Bulletproof Hosting Hunt
Connecting the dots from Lumma to Qwins Ltd (ASN 213702)
It all started with a simple follow up on another Lumma infection. I wanted to find and automate a quick way to get hunting leads for infra that is not hidden behind CDNs but I think I might have found a Bulletproof hosting provider.
Lumma continues to be in the top 5 malware families [1] [2] , which means high sample availability on malware reporting platforms and a great starting point for a hunt! Starting from the latest Lumma samples, we can expand to additional malicious infrastructure, including phishing, impersonation mininng and various malware.
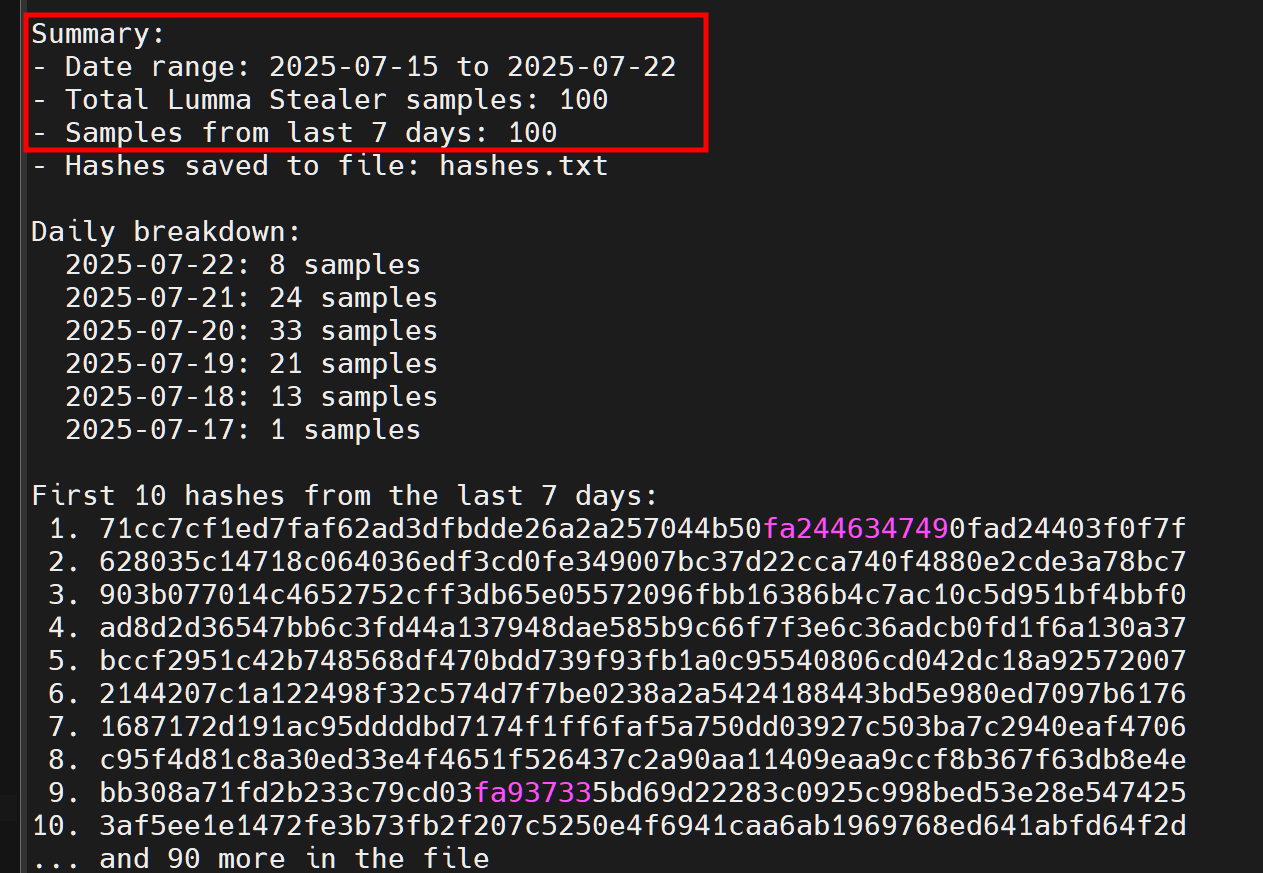
Using abuse.ch API to retrieve samples from the last week (of this writing), returns 100 results between 15-22/7. With the latest hashes in hand we can start our analysis.
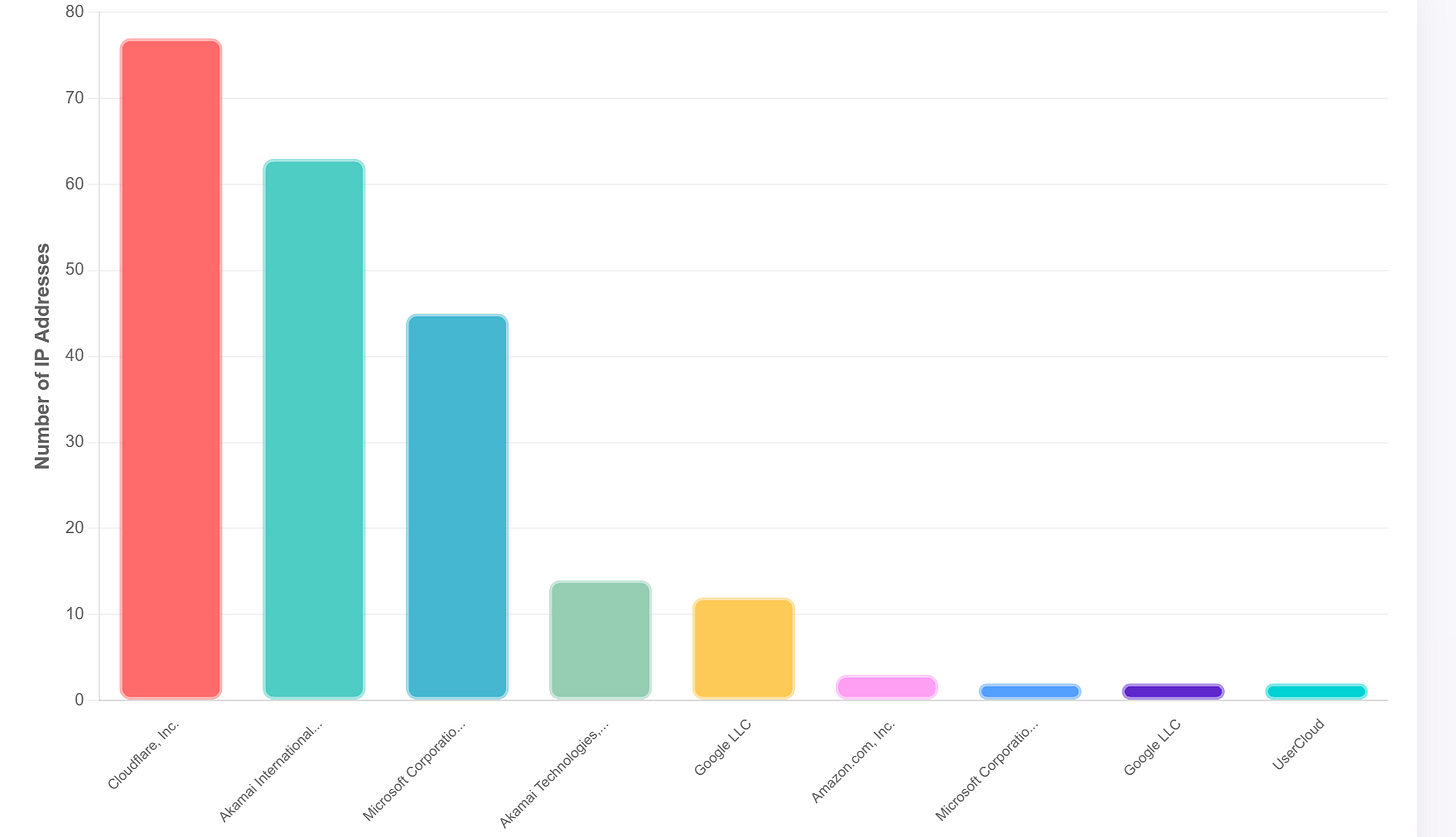
First, let’s grab any communicating IPs. Using VT API we can see that the malicious files are communicating with 292 IPs. Now that we have our IPs, we’ll group them and try to filter out dead end pivots. What I mean by that is, since most of the domains associated with Lumma are usually hidden behind CDN like Cloudflare, Akamai etc, we’ll filter those out as it’s nearly impossible to pivot.
After filtering the IPs and ASN, we are left with 10 unique IPs spread across 10 unique ASN so there is no immediate pattern in the grouping.
141.98.6.34 - AS213702, Qwins LTD
185.215.113.51 - AS51381, (ELITETEAM-PEERING-AZ1 1337TEAM PEERING AZ1)
144.172.115.212 - AS14956, ROUTERHOSTING
167.160.161.12 - AS214943, Railnet LLC
104.251.123.89 - AS14315, 1GSERVERS, LLC
146.70.100.103 - AS9009, M247 Europe SRL
176.46.152.39 - AS214351, FEMO IT SOLUTIONS LIMITED
198.54.117.242 - AS22612, Namecheap, Inc.
45.134.26.137 - AS198953 ,Proton66 OOO
92.38.145.145 - AS199524, G-Core Labs S.A.Qwins LTD: Infostealers, Trojans & Impresonations
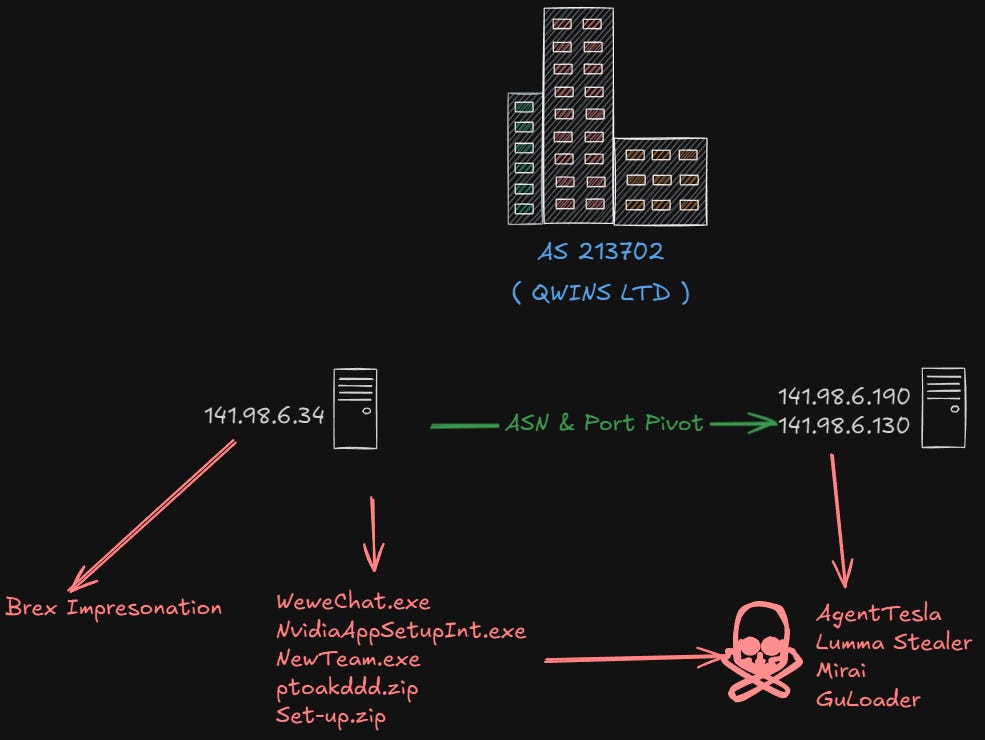
Starting with 141.98.6.34 part of the AS213702 owned by QWINS LTD we find a very interesting Russian operated hosting provider offering VPS and dedicated servers at very low prices (starting around 2$ per month), while also offering services directly through their Telegram bot.
Servers can be deployed in Russia, Germany, Finland, Netherlands, Estonia
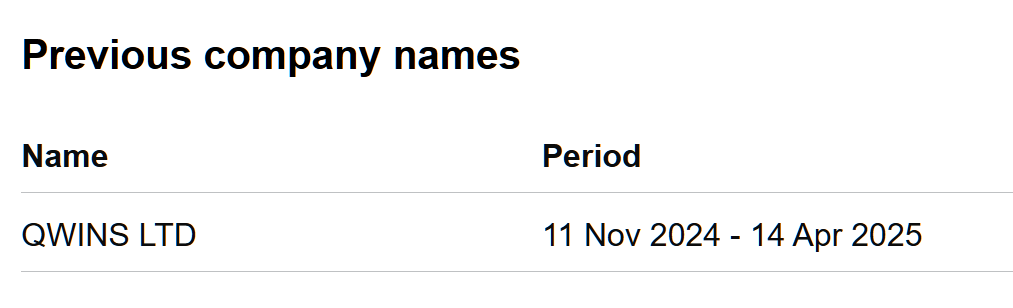
The company was incorporated on 11 November 2024 in the UK and had “Kristina Konstantinova” as acting director from the date of incorporation until April 2025 (6 months exactly). The company domain was registered one year earlier on Nov 2023
The company was renamed on April 2025 to “QUALITY IT NETWORK SOLUTIONS LIMITED”.
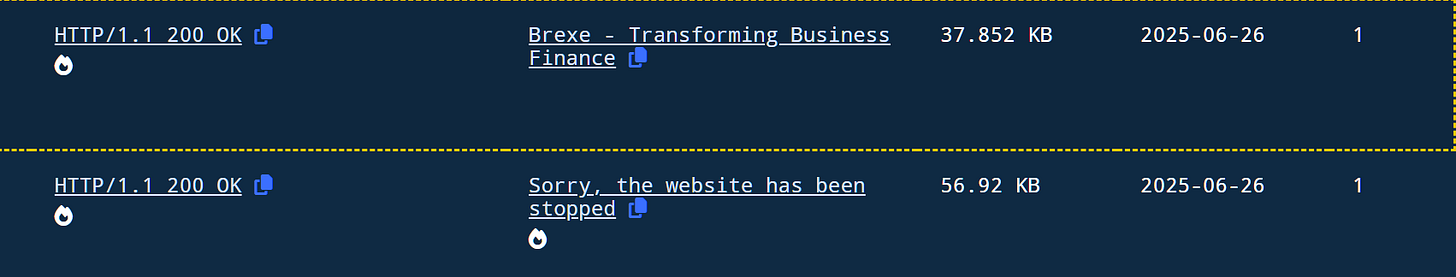
Reviewing the aforementioned IP, we can see that around the end of June, a site impersonating “Brex” financial services was hosted on it.
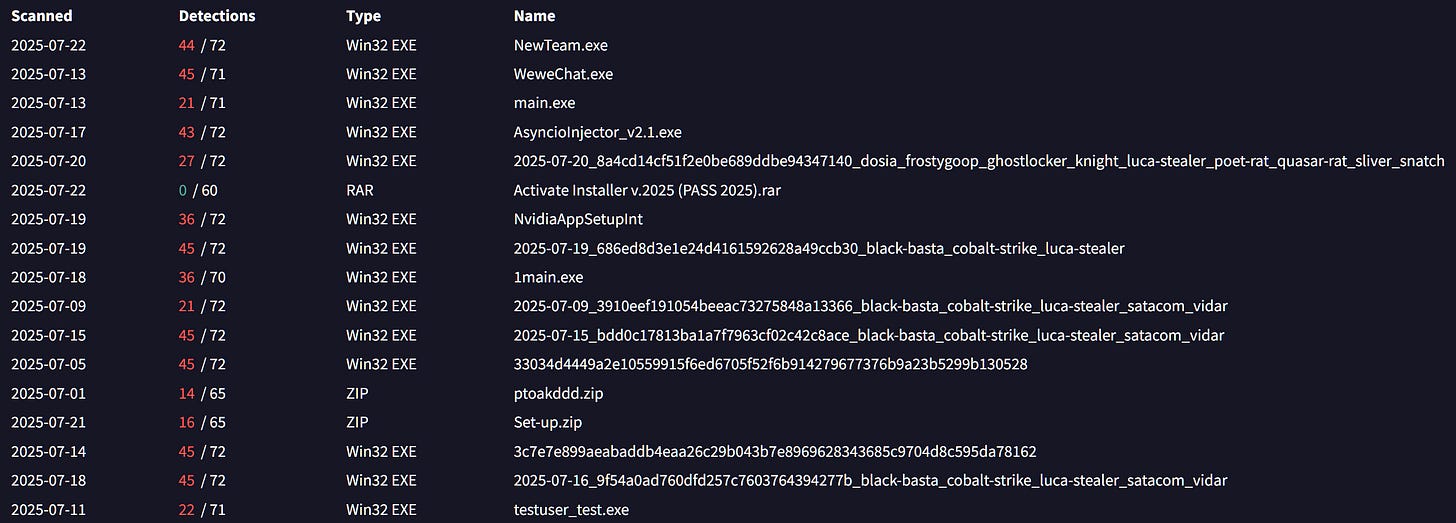
In addition, we see many malicious files (exe,zip,rar,etc.), associated mainly with infostealers and trojans recently communicating with the same IP meaning it is used by either multiple threat actors or a single actor involved in many attacks.
This hosting provider seems promising, so let’s spend some more time investigating the ASN before pivoting to other networks.
Hypothesis Creation
Our hypothesis is that ASN 213702 is being used by threat actors and by now, we can say with high confidence that the IP 141.98.6.34 is hosting malicious payloads and is used as C2 infrastructure.
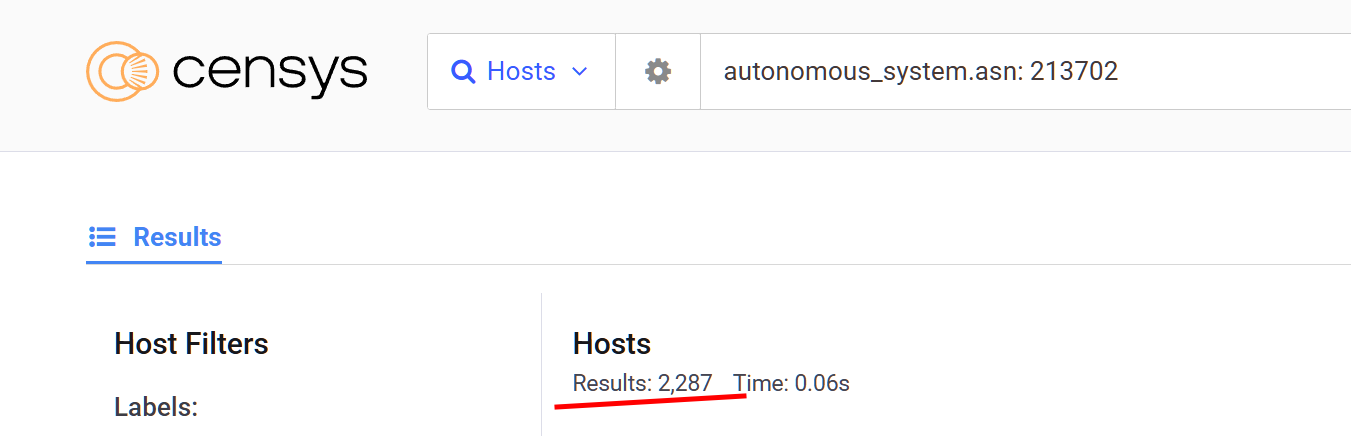
Moving over to Censys, we see that there are about 2.3K hosts in that ASN.
ASN & Ports Pivot
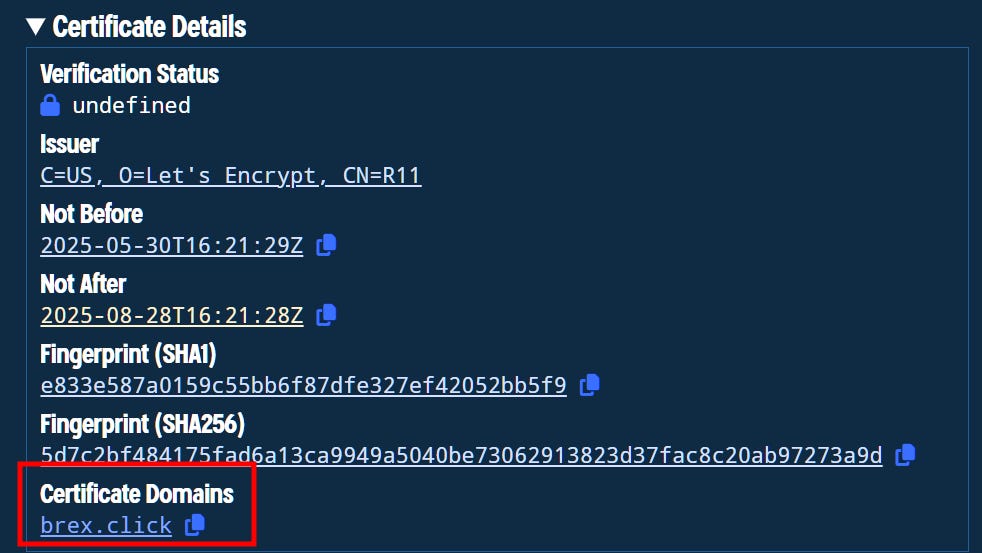
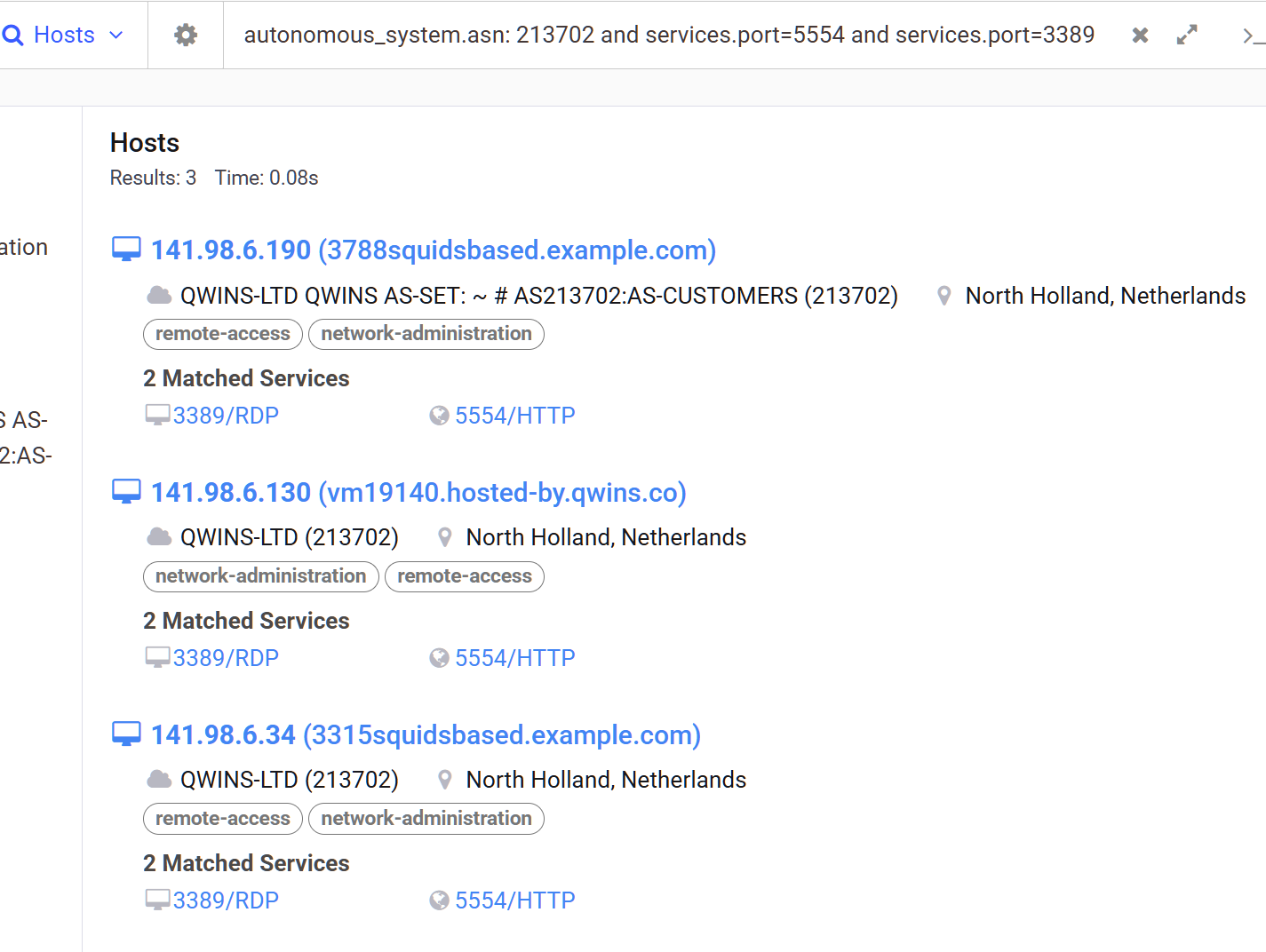
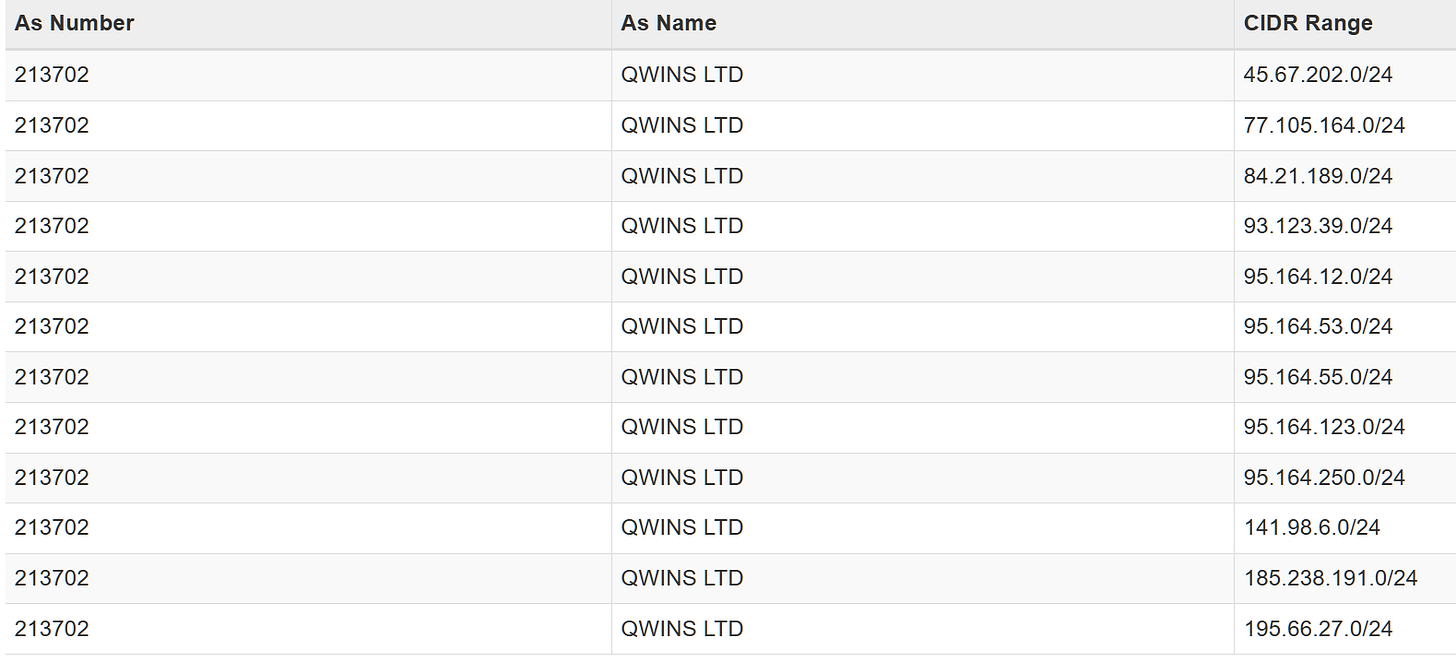
We can narrow it down by filtering for hosts that match the attributes of our IP, which leaves us with just 3 hosts which also seem to share the same self signed cert.
autonomous_system.asn: 213702 and services.port=5554 and services.port=3389141.98.6.190
141.98.6.130
141.98.6.34The above IPs have been linked with malware, specifically with trojans and loaders and infostealers (makoob, guloader, agenttesla) and have been active around the same time, in combination with the services and self signed certificates, I would say it’s safe to cluster those 3 IPs together.
SQL Website Pivot
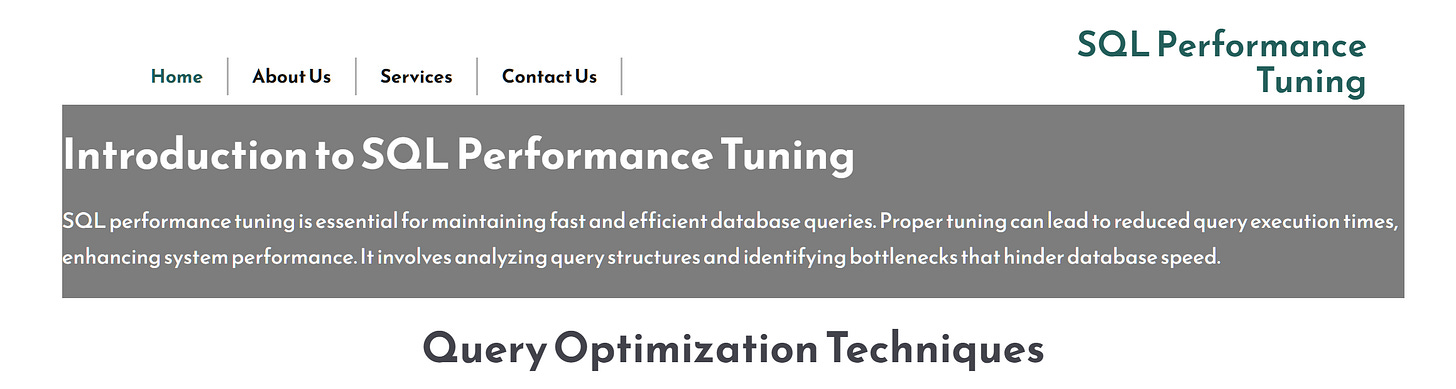
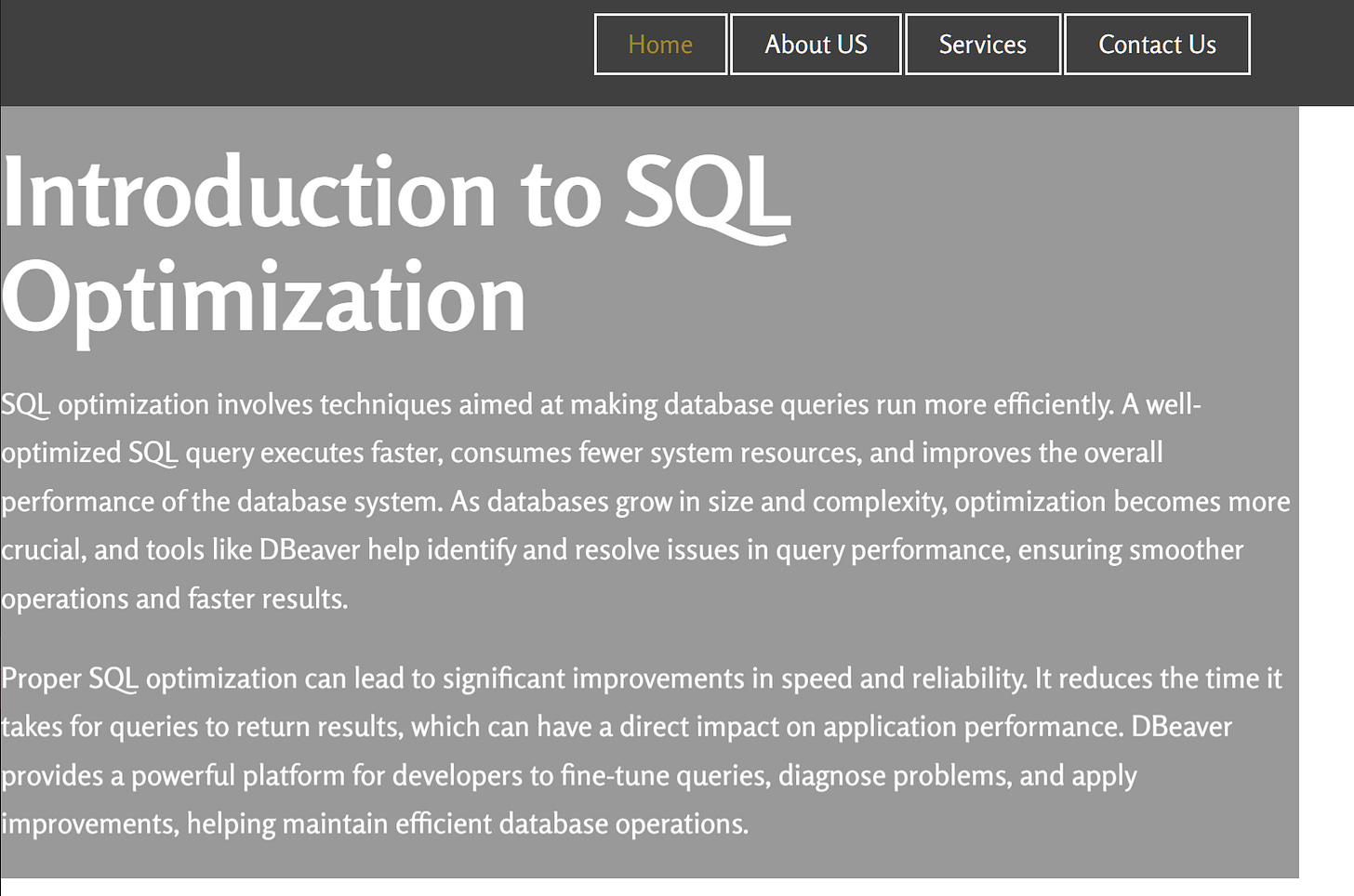
Our next pivot comes from domains hosted on our newly found cluster that trying to impersonate the database tool DBeaver.
”dbeaver.it[.]com” & “dbeaver-pro.[s]ite” are hosted on that cluster and they claim to perform SQL perfomance optimization.
dbeaver-pro[.]site leads us to our next IP target 141.98.6.81, this IP has association mainly with botnets (mirai, quackbot, qbot, condi and more).
ASN 213702 Analysis
It’s clear now, that many malicious activities take place in this ASN, since it’s a relatively small network hosting around 3K IPs, let’s try to group the malicious activity per network and map out in more detail what kind of activities originate from these networks.
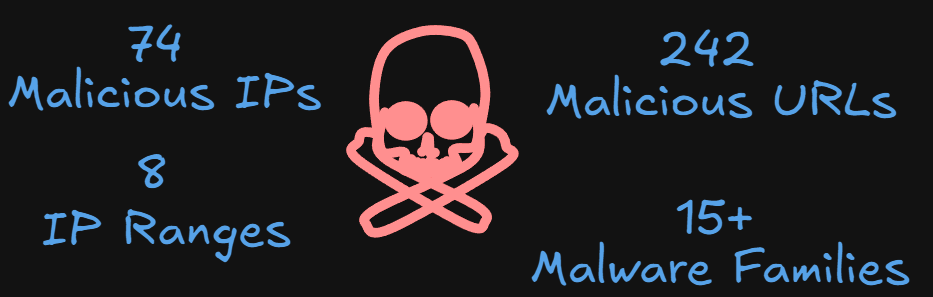
To keep the IoC as fresh as possible, I only focused on the last 30 days. Grabbed all the hashes, IPs and URLs that were flagged as malicious on these networks and analyzed the results.
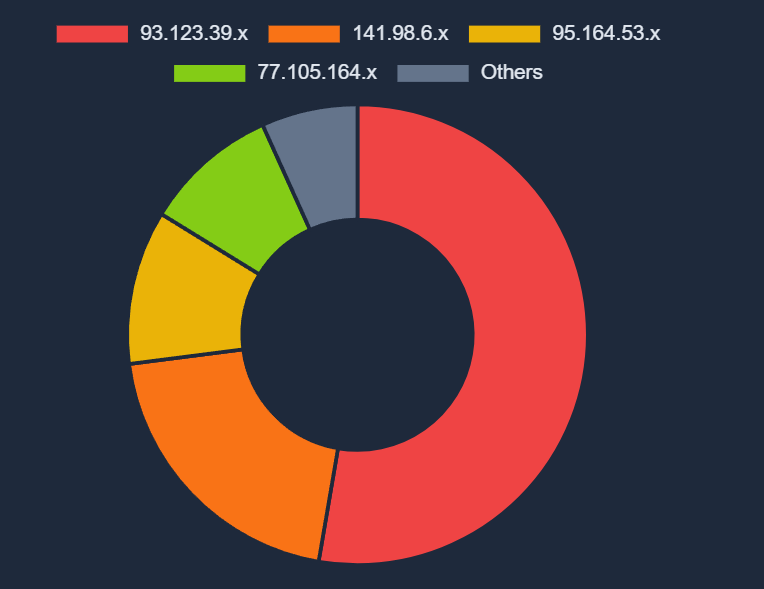
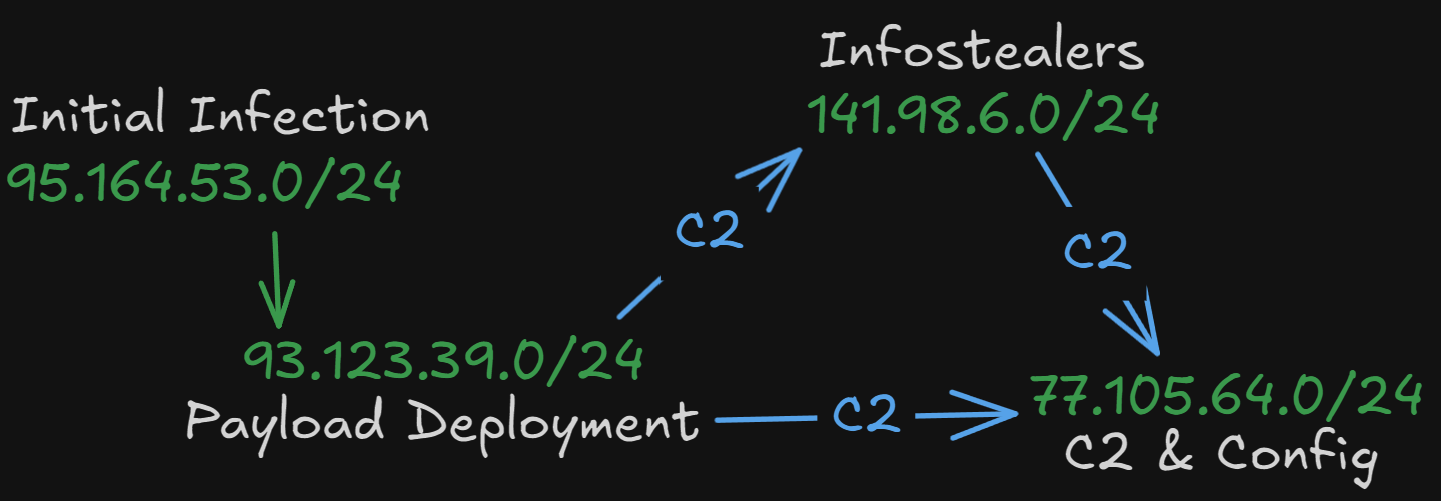
Most of the activity is originating from networks 93.123.39.0/24 and 141.98.6.0/24
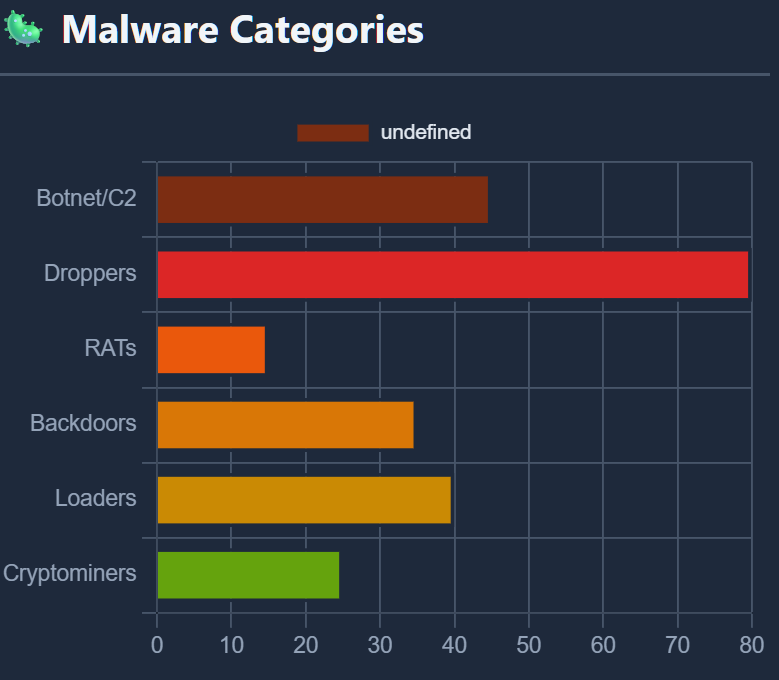
Based on the hashes found communicating and/or hosted on the networks, most of the malware is categorized as Droppers but as you can see, there is a huge variety of malware like botnet, rats, cryptominers, infostealers, targeting multiple architectures (Windows/Linux x86/x86_64, ARM, Mips). Specifically, I found a big concentration on the following malware.
Amadey Botnet
Mirai Botnet
Zapchast Trojan
Lumma
Vidar
DarkGate
We previously found that phishing websites and social engineering originated from the networks too, which is consistent with the initial access via document droppers (pdf, doc,zip).
Malware Activity Clustering Analysis
Further reviewing the findings leads to additional clustering based on the malware communication.
93.123.39.0/24 - DDoS & Botnets
In this network, we find 39 malicious IPs spreading over than 120 payloads mainly associated with botnets, DDoS infra and C2 usually on port 666
141.98.6.0/24 Infostealers
We can find around 15 flagged IPs, hosting over 45 samples. Mainly infostealers like Amadey, Lumma and Vidar and probably C2 infra.
95.164.53.0/24 Malware Distribution
Found many files that look like initial payload distribution and malware hosting. It could be serving as the entry point for infection chains, hosting document droppers, and first stage loaders.
77.105.164.0/24 C2, Config & Backup
The above findings can be somewhat verified if we follow the flow of the malicious files/hashes. We can see that many droppers on the 95.164 network lead to payloads on the 93.123 network and many stealers from the 141.98 communicate the 77.105 network which I interpreted as C2 communication and data exfil.
Wrapping Up
To summarize, I think we found a very interesting hosting provider that requires further investigation, I can’t say with certainty if this is or isn’t a BPH but I can definitely say that there are some troubling signs.
In any case, this is all I have for now. I will follow up on some of the leads and see what other connections might appear.
If anyone has previously worked on that please reach out.
As always, I hope you are all safe and healthy. Thanks and take care!







You started with just a few Lumma samples and ended up peeling back layers like an onion—CDNs filtered out, IPs grouped, certs matched, and boom: a suspicious hosting provider that reeks of bulletproof vibes.
Love how you connected the dots between the subnets and mapped out their roles (droppers here, C2 there, exfil over there)—it’s like watching a cybercrime ecosystem unfold in real time. And that Telegram bot + super-cheap VPS + UK shell game? Classic red flags.
Seriously great work—super detailed but still easy to follow. Thanks for sharing the hunt! Hope you catch even more in the next round. Stay sharp