed a steam API key and put Claude to work, it created a script that would go through usernames and look for similar structures. Unfortunately the API is limited to 100K requests per day which is a blocker since Steam has million of users.
I took a different approach -a long shot- , reached out to steam to share my findings and asked them if they can perform a search for “https://x.x.x.x” in their users database and share the results. I am sure they won’t do it but it was worth a try.
That’s all folks, if anybody has a better idea on how to approach this and likes to work on this, I would be more than happy to do it.
Quick Update
As I told you, I had contacted Steam to try and get their help. As expected they brushed me off.